Essential User Authentication Protocols for Secure Systems 🔐
Discover how user authentication protocols protect digital systems in our latest video on Cryptography and System Security. Learn key methods to enhance security and prevent breaches!

Ekeeda
307 views • Jul 21, 2023
About this video
in our latest video on Cryptography and System Security! 💻 Join us as we explore the crucial role that authentication plays in safeguarding digital systems and discover the key protocols shaping secure access to sensitive information.
🚀 Key Topics Explored:
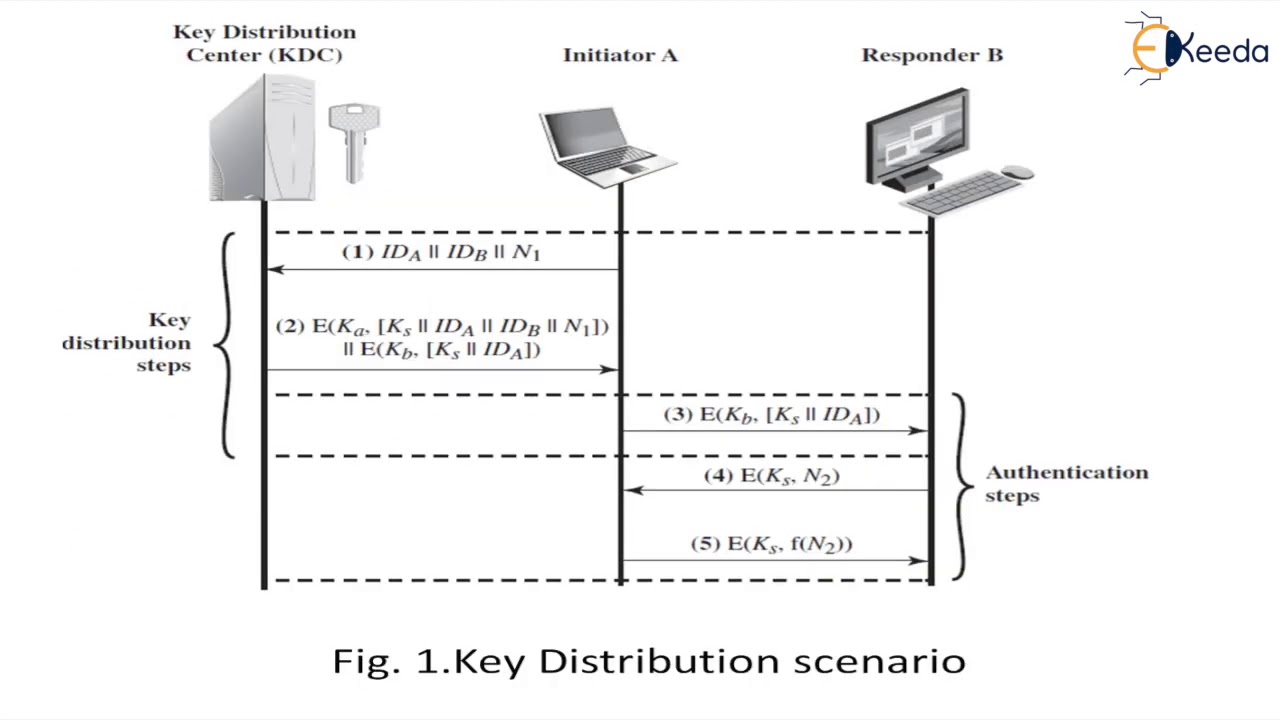
🔒 Understanding User Authentication Protocols
🔑 Importance of Authentication in System Security
💡 Overview of Common Authentication Methods
🌐 Role of Cryptography in Secure User Access
🔗 Comparative Analysis of Authentication Protocols
👉 Download Ekeeda Application & Learn from the best professors with 10+ years of experience.
Subscribe to a Course or Start a Free Trial of Package.
✤ Download the Ekeeda - Learning App for Engineering Courses App here:
➤ Android & iOS: https://ekeeda.com/download.html
Access the Complete Playlist of Subject GATE Algorithms - https://www.youtube.com/playlist?list=PLO4TWepMw7ggN22wYVdfE7KmOcMjNHh4m
✤ For More Such Classes Get Subscription Advantage:
👉 GATE Algorithms (GATE Computer Science and Information Technology): https://ekeeda.com/gate/gate-computer-science-and-information-technology/algorithms
👉 GATE Computer Science and Information Technology: https://ekeeda.com/gate/gate-computer-science-and-information-technology
👉 Explore our Courses - https://ekeeda.com/catalog
Like us on Facebook: https://www.facebook.com/Ekeeda
Follow us on Instagram: https://www.instagram.com/ekeeda_official/
Follow us on Twitter: https://twitter.com/ekeeda_official
Follow us on LinkedIn: https://www.linkedin.com/company/ekeeda.com
Visit Our Website: https://ekeeda.com/
Subscribe to Ekeeda Channel to access more videos: https://www.youtube.com/c/Ekeeda?sub_confirmation=1
🚀 Key Topics Explored:
🔒 Understanding User Authentication Protocols
🔑 Importance of Authentication in System Security
💡 Overview of Common Authentication Methods
🌐 Role of Cryptography in Secure User Access
🔗 Comparative Analysis of Authentication Protocols
👉 Download Ekeeda Application & Learn from the best professors with 10+ years of experience.
Subscribe to a Course or Start a Free Trial of Package.
✤ Download the Ekeeda - Learning App for Engineering Courses App here:
➤ Android & iOS: https://ekeeda.com/download.html
Access the Complete Playlist of Subject GATE Algorithms - https://www.youtube.com/playlist?list=PLO4TWepMw7ggN22wYVdfE7KmOcMjNHh4m
✤ For More Such Classes Get Subscription Advantage:
👉 GATE Algorithms (GATE Computer Science and Information Technology): https://ekeeda.com/gate/gate-computer-science-and-information-technology/algorithms
👉 GATE Computer Science and Information Technology: https://ekeeda.com/gate/gate-computer-science-and-information-technology
👉 Explore our Courses - https://ekeeda.com/catalog
Like us on Facebook: https://www.facebook.com/Ekeeda
Follow us on Instagram: https://www.instagram.com/ekeeda_official/
Follow us on Twitter: https://twitter.com/ekeeda_official
Follow us on LinkedIn: https://www.linkedin.com/company/ekeeda.com
Visit Our Website: https://ekeeda.com/
Subscribe to Ekeeda Channel to access more videos: https://www.youtube.com/c/Ekeeda?sub_confirmation=1
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
307
Likes
3
Duration
19:53
Published
Jul 21, 2023
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.