Understanding Public Key (Asymmetric) Encryption Systems 🔐
Explore the fundamentals of asymmetric cryptography, its history, and how it differs from symmetric key systems for secure communication.

Ritika xRay Pixy
156 views • Oct 4, 2020
About this video
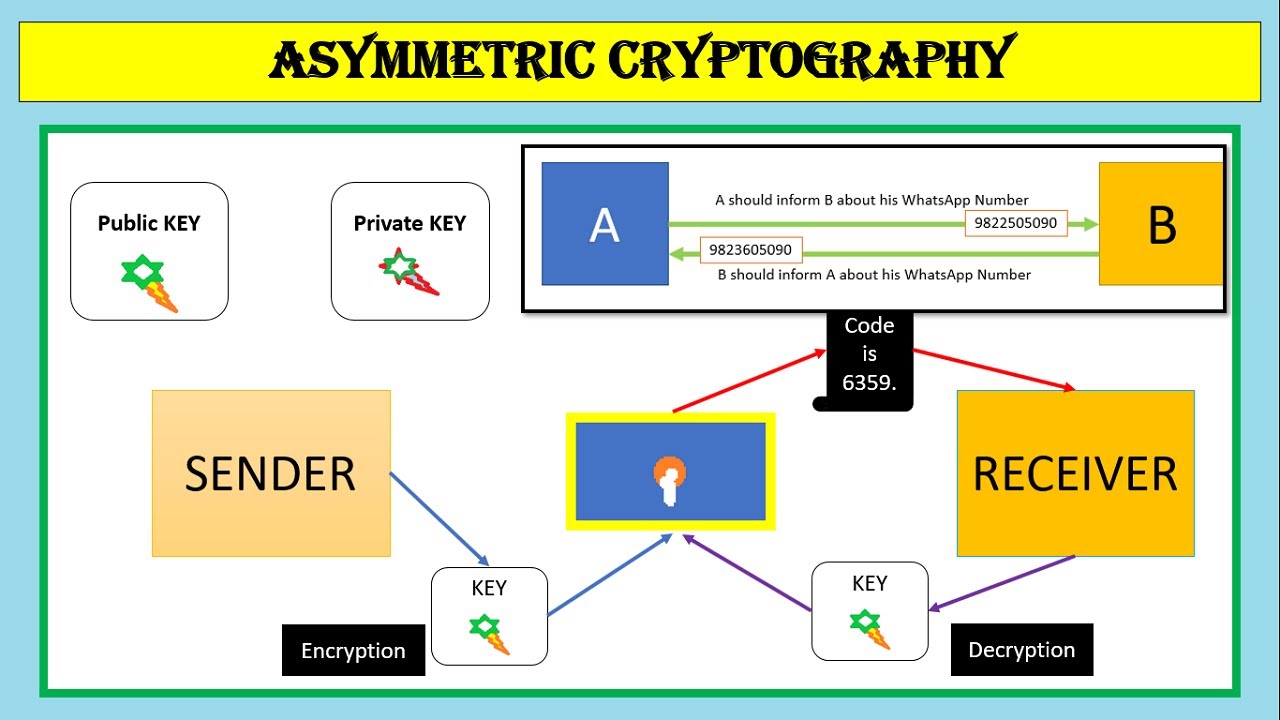
Public key(Asymmetric key) Encryption Systems
Symmetric Key Cryptography
Asymmetric Key Cryptography
History of Asymmetric Key Cryptography
Overview of Asymmetric Key Cryptography
Asymmetric Key Example
What is an example of public key encryption?
What are the features of a public key in asymmetric encryption?
What two types of keys are used in public key encryption?
Can a public key decrypt a private key?
Is RSA symmetric or asymmetric?
Which is the principle of the encryption using a key?
#security #RSA #cryptography #computer #computernotes #computerscience #computerscienceengineering #crypto
#cryptograph #cryptography #cryptographicsystems #information #security #privacy
#datasecurity #authenticity #authorization #algorithm #encryption #decrypt
#encrypted #notes #btech #hptu #himachalpradeshuniversity #btechstudent #ritikaxraypixy
Symmetric Key Cryptography
Asymmetric Key Cryptography
History of Asymmetric Key Cryptography
Overview of Asymmetric Key Cryptography
Asymmetric Key Example
What is an example of public key encryption?
What are the features of a public key in asymmetric encryption?
What two types of keys are used in public key encryption?
Can a public key decrypt a private key?
Is RSA symmetric or asymmetric?
Which is the principle of the encryption using a key?
#security #RSA #cryptography #computer #computernotes #computerscience #computerscienceengineering #crypto
#cryptograph #cryptography #cryptographicsystems #information #security #privacy
#datasecurity #authenticity #authorization #algorithm #encryption #decrypt
#encrypted #notes #btech #hptu #himachalpradeshuniversity #btechstudent #ritikaxraypixy
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
156
Likes
3
Duration
7:20
Published
Oct 4, 2020
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.