Unlocking the Secrets of Symmetric Key Cryptography 🔐
Discover how symmetric key algorithms protect your data's confidentiality and integrity. Learn essential cybersecurity strategies to prevent breaches and secure sensitive information.

Naresh KSHETRI
187 views • Jul 21, 2024
About this video
#cybersecurity #databreach #datarisk #cybersecuritygoals #breachimpact #cryptography #confidentiality #integrity #authentication #nonrepudiation #symmetriccryptography #ecdhpalgorithm #privatekey #secretkeys #alicebob #moderncryptography #algorithms
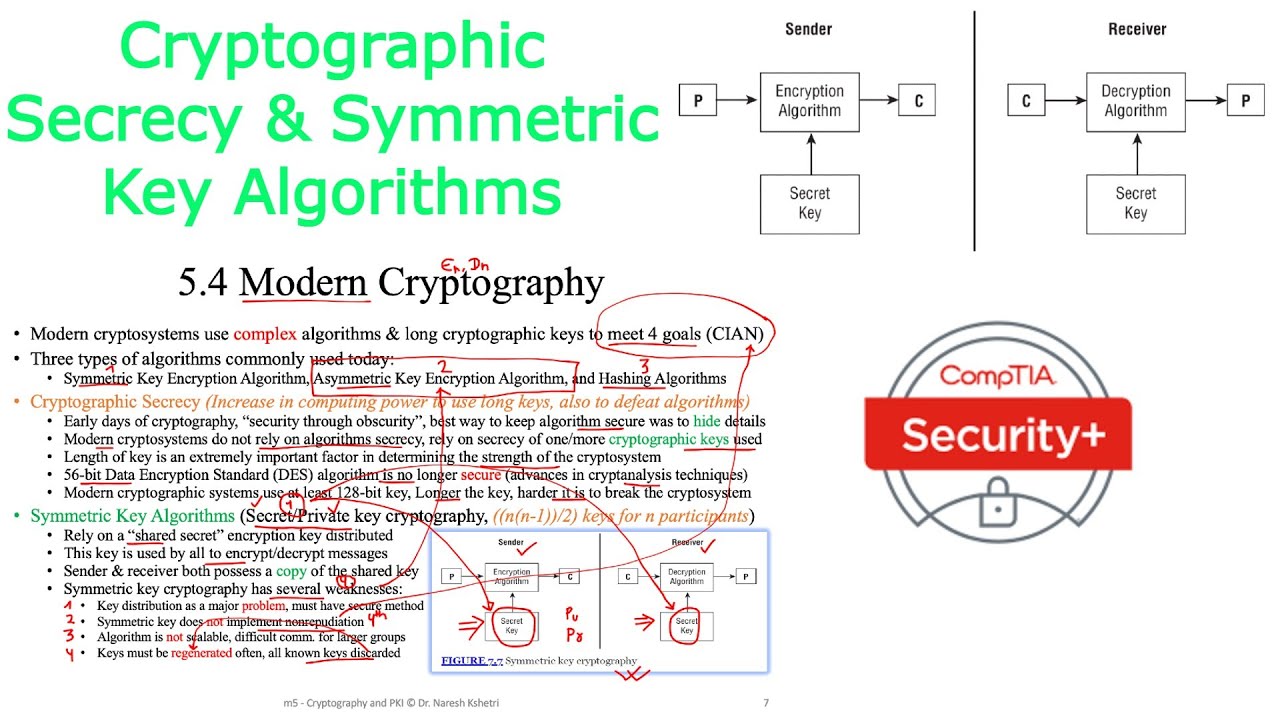
* Hello everyone, welcome back, in this video, I am explaining modern cryptography with three types of algorithms (Symmetric Key, Asymmetric Key, Hashing) commonly used today !
* Cryptographic Secrecy & Symmetric Key (secret / private key) Algorithms
^ Early days of cryptography, “security through obscurity”
^ Best way to keep algorithm secure was to hide details
^ Modern cryptosystems do not rely on algorithms secrecy
^ Rely on secrecy of one/more cryptographic keys used
^ Length of key is an extremely important factor in determining the strength of the cryptosystem
^ 56-bit Data Encryption Standard (DES) algorithm is no longer secure
^ Several advances in cryptanalysis techniques
^ Modern cryptographic systems use at least 128-bit key
^ Longer the key, harder it is to break the cryptosystem
^ Symmetric cryptography rely on a “shared secret” encryption key distributed
^ This key is used by all members to encrypt / decrypt messages
^ Sender & receiver both possess a copy of the shared key
^ Symmetric key cryptography has several weaknesses
* YouTube channel link: https://www.youtube.com/@NareshKSHETRI
* Cybersecurity playlist in my Channel: https://www.youtube.com/playlist?list=PL7-xjgCdZq85ZwT6L6UHLc39rGGGX60Wc
* LinkedIn (let us connect): https://www.linkedin.com/in/NareshKshetri/
* Website (Google Sites): https://sites.google.com/view/NareshKshetri
* Please like, share, & subscribe if the video was helpful !
* Hello everyone, welcome back, in this video, I am explaining modern cryptography with three types of algorithms (Symmetric Key, Asymmetric Key, Hashing) commonly used today !
* Cryptographic Secrecy & Symmetric Key (secret / private key) Algorithms
^ Early days of cryptography, “security through obscurity”
^ Best way to keep algorithm secure was to hide details
^ Modern cryptosystems do not rely on algorithms secrecy
^ Rely on secrecy of one/more cryptographic keys used
^ Length of key is an extremely important factor in determining the strength of the cryptosystem
^ 56-bit Data Encryption Standard (DES) algorithm is no longer secure
^ Several advances in cryptanalysis techniques
^ Modern cryptographic systems use at least 128-bit key
^ Longer the key, harder it is to break the cryptosystem
^ Symmetric cryptography rely on a “shared secret” encryption key distributed
^ This key is used by all members to encrypt / decrypt messages
^ Sender & receiver both possess a copy of the shared key
^ Symmetric key cryptography has several weaknesses
* YouTube channel link: https://www.youtube.com/@NareshKSHETRI
* Cybersecurity playlist in my Channel: https://www.youtube.com/playlist?list=PL7-xjgCdZq85ZwT6L6UHLc39rGGGX60Wc
* LinkedIn (let us connect): https://www.linkedin.com/in/NareshKshetri/
* Website (Google Sites): https://sites.google.com/view/NareshKshetri
* Please like, share, & subscribe if the video was helpful !
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
187
Likes
6
Duration
7:13
Published
Jul 21, 2024
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.