Understanding Encryption & Public Key Encryption 🔐: A Complete Guide
Discover the fundamentals of encryption and how public key encryption secures your data. Learn everything you need to know in this detailed explanation.

Programmers Bond
93 views • Jun 14, 2023
About this video
What Is Encryption? Public Key Encryption? Explained In Detail
About Video:-
Encryption schemes are vital tools used to secure sensitive information and protect it from unauthorized access or interception. These schemes employ complex mathematical algorithms to transform plaintext into ciphertext, rendering it unintelligible to anyone without the appropriate decryption key. Encryption is widely used in various applications, including data transmission, storage, and communication channels.
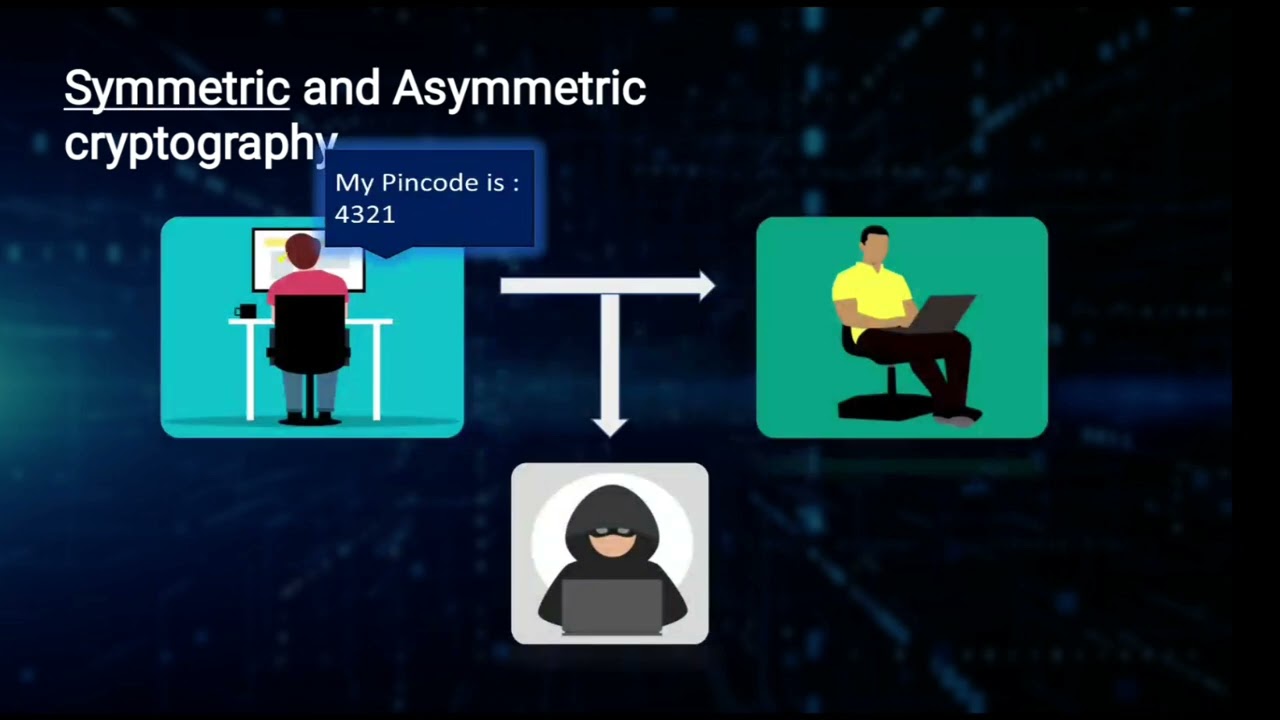
One commonly used encryption scheme is symmetric encryption, where the same key is used for both encryption and decryption processes. The sender and the recipient must possess and share this key securely to ensure confidentiality. Symmetric encryption algorithms, such as the Advanced Encryption Standard (AES), are known for their efficiency and ability to encrypt large amounts of data rapidly.
Another widely used encryption scheme is asymmetric encryption, also known as public-key encryption. Asymmetric encryption employs a pair of mathematically related keys: a public key and a private key. The public key is freely distributed and used for encryption, while the private key is kept secret and used for decryption. This scheme allows secure communication between parties who have never previously interacted and eliminates the need for key distribution. The most commonly used asymmetric encryption algorithm is the RSA algorithm.
