Understanding Asymmetric Encryption: Essential for Secure Communication
Explore the fundamentals of asymmetric encryption, a crucial element in contemporary cybersecurity. This deep dive will equip you with the knowledge necessary for secure communication.

Visualize Byte Code
9 views • Aug 15, 2024
About this video
Welcome to our deep dive into the world of asymmetric encryption, a cornerstone of modern cybersecurity!
🔐 What You'll Learn:
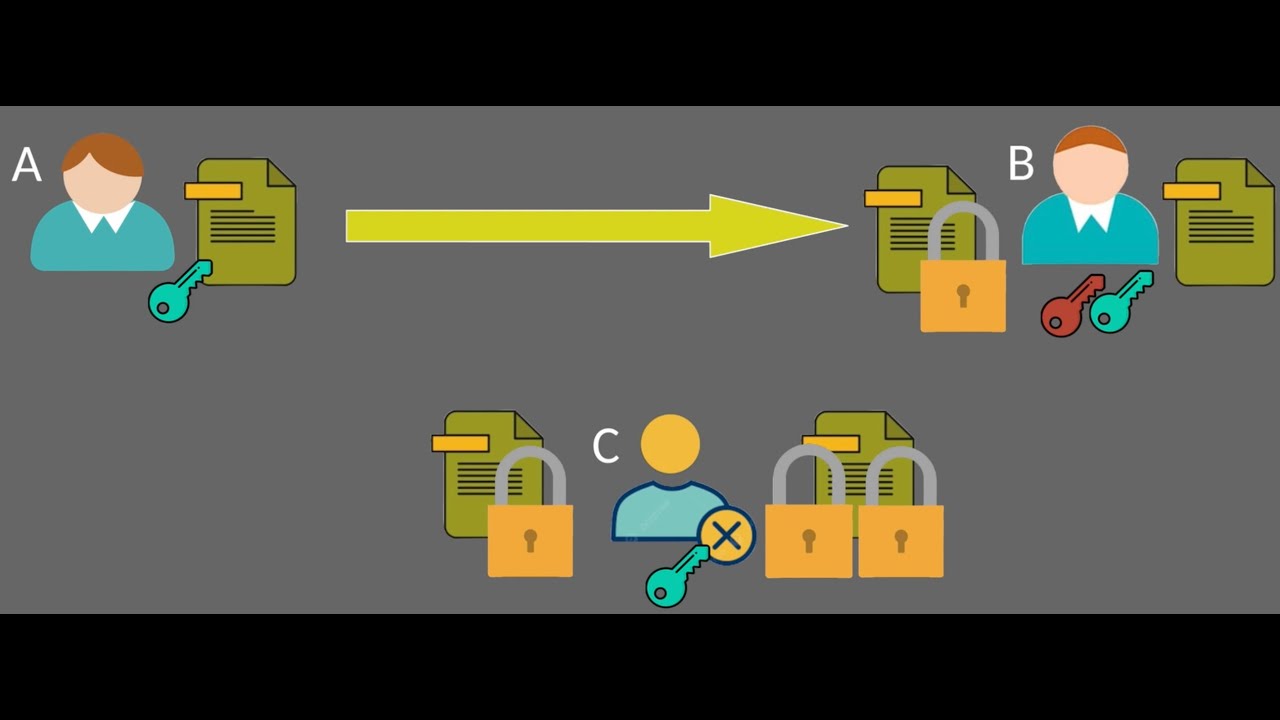
- The fundamentals of asymmetric encryption and how it differs from symmetric encryption.- How public and private keys work together to secure your data.- A step-by-step breakdown of the encryption and decryption process.Whether you're a cybersecurity enthusiast, a computer science student, or just curious about how your online data stays secure, this video will give you a clear and easy-to-understand explanation of asymmetric encryption.
🔍 Why It Matters:
In a world where data breaches and cyberattacks are increasingly common, understanding the technology that protects our sensitive information is more important than ever. Asymmetric encryption is used in everything from online banking to secure emails—making it a must-know topic for anyone interested in technology.
👍 Don’t Forget to Like, Comment, and Subscribe!If you found this video helpful, please give it a thumbs up and share it with your friends. For more tech and cybersecurity content, be sure to subscribe to our channel and hit the bell icon to get notified of our latest videos.
Chapters:
00:00 Definition: Asymmetric Encryption
01:07 Visualization of Asymmetric Encryption
02:50 Steps to perform Asymmetric Encryption
03:19 Generating RSA keys
04:38 Implementation: Generating RSA keys
06:34 Create public key
09:08 Create matching private key
11:49 Process: Encryption & Decryption via generated private key
12:33 Validating public & private key pairs
16:28 Encrypt string using RSA algorithm
🔐 What You'll Learn:
- The fundamentals of asymmetric encryption and how it differs from symmetric encryption.- How public and private keys work together to secure your data.- A step-by-step breakdown of the encryption and decryption process.Whether you're a cybersecurity enthusiast, a computer science student, or just curious about how your online data stays secure, this video will give you a clear and easy-to-understand explanation of asymmetric encryption.
🔍 Why It Matters:
In a world where data breaches and cyberattacks are increasingly common, understanding the technology that protects our sensitive information is more important than ever. Asymmetric encryption is used in everything from online banking to secure emails—making it a must-know topic for anyone interested in technology.
👍 Don’t Forget to Like, Comment, and Subscribe!If you found this video helpful, please give it a thumbs up and share it with your friends. For more tech and cybersecurity content, be sure to subscribe to our channel and hit the bell icon to get notified of our latest videos.
Chapters:
00:00 Definition: Asymmetric Encryption
01:07 Visualization of Asymmetric Encryption
02:50 Steps to perform Asymmetric Encryption
03:19 Generating RSA keys
04:38 Implementation: Generating RSA keys
06:34 Create public key
09:08 Create matching private key
11:49 Process: Encryption & Decryption via generated private key
12:33 Validating public & private key pairs
16:28 Encrypt string using RSA algorithm
Video Information
Views
9
Likes
1
Duration
19:53
Published
Aug 15, 2024
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now