Secure and Fast Authentication with Chameleon Hashing Key Chain 🔐
Discover how our final year engineering project at UGS and SIT leverages Chameleon Hashing Key Chains for quick, secure user authentication. Learn about innovative methods to enhance security efficiency.

University of Glasgow Singapore
229 views • Apr 23, 2020
About this video
Final Year Project in Engineering at University of Glasgow Singapore (UGS) and Singapore Institute of Technology (SIT)
Student: Student: Chu Yu Han
Supervisor: Supervisor: Prof. Sye Loong Keoh (UGS)
Project Description:
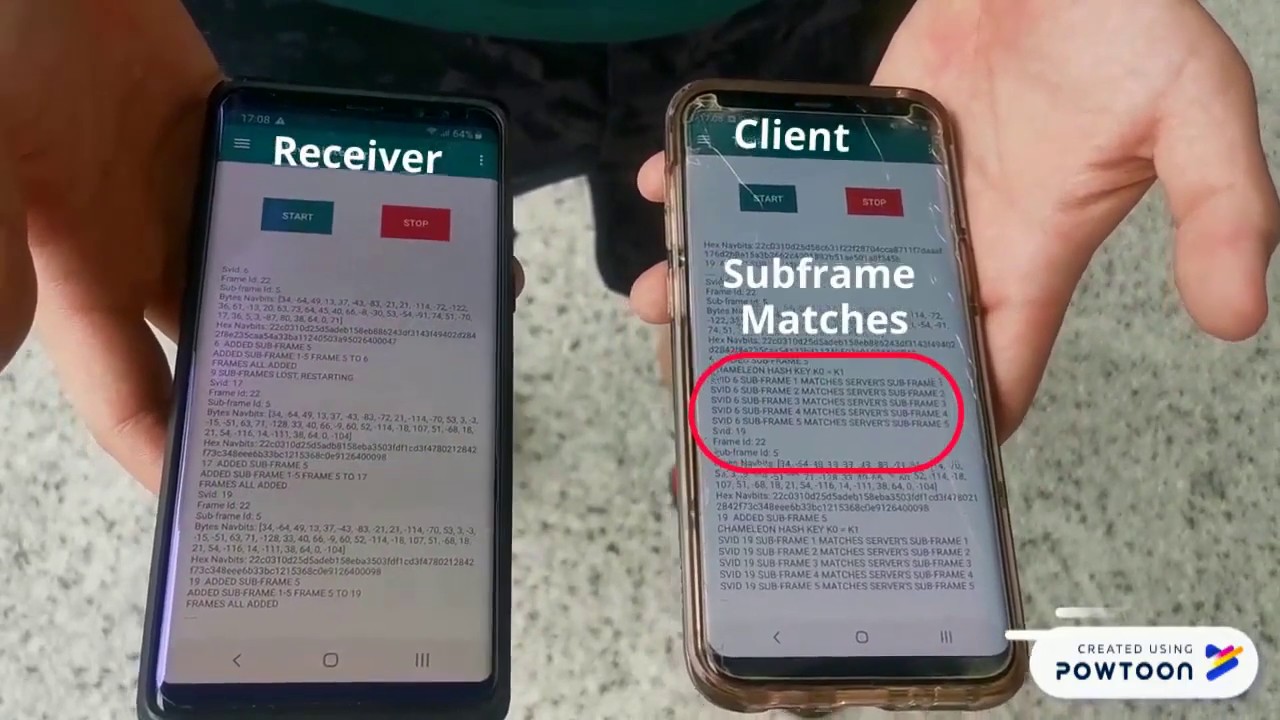
Public key cryptosystem is currently the de-facto standard for authentication. It is also used to perform key agreement between two parties in order to establish a symmetric-key to be used for encryption. Using public-key cryptosystem for authentication is rather expensive and not efficient.
In this project, we would like to explore the use of chameleon hashing that is based on Elliptic Curve Cryptography (ECC) to form a keychain to perform fast authentication for continuous stream of data. Currently, there is a scheme defined by Universita di Roma, but we found that the scheme is flawed, if one of the key in the hash chain is compromised, the entire chain is also compromised hence breaking the forward secrecy property.
Student: Student: Chu Yu Han
Supervisor: Supervisor: Prof. Sye Loong Keoh (UGS)
Project Description:
Public key cryptosystem is currently the de-facto standard for authentication. It is also used to perform key agreement between two parties in order to establish a symmetric-key to be used for encryption. Using public-key cryptosystem for authentication is rather expensive and not efficient.
In this project, we would like to explore the use of chameleon hashing that is based on Elliptic Curve Cryptography (ECC) to form a keychain to perform fast authentication for continuous stream of data. Currently, there is a scheme defined by Universita di Roma, but we found that the scheme is flawed, if one of the key in the hash chain is compromised, the entire chain is also compromised hence breaking the forward secrecy property.
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
229
Likes
7
Duration
1:05
Published
Apr 23, 2020
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now