19. Understanding Asymmetric Encryption: The Key to Secure Communication 🔐
Learn how asymmetric encryption uses a pair of keys to ensure secure data transmission, offering a safer alternative to symmetric encryption.

Crypto4everyone
104 views • Feb 21, 2022
About this video
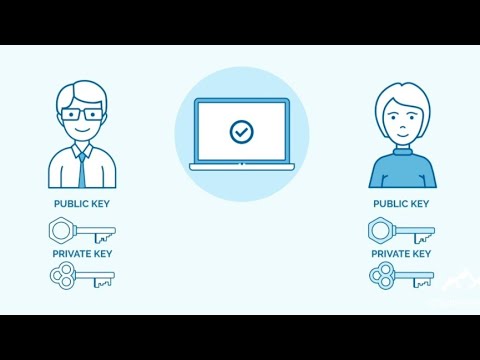
Unlike symmetric encryption that uses identical cryptographic keys, asymmetric encryption is a cryptography technique that uses two unique cryptographic keys, also referred to as a key pair, for the encryption and decryption of data.
In asymmetric encryption, anyone can encrypt messages using a public key, but only the holder of the paired, or private key, can decrypt the data.
How it Works
Let’s take a look at how asymmetric encryption works with an example...
Bob wants to send Sue a secure message using asymmetric encryption, and in order to do this, both Bob and Sue will have to generate a key pair. They can do this using a key pair generator such as the RSA algorithm. In fact, there are many free to use key pair generators available online.
Now that Bob and Sue have successfully generated a key pair, Sue sends Bob her Public key. Remember, a public key can be used by anyone who has it, to encrypt data so that it can be decrypted using its paired private key.
Having received Sues public key, Bob uses it to encrypt his message, and once done, sends his message to Sue. Sue now uses her paired private key, that only she has access to, to decrypt and read Bob’s message.
Both Bob and Sue can share their public keys with whoever they like, allowing recipients to encrypt data that only they themselves can read using their private keys. Now it is important to note that paired keys cannot be derived from each other, meaning that if someone has access to someone else’s public key, they cannot use that to derive the paired private key and therefore decrypt any encrypted messages sent to them.
Asymmetric encryption only works if the owner of a private key keeps their private key, well, private.
Keys vs Addresses
In the world of cryptocurrency, using Bitcoin for our example. Public keys are also referred to as public addresses. A public address essentially allows other users of the network to send you cryptocurrency.
One's private key, however, remains private and is used only by the sender, to send cryptocurrency to other people on the network
Subscribe the channel for more and better videos
In asymmetric encryption, anyone can encrypt messages using a public key, but only the holder of the paired, or private key, can decrypt the data.
How it Works
Let’s take a look at how asymmetric encryption works with an example...
Bob wants to send Sue a secure message using asymmetric encryption, and in order to do this, both Bob and Sue will have to generate a key pair. They can do this using a key pair generator such as the RSA algorithm. In fact, there are many free to use key pair generators available online.
Now that Bob and Sue have successfully generated a key pair, Sue sends Bob her Public key. Remember, a public key can be used by anyone who has it, to encrypt data so that it can be decrypted using its paired private key.
Having received Sues public key, Bob uses it to encrypt his message, and once done, sends his message to Sue. Sue now uses her paired private key, that only she has access to, to decrypt and read Bob’s message.
Both Bob and Sue can share their public keys with whoever they like, allowing recipients to encrypt data that only they themselves can read using their private keys. Now it is important to note that paired keys cannot be derived from each other, meaning that if someone has access to someone else’s public key, they cannot use that to derive the paired private key and therefore decrypt any encrypted messages sent to them.
Asymmetric encryption only works if the owner of a private key keeps their private key, well, private.
Keys vs Addresses
In the world of cryptocurrency, using Bitcoin for our example. Public keys are also referred to as public addresses. A public address essentially allows other users of the network to send you cryptocurrency.
One's private key, however, remains private and is used only by the sender, to send cryptocurrency to other people on the network
Subscribe the channel for more and better videos
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
104
Likes
4
Duration
2:31
Published
Feb 21, 2022
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now