Search Results for "isc2 cybersecurity"
Find videos related to your search query. Browse through our collection of videos matching "isc2 cybersecurity". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "isc2 cybersecurity"
50 results found

0:25
Understanding the CIA Triad in Cybersecurity! #cyberprotection #cybersecurityawareness #technology
CyberGuardian Academy
889 views

0:06
50 Cybersecurity Project Ideas | Beginner to Advanced
Buddy Security
33.9K views

0:58
CLOUD SECURITY FUNDAMENTALS | TOPIC - 21| #technology #cryptography #cybersecurity #cloudcomputing
SCInformatics
10 views

1:00
5 ways to make money in Cybersecurity!
CodeWithHarry
1.2M views

13:48
stop wasting your time in cybersecurity
Cyb3rMaddy
236.1K views

0:57
Cryptography and encryption techniques🧐😱 #computersecurity #cybersecurity #crypto #tech #shorts
CYBER HEAL
431 views

1:10
Cryptology explained in few words #cybersecurity #shorts #day49 #cryptology
fabulousfav
97 views

0:17
ESP32-DIV in Action 📡 #cybersecurity #esp32 #gadgets
CiferTech
2.1M views

0:34
Ancient Cryptography | Caeser Cipher | #cybersecurity #ethicalhacking #cryptography #bitcoin
Technology Geeks
64 views

32:47
NIST National Cybersecurity Center of Excellence’s Migration to Post-Quantum Cryptography Project
PKI Consortium
193 views

0:35
Cracking The Code - Exploring Secure Hash Algorithms - SHA Short #cybersecurity #hashing
Technically U
1.1K views

2:58
What is a Breach? | Cybersecurity
Aldridge
520 views

0:19
Top 5 Programming Languages for Ethical Hacker 🕵️ #cybersecurity #viral
Cyber Aware Hub
64.8K views

3:17
Quantum Cryptography: Decoding the Future of Cybersecurity
PS Consultorium
62 views

0:48
Dive deep into the enigmatic world of encryption with #Encryption #CyberSecurity #Cryptography #fyp
CyberGlitchTV
450 views

0:49
Discover the future of cybersecurity! #QuantumCryptography #TechRevolution #UnbreakableCodes
FloofChonk
73 views

6:10
Ethical Hacking - Steganography | Hacker Tool | Cybersecurity Training
Computer science and application education hub
349 views

0:59
It's a post quantum encryption world #cybersecurity
Varonis
977 views

3:06
Quantum Chips Transform Cybersecurity - Qryptonic
Qryptonic, LLC
18 views

3:29
How to explore the potential of quantum cryptography for cybersecurity
What is and How to
5 views

11:03
learn DNA Computing and DNA Encryption in Cybersecurity
Computer world
382 views
5:54
7.Use Steganography to Hide Data | Cybersecurity Essentials Lab
Scape
866 views

0:41
What is a brute force attack? #cybersecurity #shorts #brute_force
Daily Dose of Cybersecurity
150 views

2:45
Steganography Tutorial | How To Hide Text Inside The Image | Cybersecurity Training |#steganography
I'M Hacker
25 views

1:00
From AI Sensing to Machine Learning to Post-Quantum Cryptography" #ai #crypto #cybersecurity
World Affairs Council Tacoma
76 views
0:48
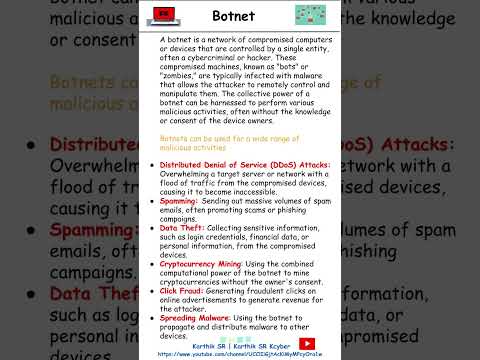
Botnet | Info | Cybersecurity | Security Awareness | Karthik SR
Karthik SR Kcyber
189 views

1:26
Cybersecurity Shorts: Day 91 - what is Cryptography ?
Shiva Ram Tech
2.1K views

