Understanding SHA-512: A Secure Hash Algorithm for Enhanced Network Security 🔐
Learn how SHA-512 works with detailed block diagrams, round functions, and text processing methods. Discover its role in cryptography and network security to protect your data effectively.

t v nagaraju Technical
174.9K views • Aug 11, 2019
About this video
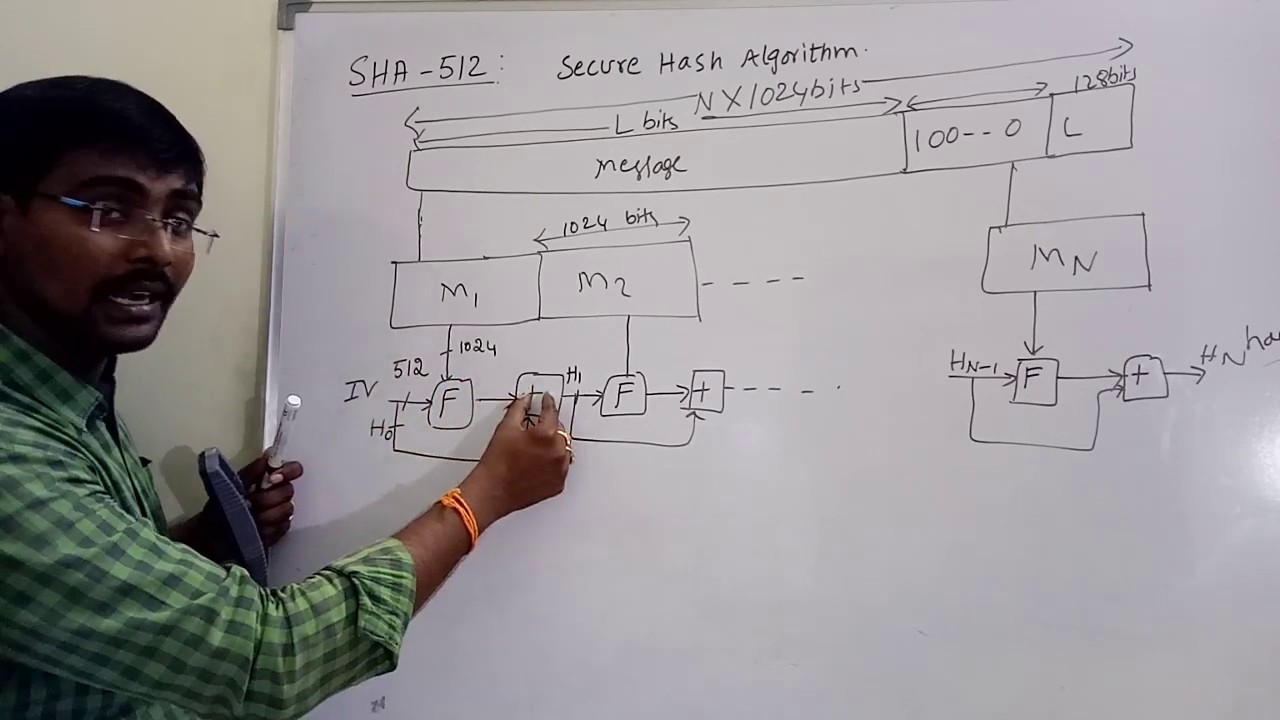
Secure hash algorithm(SHA)-512 implementation with block diagram, round function and generation of words from the text etc.It is a cryptographic hash algorithm and it is authentication algorithm.
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
174.9K
Likes
2.1K
Duration
26:58
Published
Aug 11, 2019
User Reviews
4.5
(34) Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now