Understanding SSH: Keys, Encryption, and Practical Applications
SSH (Secure Shell) is the gold standard for securely accessing and managing remote servers. In this video, we’ll break down how SSH works under the hood, why it is essential, and provide real-world examples.

ByteMonk
22.0K views • Aug 12, 2025
About this video
SSH (Secure Shell) is the gold standard for securely accessing and managing remote servers. In this video, we’ll break down how SSH works under the hood, why it replaced Telnet, and how developers and DevOps teams use it every day.
💡 **What you'll learn:**
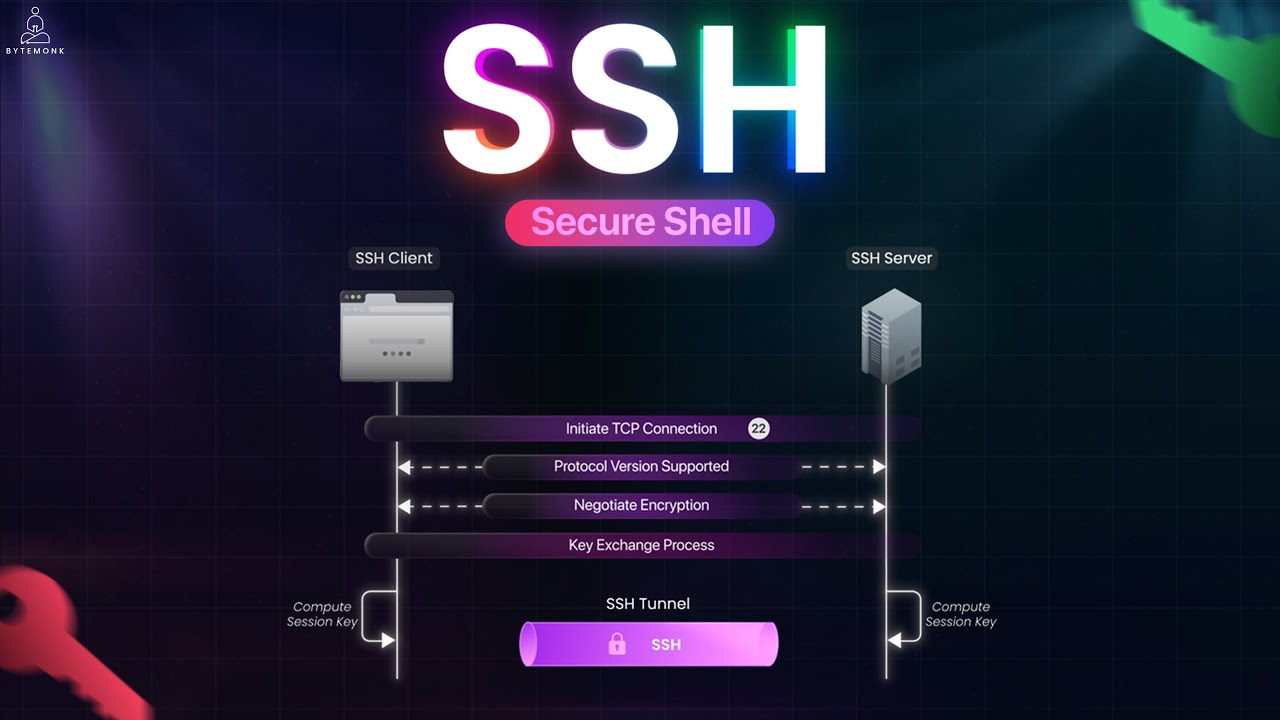
- How SSH establishes a secure, encrypted connection
- SSH vs. Telnet — the postcard vs. locked briefcase analogy
- Key-based authentication vs. passwords
- Real-world examples: AWS EC2 `.pem` files & GitHub SSH keys
- SSH port forwarding (tunneling) for databases & private tools
Whether you’re deploying code, managing servers, or setting up secure automation, this guide will make SSH clear and approachable.
