USENIX Security '22: GAROTA — Advanced Root-of-Trust Architecture for Tiny Embedded Devices 🔒
Discover GAROTA, a groundbreaking generalized active root-of-trust architecture designed to enhance security in small embedded devices, presented at USENIX Security '22 by UC Irvine researchers.

USENIX
300 views • Oct 26, 2022
About this video
USENIX Security '22 - GAROTA: Generalized Active Root-Of-Trust Architecture (for Tiny Embedded Devices)
Esmerald Aliaj, University of California, Irvine; Ivan De Oliveira Nunes, Rochester Institute of Technology; Gene Tsudik, University of California, Irvine
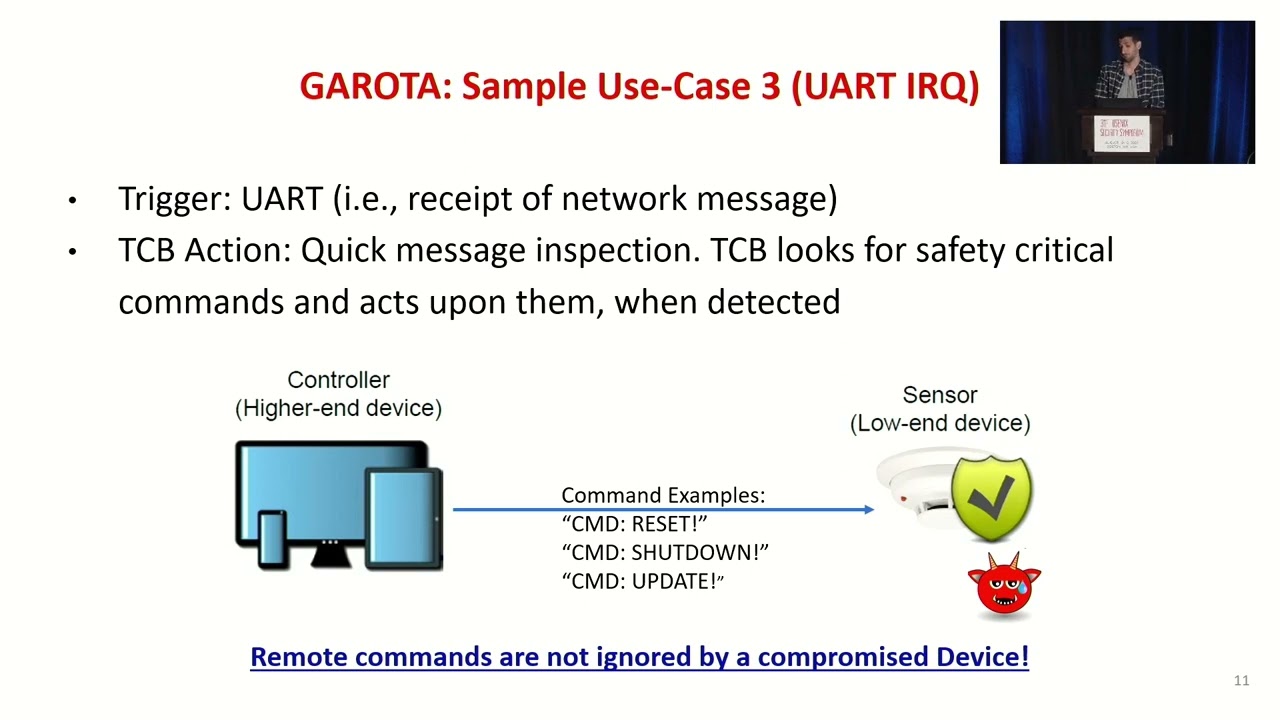
Embedded (aka smart or IoT) devices are increasingly popular and becoming ubiquitous. Unsurprisingly, they are also attractive attack targets for exploits and malware. Low-end embedded devices, designed with strict cost, size, and energy limitations, are especially challenging to secure, given their lack of resources to implement sophisticated security services, available on higher-end computing devices. To this end, several tiny Roots-of-Trust (RoTs) were proposed to enable services, such as remote verification of device's software state and run-time integrity. Such RoTs operate reactively: they can prove whether a desired action (e.g., software update or program execution) was performed on a specific device. However, they can not guarantee that a desired action will be performed, since malware controlling the device can trivially block access to the RoT by ignoring/discarding received commands and other trigger events. This is an important problem because it allows malware to effectively ""brick"" or incapacitate a potentially huge number of (possibly mission-critical) devices.Though recent work made progress in terms of incorporating more active behavior atop existing RoTs, much of it relies on extensive hardware support in the form of Trusted Execution Environments (TEEs), which are generally too costly for low-end devices. In this paper, we set out to systematically design a minimal active RoT for low-end MCU-s. We begin with three questions: (1) What functionality is required to guarantee actions in the presence of malware? (2) How to implement this efficiently? and (3) What are the security benefits of such an active RoT architecture? We then design, implement, formally verify, and evaluate GAROTA : Generalized Active Root-Of-Trust Architecture. We believe that GAROTA is the first clean-slate design of an active RoT for low-end MCU-s. We show how GAROTA guarantees that even a fully software-compromised low-end MCU performs a desired action. We demonstrate its practicality by implementing GAROTA in the context of three types of applications where actions are triggered by: sensing hardware, network events and timers. We also formally specify and verify GAROTA functionality and properties.
View the full USENIX Security '22 program at https://www.usenix.org/conference/usenixsecurity22/technical-sessions
Esmerald Aliaj, University of California, Irvine; Ivan De Oliveira Nunes, Rochester Institute of Technology; Gene Tsudik, University of California, Irvine
Embedded (aka smart or IoT) devices are increasingly popular and becoming ubiquitous. Unsurprisingly, they are also attractive attack targets for exploits and malware. Low-end embedded devices, designed with strict cost, size, and energy limitations, are especially challenging to secure, given their lack of resources to implement sophisticated security services, available on higher-end computing devices. To this end, several tiny Roots-of-Trust (RoTs) were proposed to enable services, such as remote verification of device's software state and run-time integrity. Such RoTs operate reactively: they can prove whether a desired action (e.g., software update or program execution) was performed on a specific device. However, they can not guarantee that a desired action will be performed, since malware controlling the device can trivially block access to the RoT by ignoring/discarding received commands and other trigger events. This is an important problem because it allows malware to effectively ""brick"" or incapacitate a potentially huge number of (possibly mission-critical) devices.Though recent work made progress in terms of incorporating more active behavior atop existing RoTs, much of it relies on extensive hardware support in the form of Trusted Execution Environments (TEEs), which are generally too costly for low-end devices. In this paper, we set out to systematically design a minimal active RoT for low-end MCU-s. We begin with three questions: (1) What functionality is required to guarantee actions in the presence of malware? (2) How to implement this efficiently? and (3) What are the security benefits of such an active RoT architecture? We then design, implement, formally verify, and evaluate GAROTA : Generalized Active Root-Of-Trust Architecture. We believe that GAROTA is the first clean-slate design of an active RoT for low-end MCU-s. We show how GAROTA guarantees that even a fully software-compromised low-end MCU performs a desired action. We demonstrate its practicality by implementing GAROTA in the context of three types of applications where actions are triggered by: sensing hardware, network events and timers. We also formally specify and verify GAROTA functionality and properties.
View the full USENIX Security '22 program at https://www.usenix.org/conference/usenixsecurity22/technical-sessions
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
300
Likes
3
Duration
13:05
Published
Oct 26, 2022
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.