Secure Remote User Authentication with Needham-Schroeder Protocol 🔐
Learn how the Needham-Schroeder protocol uses symmetric encryption to securely authenticate remote users. Enhance your cybersecurity knowledge today!

Chirag Bhalodia
33.5K views • Oct 6, 2020
About this video
Remote User Authentication Using Symmetric Encryption | Needham Shcroeder Protocol
Follow my blog: https://www.chiragbhalodia.com/2021/11/remote-user-authentication.html
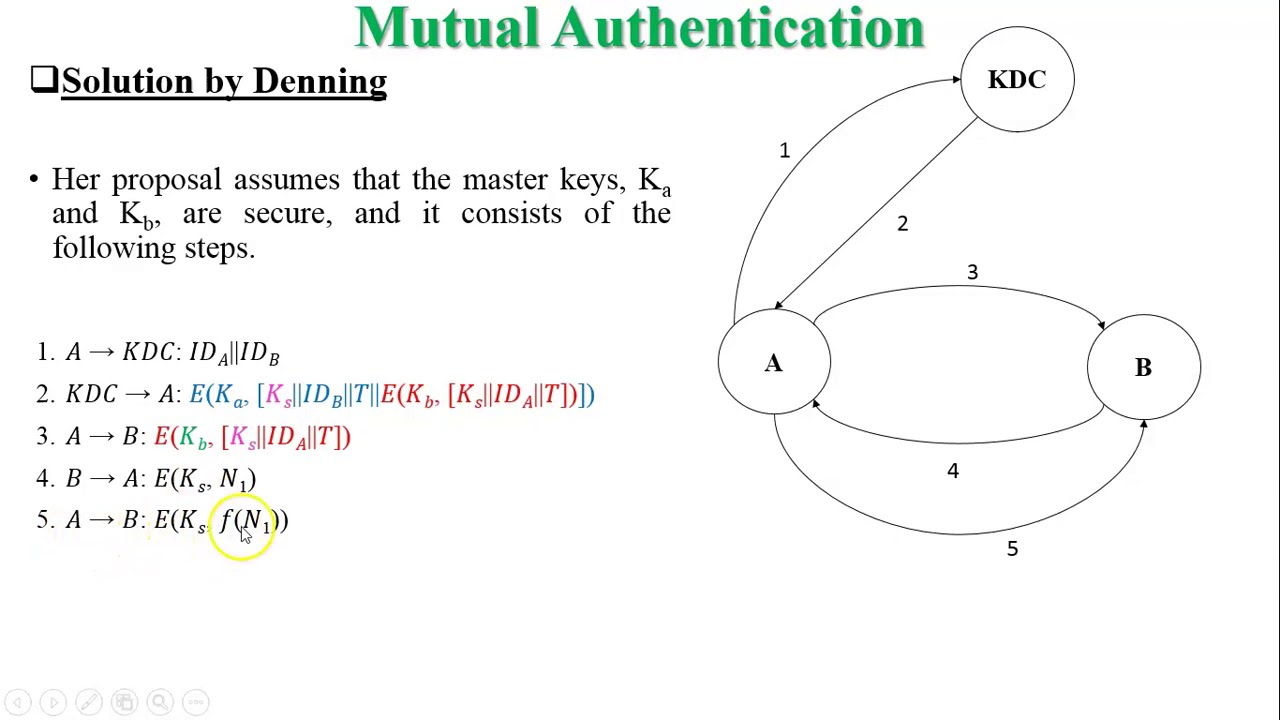
In this video, I have covered Remote User Authentication using Symmetric Encryption techniques:
- Mutual Authentication (needham-Shcroeder Protocol)
- 1-way Authentication (One - way Authentication based on needham-Shcroeder Protocol)
0:00 Introduction
0:10 Outline
0:19 Mutual Authentication
2:19 Needham - Schroeder Protocol
7:53 denning Solution
12:48 Alternate solution for Suppress Replay Attack
18:29 One-way authentication
#Remote_User_Authentication
#Remote_Suer_Authentication_using_Symmetric_Encryption
#Mutual_Authentication
#One_way_Authentication
#Needham_Schroeder_protocol
#Denning_Solution
#Suppress_replay_Attack
#chiragbhalodia
#chirag_bhalodia
Follow my blog: https://www.chiragbhalodia.com/2021/11/remote-user-authentication.html
In this video, I have covered Remote User Authentication using Symmetric Encryption techniques:
- Mutual Authentication (needham-Shcroeder Protocol)
- 1-way Authentication (One - way Authentication based on needham-Shcroeder Protocol)
0:00 Introduction
0:10 Outline
0:19 Mutual Authentication
2:19 Needham - Schroeder Protocol
7:53 denning Solution
12:48 Alternate solution for Suppress Replay Attack
18:29 One-way authentication
#Remote_User_Authentication
#Remote_Suer_Authentication_using_Symmetric_Encryption
#Mutual_Authentication
#One_way_Authentication
#Needham_Schroeder_protocol
#Denning_Solution
#Suppress_replay_Attack
#chiragbhalodia
#chirag_bhalodia
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
33.5K
Likes
436
Duration
20:53
Published
Oct 6, 2020
User Reviews
4.5
(6) Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.