⏱️ Timestamps
00:00 Intro — Why SSH Matters
00:42 What is SSH & Why Use It?
01:35 SSH vs Telnet (Secure vs Insecure Shell)
02:26 How SSH Works — Encryption & Key Exchange
04:15 Authenticating with SSH — Keys vs Passwords
05:18 Real-World Example: AWS EC2 .pem File
06:05 Real-World Example: GitHub SSH Keys
06:42 SSH Local Port Forwarding (Tunneling)
https://www.linkedin.com/in/bytemonk/
https://www.youtube.com/playlist?list=PLJq-63ZRPdBt423WbyAD1YZO0Ljo1pzvY
https://www.youtube.com/playlist?list=PLJq-63ZRPdBssWTtcUlbngD_O5HaxXu6k
https://www.youtube.com/playlist?list=PLJq-63ZRPdBu38EjXRXzyPat3sYMHbIWU
https://www.youtube.com/playlist?list=PLJq-63ZRPdBuo5zjv9bPNLIks4tfd0Pui
https://www.youtube.com/playlist?list=PLJq-63ZRPdBsPWE24vdpmgeRFMRQyjvvj
https://www.youtube.com/playlist?list=PLJq-63ZRPdBslxJd-ZT12BNBDqGZgFo58
AWS Certification:
AWS Certified Cloud Practioner: https://youtu.be/wF1pldkQrOY
AWS Certified Solution Architect Associate: https://youtu.be/GzomXNLFgkk
AWS Certified Solution Architect Professional: https://youtu.be/KFZrBxSA9tI
#SSH #SecureShell #SystemDesign #Cybersecurity #RemoteAccess #Encryption #Authentication #PortForwarding #Telnet
💡 **What you'll learn:**
- How SSH establishes a secure, encrypted connection
- SSH vs. Telnet — the postcard vs. locked briefcase analogy
- Key-based authentication vs. passwords
- Real-world examples: AWS EC2 `.pem` files & GitHub SSH keys
- SSH port forwarding (tunneling) for databases & private tools
Whether you’re deploying code, managing servers, or setting up secure automation, this guide will make SSH clear and approachable.
⏱️ Timestamps
00:00 Intro — Why SSH Matters
00:42 What is SSH & Why Use It?
01:35 SSH vs Telnet (Secure vs Insecure Shell)
02:26 How SSH Works — Encryption & Key Exchange
04:15 Authenticating with SSH — Keys vs Passwords
05:18 Real-World Example: AWS EC2 .pem File
06:05 Real-World Example: GitHub SSH Keys
06:42 SSH Local Port Forwarding (Tunneling)
https://www.linkedin.com/in/bytemonk/
https://www.youtube.com/playlist?list=PLJq-63ZRPdBt423WbyAD1YZO0Ljo1pzvY
https://www.youtube.com/playlist?list=PLJq-63ZRPdBssWTtcUlbngD_O5HaxXu6k
https://www.youtube.com/playlist?list=PLJq-63ZRPdBu38EjXRXzyPat3sYMHbIWU
https://www.youtube.com/playlist?list=PLJq-63ZRPdBuo5zjv9bPNLIks4tfd0Pui
https://www.youtube.com/playlist?list=PLJq-63ZRPdBsPWE24vdpmgeRFMRQyjvvj
https://www.youtube.com/playlist?list=PLJq-63ZRPdBslxJd-ZT12BNBDqGZgFo58
AWS Certification:
AWS Certified Cloud Practioner: https://youtu.be/wF1pldkQrOY
AWS Certified Solution Architect Associate: https://youtu.be/GzomXNLFgkk
AWS Certified Solution Architect Professional: https://youtu.be/KFZrBxSA9tI
#SSH #SecureShell #SystemDesign #Cybersecurity #RemoteAccess #Encryption #Authentication #PortForwarding #Telnet
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
22.0K
Likes
990
Duration
7:36
Published
Aug 12, 2025
User Reviews
4.6
(4) Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now