Enhanced RSA Encryption with Double Steganography in DWT Domain for Secure Image Watermarking 🔒
Discover how combining RSA encryption with double steganography using Discrete Wavelet Transform (DWT) enhances image security and watermark robustness. Learn the innovative design techniques for advanced data hiding.

VERILOG COURSE TEAM-MATLAB PROJECT
65 views • Feb 24, 2021
About this video
DESIGN DETAILS
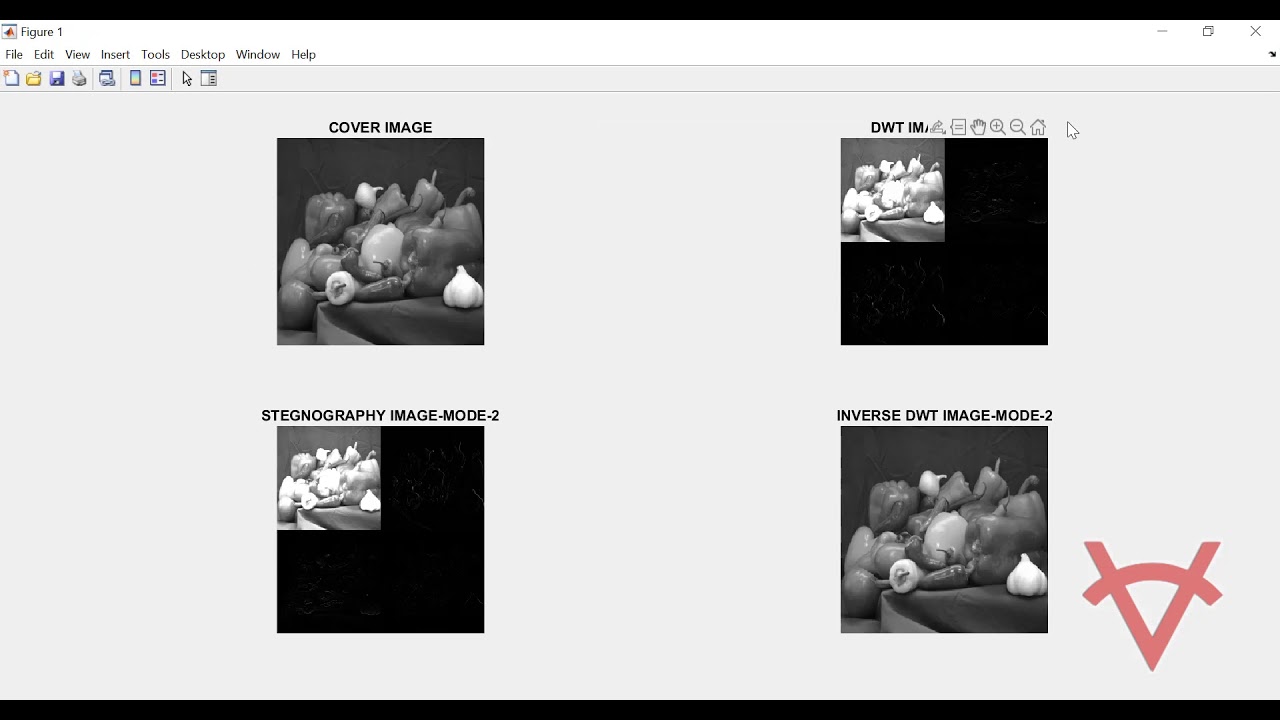
Watermarking and Steganography are two closely related techniques of information hiding. The fundamental difference between the two is that former is a method used for copyright protection while the latter is a method of embedding secret data into a camouflage media so that unintended recipients will not have access to the data. Steganography not only hides the data, but also conceals the fact that a secret data is being transmitted. However, cryptography is different from steganography since a cipher text has meaningless form and the existence of a secret data is detectable by malicious attackers. This Matlab design uses the concept of RSA algorithm for data encryption, where the data will be converted into a cipher, which will be then hidden into an image file. To enable large capacity of data and maintaining good visual quality of the cover image, the embedding is applied by modifying the details coefficients in transform domain of Two-Dimensional Discrete Wavelet Transform (DWT). Furthermore, to enhance the security level of the data, the concept of Double-Stegging is used to embed the data into the image file. The greatest advantage of this system is that it does not require the original cover image for successful extraction of the secret data. The design is tested in three modes of operation and verified for PSNR values for different payloads of input data for the secret message.
Mode-1: Data encrypt ion using RSA Algorithm and Embedding by Double-stegging.
Mode-2: Data encrypt ion using RSA Algorithm and Embedding data into 2 different sets of details coefficients.
Mode-3: No data encryption applied and Embedding data into 3, different sets of details coefficients.
REFERENCES
Reference Paper-1: Image Steganography in DWT Domain using Double-stegging with RSA Encryption.
Author’s Name: Nadiya PV and B Mohammed lmran
Source: IEEE
Year: 2013
Request source code for academic purpose, fill REQUEST FORM below,
http://www.verilogcourseteam.com/request-form
You may contact +91 7904568456 by WhatsApp Chat, for paid services.
We are available on Telegram and Signal.
Visit Website: http://www.verilogcourseteam.com/
Visit Our Social Media
Like our Facebook Page: https://www.facebook.com/VerilogCourseTeam/
Subscribe: https://www.youtube.com/verilogcourseteamelectricalprojects
Subscribe: https://www.youtube.com/verilogcourseteammatlabproject
Subscribe: https://www.youtube.com/verilogcourseteam
Watermarking and Steganography are two closely related techniques of information hiding. The fundamental difference between the two is that former is a method used for copyright protection while the latter is a method of embedding secret data into a camouflage media so that unintended recipients will not have access to the data. Steganography not only hides the data, but also conceals the fact that a secret data is being transmitted. However, cryptography is different from steganography since a cipher text has meaningless form and the existence of a secret data is detectable by malicious attackers. This Matlab design uses the concept of RSA algorithm for data encryption, where the data will be converted into a cipher, which will be then hidden into an image file. To enable large capacity of data and maintaining good visual quality of the cover image, the embedding is applied by modifying the details coefficients in transform domain of Two-Dimensional Discrete Wavelet Transform (DWT). Furthermore, to enhance the security level of the data, the concept of Double-Stegging is used to embed the data into the image file. The greatest advantage of this system is that it does not require the original cover image for successful extraction of the secret data. The design is tested in three modes of operation and verified for PSNR values for different payloads of input data for the secret message.
Mode-1: Data encrypt ion using RSA Algorithm and Embedding by Double-stegging.
Mode-2: Data encrypt ion using RSA Algorithm and Embedding data into 2 different sets of details coefficients.
Mode-3: No data encryption applied and Embedding data into 3, different sets of details coefficients.
REFERENCES
Reference Paper-1: Image Steganography in DWT Domain using Double-stegging with RSA Encryption.
Author’s Name: Nadiya PV and B Mohammed lmran
Source: IEEE
Year: 2013
Request source code for academic purpose, fill REQUEST FORM below,
http://www.verilogcourseteam.com/request-form
You may contact +91 7904568456 by WhatsApp Chat, for paid services.
We are available on Telegram and Signal.
Visit Website: http://www.verilogcourseteam.com/
Visit Our Social Media
Like our Facebook Page: https://www.facebook.com/VerilogCourseTeam/
Subscribe: https://www.youtube.com/verilogcourseteamelectricalprojects
Subscribe: https://www.youtube.com/verilogcourseteammatlabproject
Subscribe: https://www.youtube.com/verilogcourseteam
Video Information
Views
65
Duration
7:47
Published
Feb 24, 2021
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now