Search Results for "Malware-based Phishing"
Find videos related to your search query. Browse through our collection of videos matching "Malware-based Phishing". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Malware-based Phishing"
54 results found

7:14
How Hackers Steal Instagram Passwords – Phishing & Social‑Engineering Explained
CyberMind Lab
293 views
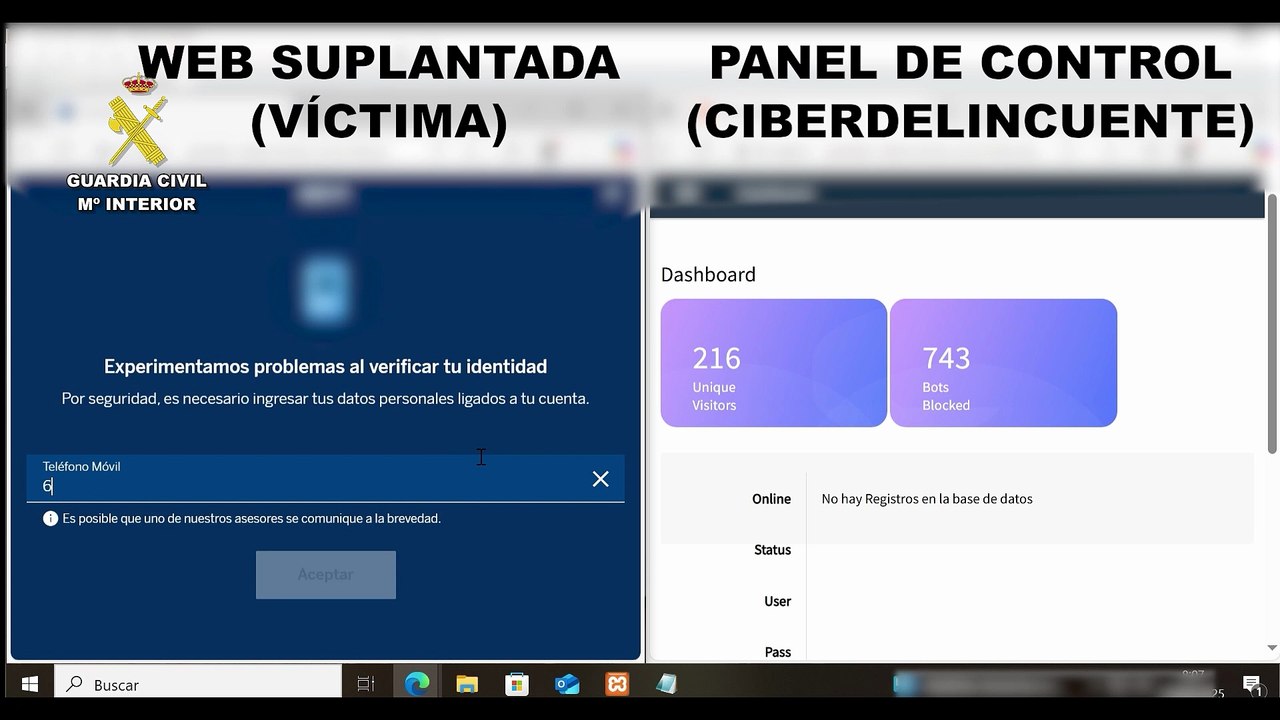
0:50
Phishing Entidades
elDiario.es
10.7K views