In addition to symmetric and asymmetric encryption, there are also hybrid encryption schemes that combine the benefits of both approaches. Hybrid encryption often involves using symmetric encryption to encrypt the actual data, while the symmetric key itself is encrypted using asymmetric encryption. This approach combines the efficiency of symmetric encryption with the convenience of asymmetric encryption for secure key exchange.
Encryption schemes also encompass various modes of operation, such as Electronic Codebook (ECB), Cipher Block Chaining (CBC), and Galois/Counter Mode (GCM). These modes determine how encryption and decryption are applied to blocks of data, adding additional security features like randomness, integrity, and authentication.
To ensure the robustness and security of encryption schemes, they undergo rigorous scrutiny by cryptographic experts and are continuously improved to withstand evolving threats. However, as computing power advances, encryption schemes may become vulnerable to brute-force attacks or breakthroughs in mathematical algorithms. Therefore, it is crucial to regularly update encryption schemes and adhere to best practices to maintain the confidentiality and integrity of sensitive information in an ever-changing digital landscape.
Cover topics:-
Encryption schemes
symmetric encryption
asymmetric encryption
public-key encryption
Advanced Encryption Standard (AES)
RSA algorithm
hybrid encryption
Electronic Codebook (ECB)
Cipher Block Chaining (CBC)
Galois/Counter Mode (GCM)
data security
confidentiality
key distribution
encryption algorithms
decryption
encryption modes
secure communication
cryptographic protocols
brute-force attacks
mathematical algorithms
digital security.
#encryption #internet #technlogy #hindi
About Video:-
Encryption schemes are vital tools used to secure sensitive information and protect it from unauthorized access or interception. These schemes employ complex mathematical algorithms to transform plaintext into ciphertext, rendering it unintelligible to anyone without the appropriate decryption key. Encryption is widely used in various applications, including data transmission, storage, and communication channels.
One commonly used encryption scheme is symmetric encryption, where the same key is used for both encryption and decryption processes. The sender and the recipient must possess and share this key securely to ensure confidentiality. Symmetric encryption algorithms, such as the Advanced Encryption Standard (AES), are known for their efficiency and ability to encrypt large amounts of data rapidly.
Another widely used encryption scheme is asymmetric encryption, also known as public-key encryption. Asymmetric encryption employs a pair of mathematically related keys: a public key and a private key. The public key is freely distributed and used for encryption, while the private key is kept secret and used for decryption. This scheme allows secure communication between parties who have never previously interacted and eliminates the need for key distribution. The most commonly used asymmetric encryption algorithm is the RSA algorithm.
In addition to symmetric and asymmetric encryption, there are also hybrid encryption schemes that combine the benefits of both approaches. Hybrid encryption often involves using symmetric encryption to encrypt the actual data, while the symmetric key itself is encrypted using asymmetric encryption. This approach combines the efficiency of symmetric encryption with the convenience of asymmetric encryption for secure key exchange.
Encryption schemes also encompass various modes of operation, such as Electronic Codebook (ECB), Cipher Block Chaining (CBC), and Galois/Counter Mode (GCM). These modes determine how encryption and decryption are applied to blocks of data, adding additional security features like randomness, integrity, and authentication.
To ensure the robustness and security of encryption schemes, they undergo rigorous scrutiny by cryptographic experts and are continuously improved to withstand evolving threats. However, as computing power advances, encryption schemes may become vulnerable to brute-force attacks or breakthroughs in mathematical algorithms. Therefore, it is crucial to regularly update encryption schemes and adhere to best practices to maintain the confidentiality and integrity of sensitive information in an ever-changing digital landscape.
Cover topics:-
Encryption schemes
symmetric encryption
asymmetric encryption
public-key encryption
Advanced Encryption Standard (AES)
RSA algorithm
hybrid encryption
Electronic Codebook (ECB)
Cipher Block Chaining (CBC)
Galois/Counter Mode (GCM)
data security
confidentiality
key distribution
encryption algorithms
decryption
encryption modes
secure communication
cryptographic protocols
brute-force attacks
mathematical algorithms
digital security.
#encryption #internet #technlogy #hindi
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
93
Likes
8
Duration
10:47
Published
Jun 14, 2023