Secure Your Hardware: Why Anti-Tampering Measures Are Essential for a Robust Root of Trust 🔒
Discover the critical importance of anti-tampering design in strengthening the hardware root of trust, safeguarding your device's security foundation against attacks and unauthorized access.

PUFsecurity Corp.
2.0K views • Apr 11, 2022
About this video
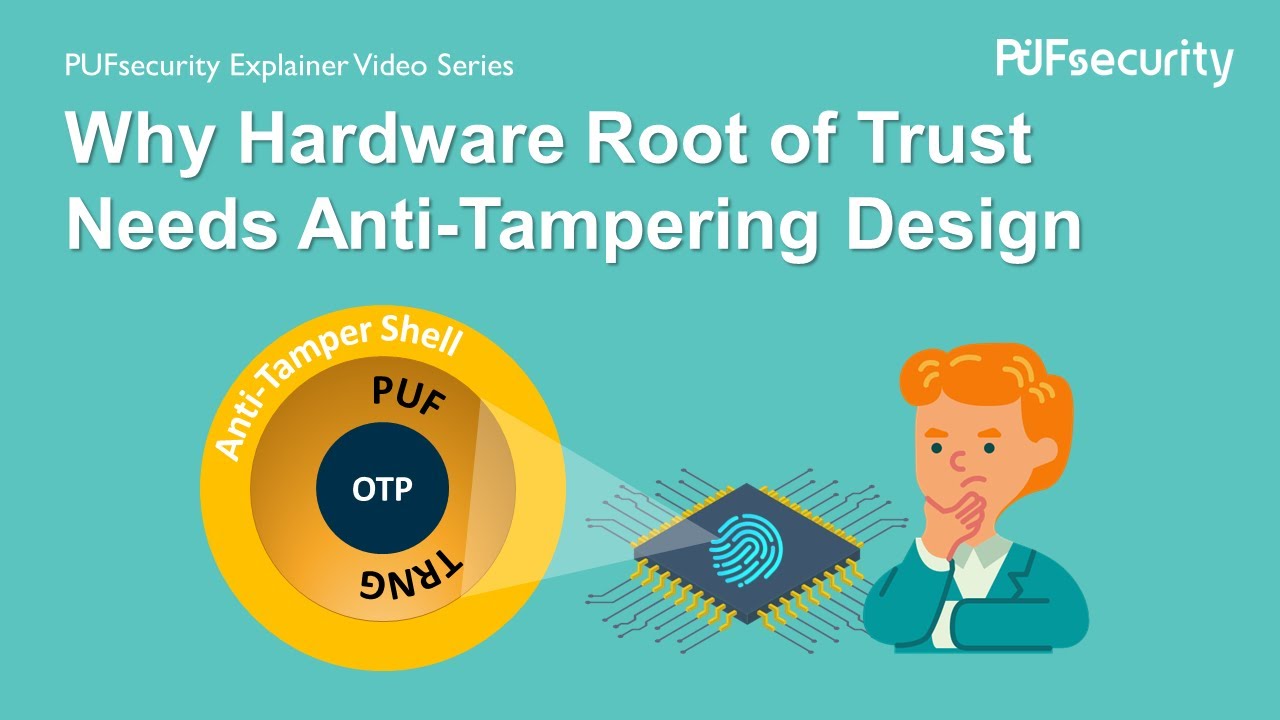
The hardware root of trust (HRoT) provides the trust base (root key), hardware identifier (UID), hardware unique key (HUK), and entropy required for the secure operation of the entire chip and therefore is often the focus of hacker attacks. If the design can’t effectively resist attacks, hackers can easily obtain the secrets of the entire chip. Attackers can use the secrets to crack identity authentication and data encryption and steal product design know-how, causing application security problems.
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
2.0K
Likes
24
Duration
7:38
Published
Apr 11, 2022
User Reviews
4.3
(2) Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.