0:59
What is Phishing in 60 Seconds
NextWebWorld
31 views

39:02
Laptop Buyer's Guide, PSN Spear Phishing, Affordable 50" HDTV: Panasonic Viera ST30 Review, The Best Upgrade Ever, Secure Browsing Tips! - Tekzilla
Tekzilla
946 views
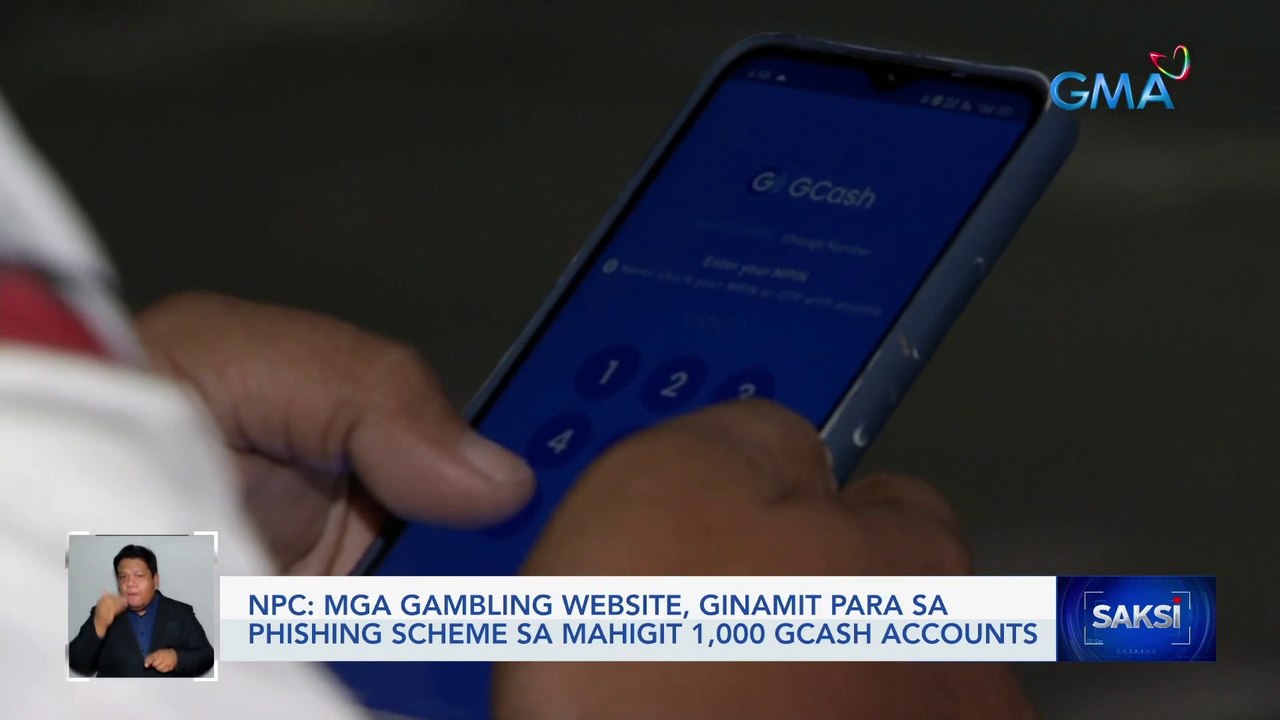
0:58
Mga gambling website, ginamit para sa phishing scheme sa mahigit 1,000 Gcash accounts — NPC | Saksi
GMA Integrated News
328 views

2:56
PointsBet Issues Statements On Cryptocurrency Phishing Emails
SportsGrid
1.6K views

0:49
Attention : nouvelle vague de phishing visant les abonnés Free 🚨
B.E.N Corp
370 views

3:53
Allarme phishing: il punto di Salvo Sottile
Chronist.it
1.0K views

1:29
Spam, phishing, arnaque mail : comment s'en protéger ?
Capital
7.4K views

4:34
Comment se protéger contre le phishing | Speech
Konbini
276 views

1:14
Russian Hackers Caught Meddling in Western Elections as Two Are Indicted in ‘Sophisticated Spear Phishing’ Campaign
Veuer
2.5K views

2:02
Apa Itu Voice Phishing dan Cara Menghindarinya?
RiauOnline.co.id
1.5K views

1:21
Spam, phishing, arnaque mail : comment s'en protéger ? (1)
Capital
54.0K views

4:01
Ransomware and Crypto-Malware - CompTIA Security+ SY0-501 - 1.1
Professor Messer
366.5K views

0:35
🚨How Hidden Malware Sneaks into Your Files! #shortvideo #shorts #new #hacker
Beyond The Firewall
97 views

51:43
Part 1: Social engineering, malware, and the future of cybersecurity in AI
Google DeepMind
839.3K views

0:30
New Malware 'Koske' Uses Steganography to Hide in Images: Protect Your Linux System
Hacked dAily
850 views

1:00
Creating malicious software in Python. Pt:1 #Python #malware #linode #IT #tech #code #coding
NetworkChuck Academy
119.1K views
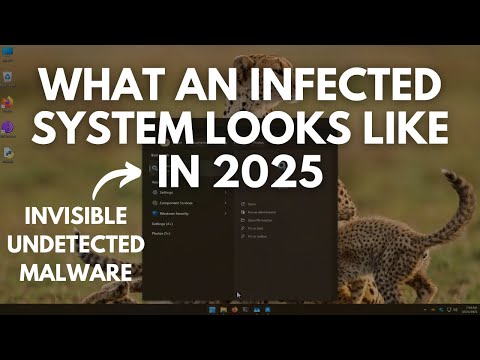
8:16
Malware of the Future: What an infected system looks like in 2025
PC Security Channel
878.6K views

