Search Results for "ciphertext attacks"
Find videos related to your search query. Browse through our collection of videos matching "ciphertext attacks". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "ciphertext attacks"
50 results found

8:37
CSS #9 Cryptanalytic attacks|Ciphertext only|Known Plaintext|Chosen Plaintext|Chosen Ciphertext|BTB
Be The Best
3.1K views

12:24
Cryptanalysis | Ciphertext-only | Known plaintext | chosen ciphertext | chosen plaintext
chandu's smart class
111 views

3:47
What is a plaintext? What is a ciphertext? Ciphertext , Encryption, Decryption Defined and Explained
Technotics World
247 views

3:26
best eagle attacks | eagle attacks mountain goats | eagle attacks fox | eagle under water | eagle attacks | eagle | falcon
GIlgit Baltistan Adventure
20 views

28:41
USENIX Security '16 - Dancing on the Lip of the Volcano: Chosen Ciphertext Attacks on Apple iMessage
USENIX
186 views

12:06
7 3 Chosen ciphertext attacks 12 min
Jake Danniel
329 views
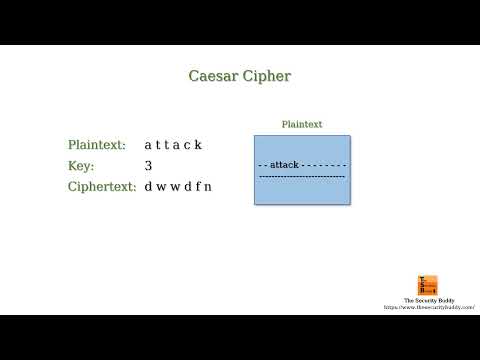
3:59
What are known-plaintext, chosen-plaintext, and chosen-ciphertext attacks in cryptanalysis?
The Security Buddy
8.5K views

16:51
LEC 16 ||Security Against Chosen Ciphertext Attacks
fahad osman
592 views
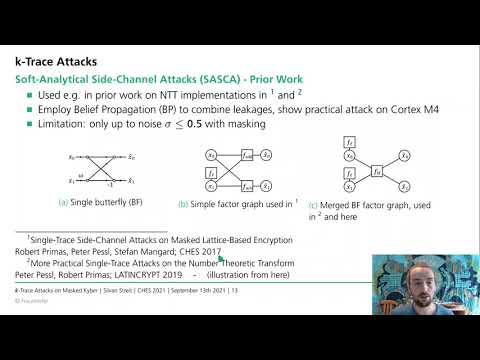
22:54
Chosen Ciphertext k-Trace Attacks on Masked CCA2 Secure Kyber
IACR
600 views
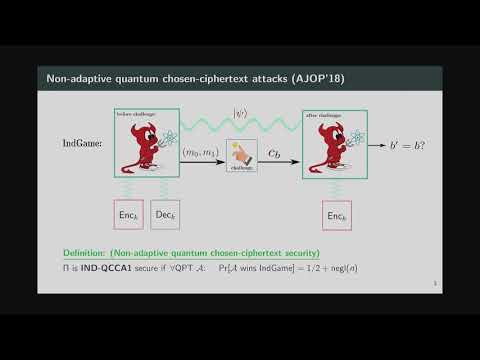
24:28
Alexander Poremba: On Quantum Chosen-Ciphertext Attacks and Learning with Errors
QuICS
137 views

3:19
Ciphertext-only attacks on randomly permuted many-time-pad (3 SOLUTIONS!!)
Nida Karagoz
10 views

12:17
USENIX Security '20 - Automating the Development of Chosen Ciphertext Attacks
USENIX
272 views
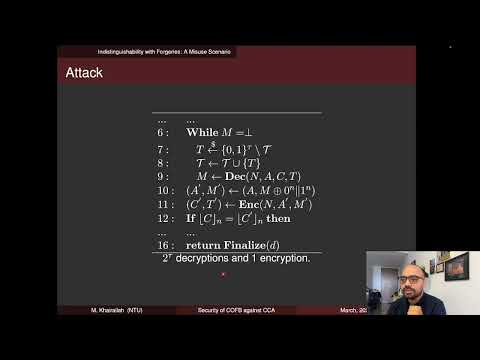
20:32
Security of COFB against Chosen Ciphertext Attacks
IACR
102 views

43:18
Automating the Development of Chosen Ciphertext Attacks
IACR
572 views
18:12
Et tu, Brute? Side Channel Assisted Chosen Ciphertext Attacks using Valid Ciphertexts on HQC KEM
PQCrypto conference videos
47 views

4:29
CISSP Cyber Security: Cryptographic Attacks (Known/Chosen Ciphertext) #cryptography #cryptosecrets
Cyber Security Cartoons
132 views

34:41
Lecture 14: Chosen Ciphertext Attacks (CCA-Security)
Cryptography - علم التشفير
795 views
55:37
CDL - Matt Green - Using SMT Solvers to Automate Chosen-Ciphertext Attacks
UCYBR - UMBC Center for Cybersecurity
50 views

