Understanding MAC and HMAC: Secure Message Authentication Explained 🔐
Learn why hashing alone isn't enough for security and discover how Message Authentication Codes (MACs) and HMACs protect your data. Perfect for beginners and security enthusiasts!

Practical Networking
30.0K views • Aug 12, 2024
About this video
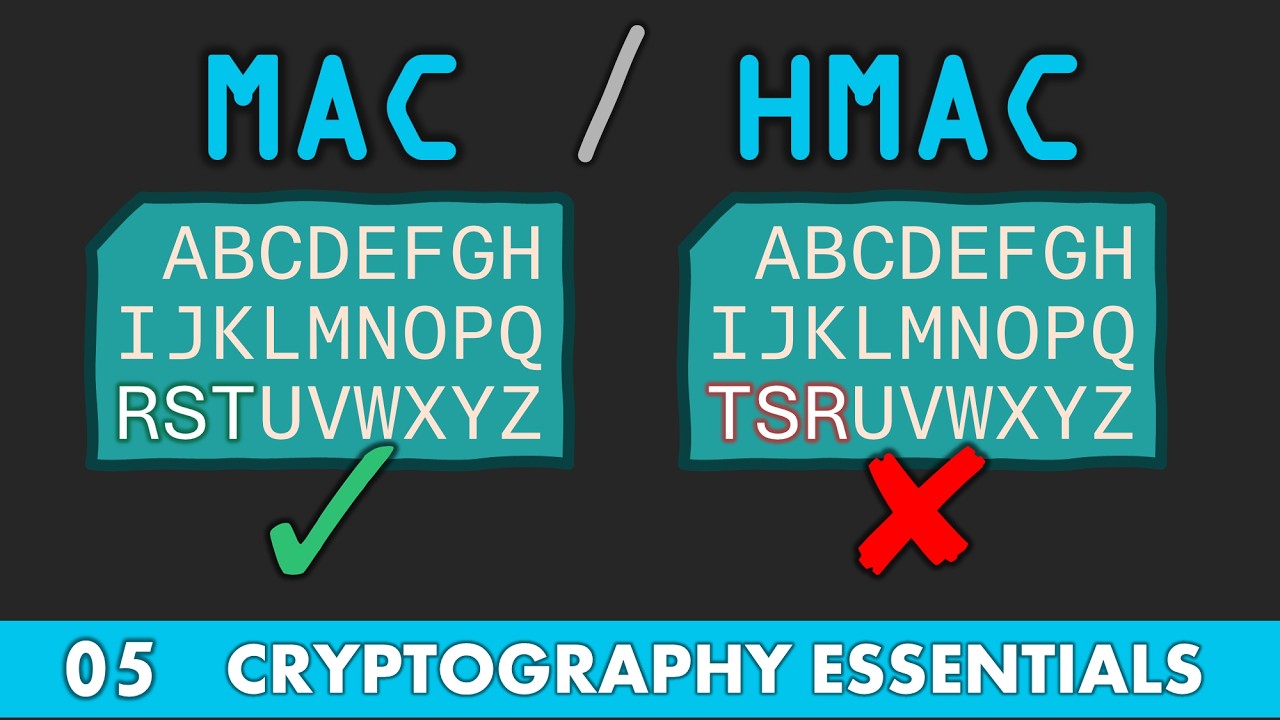
In this video we explore the concepts of MACs. We first explore why Hashing alone is not enough, which leads us into the definition of a MAC. Then we define the most commonly used MAC... the HMAC.
// CHAPTERS //
0:00 - Message Authentication Codes
0:38 - Hashing isn't enough for Integrity
2:04 - Hashing vs Encryption (two different problems)
2:37 - MAC Simply Explained
3:58 - MACs vs HMACs
5:38 - MAC Algorithms
5:57 - MACs can be included with Encryption in AEAD Ciphers
6:16 - Full Crypto Essentials series: pracnet.net/ce
// FULL SERIES - Cryptography Essentials //
This video is part of a 16-part series covering the essentials of modern Cryptography. Explained simply, and technically accurate.
The full series is available here:
📋 https://www.youtube.com/playlist?list=PLIFyRwBY_4bQvq5PuJASilkHSVGLZtceZ
(or use this shortcut: pracnet.net/ce)
00 Series Introduction
01 Hashing
02 Keys / Secret Keys
03 Symmetric Cryptography
04 Encryption
05 MAC / HMAC
06 Pseudo Random Function
07 Asymmetric Cryptography
08 Asymmetric Encryption (RSA)
09 Signatures
10 RSA Signatures
11 DSA Signatures
12 Key Exchanges
13 RSA Key Exchanges
14 DH Key Exchanges
15 Elliptic Curve Cryptography
// SUPPORT PRACTICAL NETWORKING //
If this content benefited you, then here are TOTALLY FREE ways to show your appreciation:
- 👍 Like to help this video reach more viewers
- 💬 Comment to boost the channel's visibility
- 🔔 Subscribe to help me attract sponsors (this is the number they care about)
// CHAPTERS //
0:00 - Message Authentication Codes
0:38 - Hashing isn't enough for Integrity
2:04 - Hashing vs Encryption (two different problems)
2:37 - MAC Simply Explained
3:58 - MACs vs HMACs
5:38 - MAC Algorithms
5:57 - MACs can be included with Encryption in AEAD Ciphers
6:16 - Full Crypto Essentials series: pracnet.net/ce
// FULL SERIES - Cryptography Essentials //
This video is part of a 16-part series covering the essentials of modern Cryptography. Explained simply, and technically accurate.
The full series is available here:
📋 https://www.youtube.com/playlist?list=PLIFyRwBY_4bQvq5PuJASilkHSVGLZtceZ
(or use this shortcut: pracnet.net/ce)
00 Series Introduction
01 Hashing
02 Keys / Secret Keys
03 Symmetric Cryptography
04 Encryption
05 MAC / HMAC
06 Pseudo Random Function
07 Asymmetric Cryptography
08 Asymmetric Encryption (RSA)
09 Signatures
10 RSA Signatures
11 DSA Signatures
12 Key Exchanges
13 RSA Key Exchanges
14 DH Key Exchanges
15 Elliptic Curve Cryptography
// SUPPORT PRACTICAL NETWORKING //
If this content benefited you, then here are TOTALLY FREE ways to show your appreciation:
- 👍 Like to help this video reach more viewers
- 💬 Comment to boost the channel's visibility
- 🔔 Subscribe to help me attract sponsors (this is the number they care about)
Video Information
Views
30.0K
Likes
1.1K
Duration
6:52
Published
Aug 12, 2024
User Reviews
4.6
(5) Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now