0:48
The Hidden Dangers of Steganography in #Cybersecurity #Steganography #Malware
Cyber Bharat
158 views

57:16
Hiding In Plain Sight - Advances In Malware Covert Communication Channels
Black Hat
5.4K views

9:45
Ethical Hacking Course Series 3: Steganography, Cryptography, Android Hacking, Kali Linux, Malware
KJR CYBER TECH
26 views

8:11
What is Ransomware | Types of Ransomware | Cryptovirology and Cryptography | Malware and its Types
World Walk
264 views

5:27
How to remove adware from chrome । How to remove skilled marketing from mac, #adware #malware
Make Me Skilled
155 views

25:48
I Tested Suspicious Phone App Malware (again)
Tranium
4.6M views
0:41
Hackers Can Hide Malware in Images! (Steganography Explained)
Byte Secure
1.8K views
1:26
#android #virus #adware #malware removed without formatting
whatsupbob
560 views

23:54
I Tested Suspicious Phone App Malware 8
Tranium
1.0M views
17:02
Cyber Crime & Security Explained || Virus Malware Firewall Digital Certificate!!
Great Adib
169 views

3:29
How Is Steganography Used In Malware? - SecurityFirstCorp.com
SecurityFirstCorp
56 views

2:02
Hidden Malware in Images: Steganography Warning
How
79 views

0:58
Kids vs. MALWARE!!
NetworkChuck
9.7M views

3:05
Stuck in Traffic - Steganography and Malware
J Wolfgang Goerlich
602 views

1:00
This Guy Installed 1000 Viruses On His Laptop. #antivirus #malware #download
MSTechSnap
19.7M views

0:16
Steganography Analysis Reveals Hidden Malware in PNG File Using pngdump.py
Secure Thread
236 views

0:36
Cybercriminals Use Steganography to Hide Malware in Images
Hacked dAily
538 views
0:36
Rover Is The Most Dangerous Desktop Assistant ☠️ #malware #virus #tech
CYBER SOLDIER
625.1K views
9:08
Malware and its types l Virus, Worms, Trojan, Ransomware, Adware and Spyware Explained in Hindi
5 Minutes Engineering
107.4K views

17:36
I Tested Malware Against Smartphones
Crypto NWO
4.9M views

0:39
The SCARIEST And DANGEROUS Malware ☠️ (Hexa Ransomware)
CYBER SOLDIER
111.6K views
0:58
How Hackers Use GIFs to Inject Malware! (Steganography Attack!)
Byte Secure
775 views
0:50
RC5 Shellcode Encryption #malware #programming #cryptography #coding #encryption
0x12 Dark Development
1.4K views
2:45
DANGEROUS AI Malware Hides in JPEGs🚨
David Bombal
63.3K views

7:12
Malware | Cryptography and System Security
Ekeeda
27 views

19:22
I Tested Malware Against Smartphones 2
Crypto NWO
1.6M views

2:56
How to Remove ADWARE MALWARE VIRUS on MAC OS X for FREE works on iMac, MacBook Pro & MacBook Air
Shani Jaf
37.0K views

21:25
The Evolution of Malware: Past, Present, and the AI-Driven Future
IBM Technology
63.0K views

12:26
How To Remove All Mac Viruses, Malware, Adware, & Spyware | Full Deep Clean & Maintenance 2023
Full Speed Mac & PC
147.7K views
2:43
Adware.GenericKD Malware Explained & Removal Guide
How To Fix Guide
71 views

19:32
I Tested Suspicious Phone App Malware 7
Tranium
381.2K views

2:46
Pourquoi les cybermenaces ont de l'avenir
Mot 2 Passe
2.0K views

1:17
DeepSeek: malware usa la popularidad de esta IA para atacar a usuarios en línea
El Economista
2.9K views

0:38
Phishing 101: How to Recognize and Protect Yourself from Cyber Scams 🎯
Badea3
205 views

0:42
Protégez-vous contre le phishing en 2024 avec la campagne Voilà ! 🔐
Cybermalveillance.gouv.fr
23.8K views