Understanding Asymmetric Key Encryption: How Public and Private Keys Secure Your Data 🔐
Learn the fundamentals of asymmetric key encryption, including how public and private keys work together to protect your messages from unauthorized access.

Simple Security
441 views • Feb 19, 2015
About this video
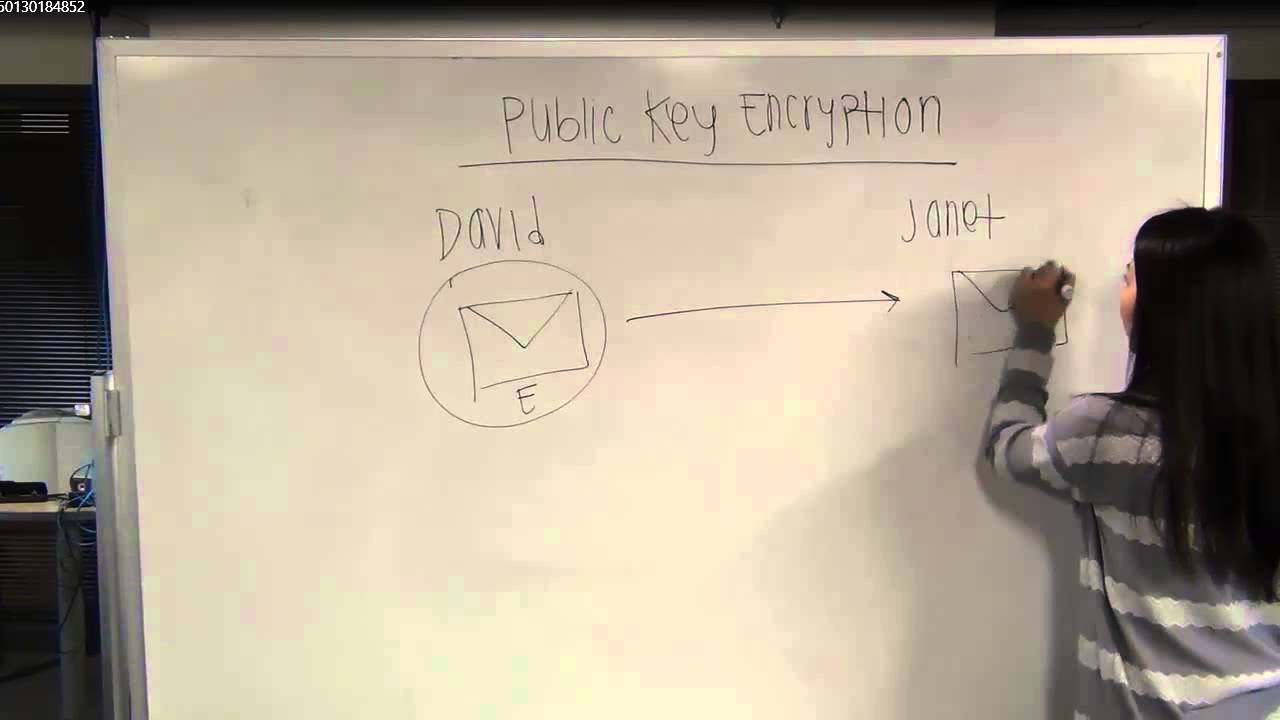
Two keys are involved in asymmetric key encryption: pubic and private keys
Any other user who wants to send an encrypted message can get the intended recipient's public key from a public directory
You use the public key to encrypt a message and you send it to the recipient
When the recipient gets the message, they decrypt it with their private key, which no one else should have access to except the recipient
References:
Hitachi ID Systems, Inc. (n.d.). Retrieved February 18, 2015, from http://hitachi- id.com/concepts/asymmetric_encryption.html
Any other user who wants to send an encrypted message can get the intended recipient's public key from a public directory
You use the public key to encrypt a message and you send it to the recipient
When the recipient gets the message, they decrypt it with their private key, which no one else should have access to except the recipient
References:
Hitachi ID Systems, Inc. (n.d.). Retrieved February 18, 2015, from http://hitachi- id.com/concepts/asymmetric_encryption.html
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
441
Likes
4
Duration
1:41
Published
Feb 19, 2015
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.