USENIX Security '16 - The Cut-and-Choose Game and Its Application to Cryptographic Protocols
This paper by Ruiyu Zhu, Yan Huang, and Jonathan Katz explores the cut-and-choose game and its implications for cryptographic protocols, presenting novel insights and applications discussed at USENIX Security 2016.

USENIX
186 views • Dec 3, 2021
About this video
The Cut-and-Choose Game and Its Application to Cryptographic Protocols
Ruiyu Zhu and Yan Huang, Indiana University; Jonathan Katz, University of Maryland; Abhi Shelat, Northeastern University
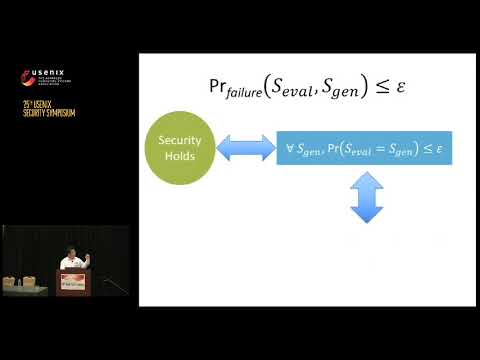
The cut-and-choose technique plays a fundamental role in cryptographic-protocol design, especially for secure two-party computation in the malicious model. The basic idea is that one party constructs n versions of a message in a protocol (e.g., garbled circuits); the other party randomly checks some of them and uses the rest of them in the protocol. Most existing uses of cut-and-choose fix in advance the number of objects to be checked and in optimizing this parameter they fail to recognize the fact that checking and evaluating may have dramatically different costs.
In this paper, we consider a refined cost model and formalize the cut-and-choose parameter selection problem as a constrained optimization problem. We analyze “cut-and-choose games” and show equilibrium strategies for the parties in these games. We then show how our methodology can be applied to improve the efficiency of three representative categories of secure-computation protocols based on cut-and-choose. We show improvements of up to an-order-of-magnitude in terms of bandwidth, and 12–106% in terms of total time. Source code of our game solvers is available to download at https://github.com/cut-n-choose.
View the full USENIX Security '16 program at https://www.usenix.org/conference/usenixsecurity16/technical-sessions
Ruiyu Zhu and Yan Huang, Indiana University; Jonathan Katz, University of Maryland; Abhi Shelat, Northeastern University
The cut-and-choose technique plays a fundamental role in cryptographic-protocol design, especially for secure two-party computation in the malicious model. The basic idea is that one party constructs n versions of a message in a protocol (e.g., garbled circuits); the other party randomly checks some of them and uses the rest of them in the protocol. Most existing uses of cut-and-choose fix in advance the number of objects to be checked and in optimizing this parameter they fail to recognize the fact that checking and evaluating may have dramatically different costs.
In this paper, we consider a refined cost model and formalize the cut-and-choose parameter selection problem as a constrained optimization problem. We analyze “cut-and-choose games” and show equilibrium strategies for the parties in these games. We then show how our methodology can be applied to improve the efficiency of three representative categories of secure-computation protocols based on cut-and-choose. We show improvements of up to an-order-of-magnitude in terms of bandwidth, and 12–106% in terms of total time. Source code of our game solvers is available to download at https://github.com/cut-n-choose.
View the full USENIX Security '16 program at https://www.usenix.org/conference/usenixsecurity16/technical-sessions
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
186
Likes
2
Duration
21:55
Published
Dec 3, 2021
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.