Mastering DID Document Security: Who Controls and How to Detect Tampering 🔍
Learn how to identify who controls a Decentralized Identifier (DID) and spot signs of tampering. This quick guide simplifies DID document management and security.

LF Decentralized Trust
187 views • Oct 6, 2025
About this video
Description:
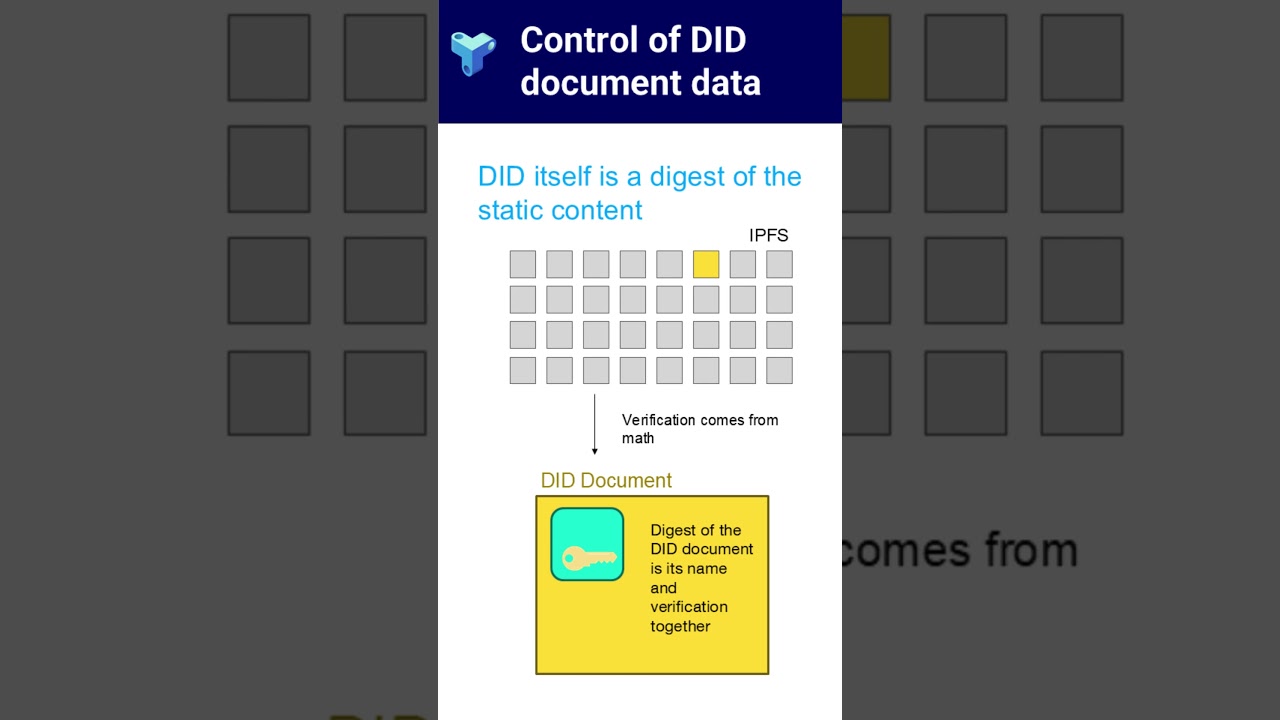
Who controls a Decentralized Identifier — and how can you tell if a DID document has been tampered with? 🧩
In this short explainer, we break down how different DID methods handle control and updates: from simple web-based identifiers to blockchain-anchored and tamper-evident systems. You’ll learn why trusting a DID document isn’t enough — and how verifying the cryptographic evidence behind it really works.
🔹 Learn what makes DIDs secure
🔹 Understand the role of the DID method
🔹 See why not all DIDs are equally verifiable
Whether you’re exploring decentralized identity, verifiable credentials, or Web5 concepts, this video helps you understand one of the most important questions in digital trust: who really controls a DID?
LF Decentralized Trust is the premier open source foundation for collaborative development of a broad range of technologies and standards that deliver the transparency, reliability, security, and efficiency required for a digital-first economy.
Join the conversation on Discord: https://discord.gg/dYtPHgVsCp
Learn more: https://www.lfdecentralizedtrust.org/
#TrustoverIP #bitesizetrust #DID #DecentralizedIdentity #DigitalIdentity
Who controls a Decentralized Identifier — and how can you tell if a DID document has been tampered with? 🧩
In this short explainer, we break down how different DID methods handle control and updates: from simple web-based identifiers to blockchain-anchored and tamper-evident systems. You’ll learn why trusting a DID document isn’t enough — and how verifying the cryptographic evidence behind it really works.
🔹 Learn what makes DIDs secure
🔹 Understand the role of the DID method
🔹 See why not all DIDs are equally verifiable
Whether you’re exploring decentralized identity, verifiable credentials, or Web5 concepts, this video helps you understand one of the most important questions in digital trust: who really controls a DID?
LF Decentralized Trust is the premier open source foundation for collaborative development of a broad range of technologies and standards that deliver the transparency, reliability, security, and efficiency required for a digital-first economy.
Join the conversation on Discord: https://discord.gg/dYtPHgVsCp
Learn more: https://www.lfdecentralizedtrust.org/
#TrustoverIP #bitesizetrust #DID #DecentralizedIdentity #DigitalIdentity
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
187
Likes
1
Duration
2:01
Published
Oct 6, 2025
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.