Search Results for "Cybersecurity Guidelines"
Find videos related to your search query. Browse through our collection of videos matching "Cybersecurity Guidelines". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Cybersecurity Guidelines"
50 results found

0:41
What is a brute force attack? #cybersecurity #shorts #brute_force
Daily Dose of Cybersecurity
150 views

2:45
Steganography Tutorial | How To Hide Text Inside The Image | Cybersecurity Training |#steganography
I'M Hacker
25 views

1:00
From AI Sensing to Machine Learning to Post-Quantum Cryptography" #ai #crypto #cybersecurity
World Affairs Council Tacoma
76 views

0:48
Botnet | Info | Cybersecurity | Security Awareness | Karthik SR
Karthik SR Kcyber
189 views

1:26
Cybersecurity Shorts: Day 91 - what is Cryptography ?
Shiva Ram Tech
2.1K views

0:58
What is Digital Signature? cyber security terminology#education #vlrtraining #cybersecurity
VLR Training
3.1K views

51:43
Part 1: Social engineering, malware, and the future of cybersecurity in AI
Google DeepMind
839.3K views
0:28
🚨 Adware Attack Explained in 60 Seconds! | Cybersecurity #Shorts
TalkingBooks Learn & Grow
610 views
0:53
Delete This Info Before Sharing Any Photo! #shorts #cybersecurity #shortvideo
Akanksha Kumari
72 views

43:38
LendTechX 2024 | Panel 3: Guarding the Digital Vault: Cybersecurity Strategies for Lending Platform
Bharat Network Group (BNG)
58 views

4:34
CISSP Stone Cold Memorization: The OSI Model in Domain 4, Network Security #cissp #cybersecurity
Steve McMichael - CPA to Cybersecurity
2.7K views

35:17
Coursera IBM | Cybersecurity Compliance Framework & System Administration | All Week Solutions
Learning Updates
9.7K views
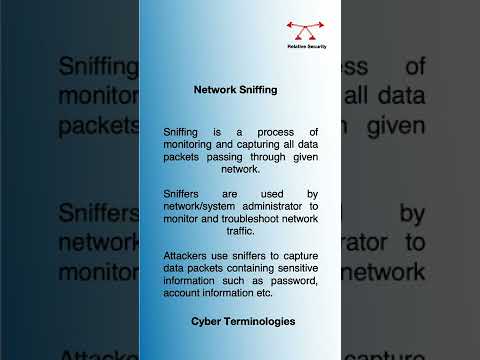
0:25
CyberSecurity Definitions | Sniffing
Relative Security
4.5K views

3:20
What Are Quantum-resistant Algorithms For Future Cybersecurity? - Crisis Response Coach
Crisis Response Coach
1 views
0:47
Types of security attack in cryptography #SecurityAttack #Cybersecurity #Hacking #InfoSec #Shorts
marTech with Neel
100 views

1:12
The Secret Power of Prime Numbers in Cybersecurity
JohnLincolnUSA
85 views

1:41
Cybersecurity Shorts for Executives: The New Chief Information Security Officer
George Mason University Television
210 views

0:36
Salary of a Cybersecurity personnel 💰
Broke Brothers
234.1K views

8:15
Steganography| Mini project| Cybersecurity
Sajid Khan
926 views

0:48
The Hidden Dangers of Steganography in #Cybersecurity #Steganography #Malware
Cyber Bharat
158 views

0:16
Strongest Data Encryption Algorithms #computerscience #cs #cyber #cybersecurity #tech #education
Cyberence
377 views

1:00
What is a Honeypot (Cybersecurity)? Honeypot benefits and risks!
AI Technical
6.1K views

0:40
Unlock the Basics of Cybersecurity: Discover the CIA Triad
Shadownik
66 views

12:11
Cryptography Basics: Intro to Cybersecurity
WhiteboardDoodles
11.8K views

22:04
How Quantum Computers Could Break Encryption and Reshape Cybersecurity, AI, and the Internet
Future of Humanity / Tech & Society
1.0K views
0:28
Ensuring Confidentiality and Non-Repudiation in Messages #shorts #cybersecurity #cissp
CISSP Study Group
454 views

1:03:59
Top Cybersecurity Threats of 2023
LMG Security
1.1K views

0:21
Free Cybersecurity Certification You Can Get in 2025 (No experience required)
Corporate with Deeksha
26.1K views

0:49
What is Password Cyberattack #cybersecurity #shorts #password
Daily Dose of Cybersecurity
147 views

0:22
Cryptography tools | Ethical hacking tools & Software | Cybersecurity tools #ethicalhackingtools
Wasey Tech
267 views

9:56
Types Of Cybercrime In Cyber Security | Cybercrimes & Its Types | Cybersecurity Tutorial|Simplilearn
Simplilearn
28.9K views

0:39
How Hackers REALLY Crack Passwords (It's NOT What You Think) 🤔 #cyberhack #cybersecurity #tech
codewithloves
1.4M views
0:30
Cybersecurity Architects: Building Your Digital Fortress Smart
CyberSecurity Summary
81 views

0:59
Types of Cybersecurity Software
Cybersecurity Research
71 views

0:42
Introduction to Cryptography - ROT13 #shorts #cybersecurity
Penguin Fortress - Cybersecurity Information
183 views
2:35
Q-Day Explained:The Day Quantum Computers Break All Encryption! | Biggest Cybersecurity Threat Ahead
Fortify Solutions
1.1K views

0:44
How Encryption works & Protect Your Data #HowEncryptionWorks #DataPrivacy #CyberSecurity #Encryption
FactFusion
906 views

8:56
Ihr habt ein FALSCHES BILD vom Job CYBERSECURITY
The Morpheus Tutorials
76.3K views
0:14
What is the difference between symmetric and asymmetric encryption? #quiz #cybersecurity
Cybersecurity Training
5 views

1:00
Effectualnary Shorts - Cybersecurity Keyword Learning - ES046 Cryptanalysis
Effectualness
22 views

0:59
Asymmetric Cryptography 🔐 #cybersecurity #shorts
TheQuirky-ishTutor
322 views

0:41
Symmetric Encryption Explained - Types of Encryption - Harsh Nagar - Cybersecurity
Harsh Nagar
763 views

34:07
Software Security | Cybersecurity Specialization | Coursera | Week 1 to 6 | Course 2 Quiz Answers
Learning Updates
3.3K views

0:52
Decoding Steganography in Cybersecurity: Unseen Data Threats
TechSavvy Plus
28 views

0:40
Asymmetric vs Symmetric Encryption #encryption #cybersecurity
Communinvest
586 views
42:55
What is Post-Quantum Cryptography? | The Future of Cybersecurity | TripleCyber Tech Talk
TripleCyber
361 views
6:10
CTF Topics to Know for ABSOLUTE Beginners | Cybersecurity Series | Kaity Codes
KT Codes
2.7K views

0:09
What is Authentication? #cybersecurity #learn #terms #cyber #security #tech
IT and Cyber Security Definitions
750 views

14:20
Why Cybersecurity is Recession-Proof // AI Hype vs Reality
TechButMakeItReal
64.6K views

6:42
Careers in Cybersecurity
IBM Technology
530.5K views