0:58
What is Digital Signature? cyber security terminology#education #vlrtraining #cybersecurity
VLR Training
3.1K views

51:43
Part 1: Social engineering, malware, and the future of cybersecurity in AI
Google DeepMind
839.3K views

0:28
🚨 Adware Attack Explained in 60 Seconds! | Cybersecurity #Shorts
TalkingBooks Learn & Grow
610 views
0:53
Delete This Info Before Sharing Any Photo! #shorts #cybersecurity #shortvideo
Akanksha Kumari
72 views

43:38
LendTechX 2024 | Panel 3: Guarding the Digital Vault: Cybersecurity Strategies for Lending Platform
Bharat Network Group (BNG)
58 views

4:34
CISSP Stone Cold Memorization: The OSI Model in Domain 4, Network Security #cissp #cybersecurity
Steve McMichael - CPA to Cybersecurity
2.7K views

35:17
Coursera IBM | Cybersecurity Compliance Framework & System Administration | All Week Solutions
Learning Updates
9.7K views
0:25
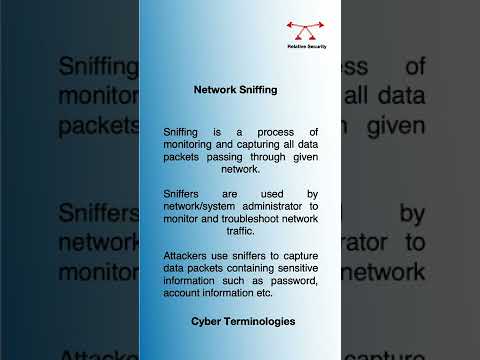
CyberSecurity Definitions | Sniffing
Relative Security
4.5K views

3:20
What Are Quantum-resistant Algorithms For Future Cybersecurity? - Crisis Response Coach
Crisis Response Coach
1 views
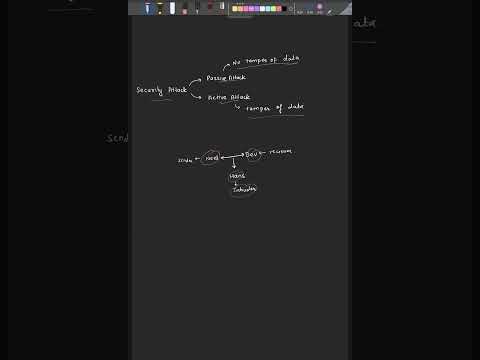
0:47
Types of security attack in cryptography #SecurityAttack #Cybersecurity #Hacking #InfoSec #Shorts
marTech with Neel
100 views

1:12
The Secret Power of Prime Numbers in Cybersecurity
JohnLincolnUSA
85 views

1:41
Cybersecurity Shorts for Executives: The New Chief Information Security Officer
George Mason University Television
210 views

0:36
Salary of a Cybersecurity personnel 💰
Broke Brothers
234.1K views

8:15
Steganography| Mini project| Cybersecurity
Sajid Khan
926 views

0:48
The Hidden Dangers of Steganography in #Cybersecurity #Steganography #Malware
Cyber Bharat
158 views

0:16
Strongest Data Encryption Algorithms #computerscience #cs #cyber #cybersecurity #tech #education
Cyberence
377 views

1:00
What is a Honeypot (Cybersecurity)? Honeypot benefits and risks!
AI Technical
6.1K views

0:40
Unlock the Basics of Cybersecurity: Discover the CIA Triad
Shadownik
66 views

12:11
Cryptography Basics: Intro to Cybersecurity
WhiteboardDoodles
11.8K views

22:04
How Quantum Computers Could Break Encryption and Reshape Cybersecurity, AI, and the Internet
Future of Humanity / Tech & Society
1.0K views
0:28
Ensuring Confidentiality and Non-Repudiation in Messages #shorts #cybersecurity #cissp
CISSP Study Group
454 views

1:03:59
Top Cybersecurity Threats of 2023
LMG Security
1.1K views

0:21
Free Cybersecurity Certification You Can Get in 2025 (No experience required)
Corporate with Deeksha
26.1K views