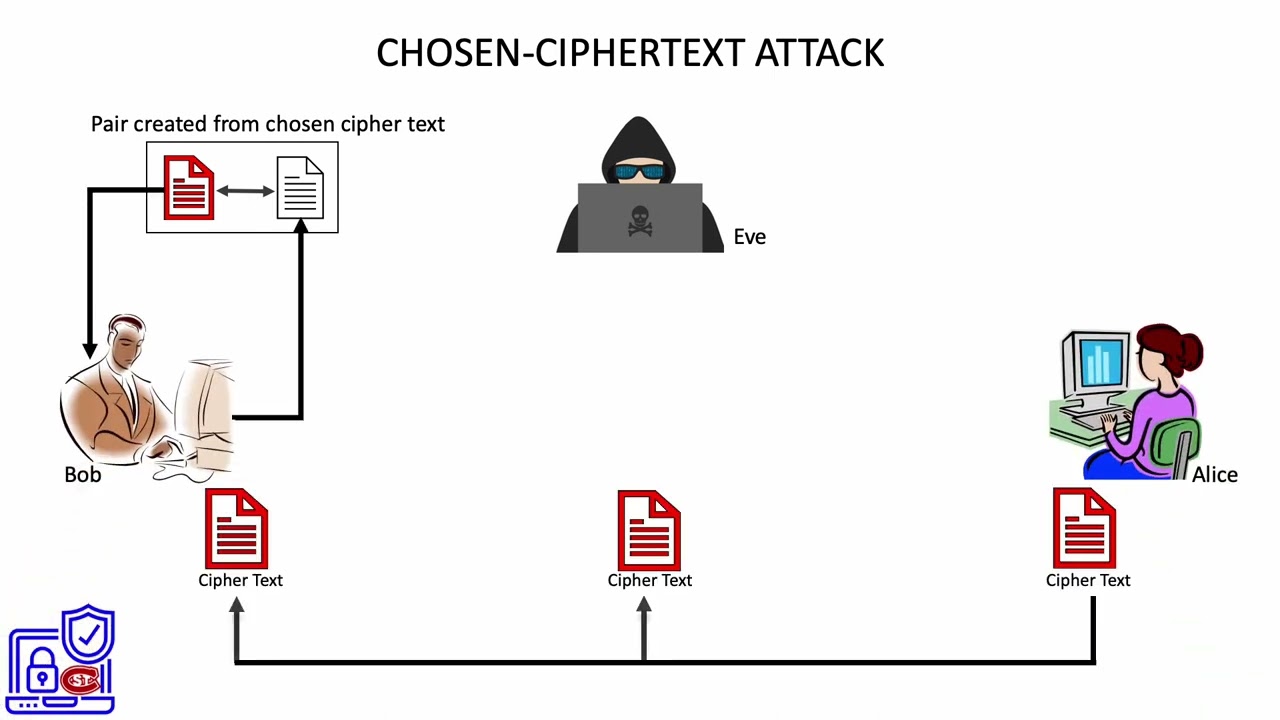
6. Understanding Chosen Ciphertext Attacks: How They Compromise Security 🔐
Learn what a chosen ciphertext attack is, how hackers exploit it, and how to protect your data from this sophisticated threat.

Cybersecurity at St. Cloud State University
6.2K views • Jun 27, 2022
Video Information
Views
6.2K
Likes
40
Duration
0:37
Published
Jun 27, 2022
User Reviews
4.1
(1) Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.