6:53
Network security attacks in Hindi | Active attacks and Passive attacks in Network security in Hindi
QuickCS
1.2K views

31:03
Password Attacks and their Countermeasures | Password Attacks | Cyber Security Attacks
CyberPlatter
2.0K views

5:07
cryptanalytic attacks| urdu hindi | cryptanalytic attacks lecture| cryptanalytic attacks tutorial|19
IT Expert Rai Jazib
4.0K views

8:47
CB3602|CCS354|EC3401 Security Attacks .Passive Attacks vs. Active Attacks.#ec3401 #ccs354
SHOBINA K
105 views

6:38
security attacks || urdu hindi | passive attacks in urdu | active attacks in urdu | types | part 6
IT Expert Rai Jazib
201 views

13:51
Most Amazing Snake Attacks - King Cobra attacks Python - Python attacks Cobra
Our Animals
1 views

16:00
Top 10 Leopard Attacks - Most Amazing Animal Attacks - Crazy Leopard Attacks
Diverte Mania
35 views

11:01
Wild Animal Attacks 2023 - Crocodile, Leopard, Tiger Attacks Wild Boar - Animal attacks
Tout est art
1.4K views

35:45
Networks Security | Attacks | Active Attacks | Passive Attacks | Cryptography | Steganography | IA
Bhavishya Coaching SGNR
771 views
![CSS #3 - [PART-1] Security Attacks | Passive attacks | Active attacks | Be The Best | BTB](/image/i.ytimg.com/vi/_HLKp9wvbkM/xhqdefault.jpg.pagespeed.ic.hZE19l_P6j.jpg)
5:16
CSS #3 - [PART-1] Security Attacks | Passive attacks | Active attacks | Be The Best | BTB
Be The Best
416 views

5:35
Chosen-ciphertext attack
WikiAudio
2.3K views

1:01
The Mysterious Ciphertext
HOTWIRE
760 views

4:26
Ciphertext-only attack
WikiAudio
6.0K views

4:18
Decrypting Ciphertext with the Vigenère Cipher: Step-by-Step Tutorial"
PHY, CHM, MATHS & COMP MUHAMMAD HAMZA BIN ATTA
7 views

10:05
RSA Example Lecture 1 | p=7, q=11, plaintext=m=9, Find public key (e), private key (d) & ciphertext
TRN CSE Tutorials
2.2K views

2:02
421 Chosen Ciphertext Attack
It Rating
270 views

24:26
Chosen-Ciphertext Security from Slightly Lossy Trapdoor Functions.
IACR
465 views

26:10
Chosen Ciphertext Security via Point Obfuscation
The Qualcomm Institute
251 views

2:29
What is a Ciphertext-only attack in cryptanalysis?
The Security Buddy
3.4K views

0:54
Day 24: Cryptography Basics 🔐 | Plaintext, Ciphertext, Symmetric vs Asymmetric Key| #100daychallenge
Encrypticle
82 views
5:17
What is a plaintext? What is a ciphertext?
internet-class
29.3K views

4:06
Circuit Ciphertext-policy Attribute-based Hybrid Encryption with Verifiable Delegation
MICANS IEEE PROJECTS 2015 PPT VIDEOS
990 views

7:06
Ciphertext
Wikivoicemedia
283 views

0:16
Unlocking the Secrets: Understanding Ciphertext in Cryptography #short #shortvideo #shorts
Aarnaaology
36 views
3:39
Ciphertext-Only Method ( Earphone Very Recommended )
Eizlan Yusof
45 views

8:15
Ciphertext Attack
CyberSecCISSPhacks
34 views

3:13
Ciphertext Only Method
MUHAMMAD IKMAL
44 views

23:43
Fully Homomorphic Encryption with Relatively Small Key and Ciphertext Sizes.
IACR
1.4K views
0:58
Yaytsogram cipher code November 8 #Yaytsogram #yaytsogramcipher #ciphercodes #ciphertext #airdrop
Digital Assets
36 views
0:37
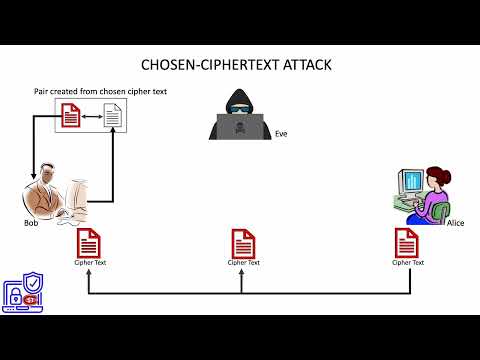
6. Chosen ciphertext attack
Cybersecurity at St. Cloud State University
6.2K views

1:00
क्या होता है #ciphertext?? What is #Cryptography?? Kumar S Bhaweshnu
civil academy
2.3K views

0:21
Chosen Ciphertext Attack, Cybersecurity Mini Dictionary #shorts
Datasafe World
24 views
Page 1 Next