🔐 Understanding Brute Force Attacks & SHA256 Hashing Explained
Discover how cryptographic hash functions like SHA256 protect your data and learn what brute force attacks are. Perfect for understanding digital security basics!

TechVerseTrends
242 views • Jan 6, 2025
About this video
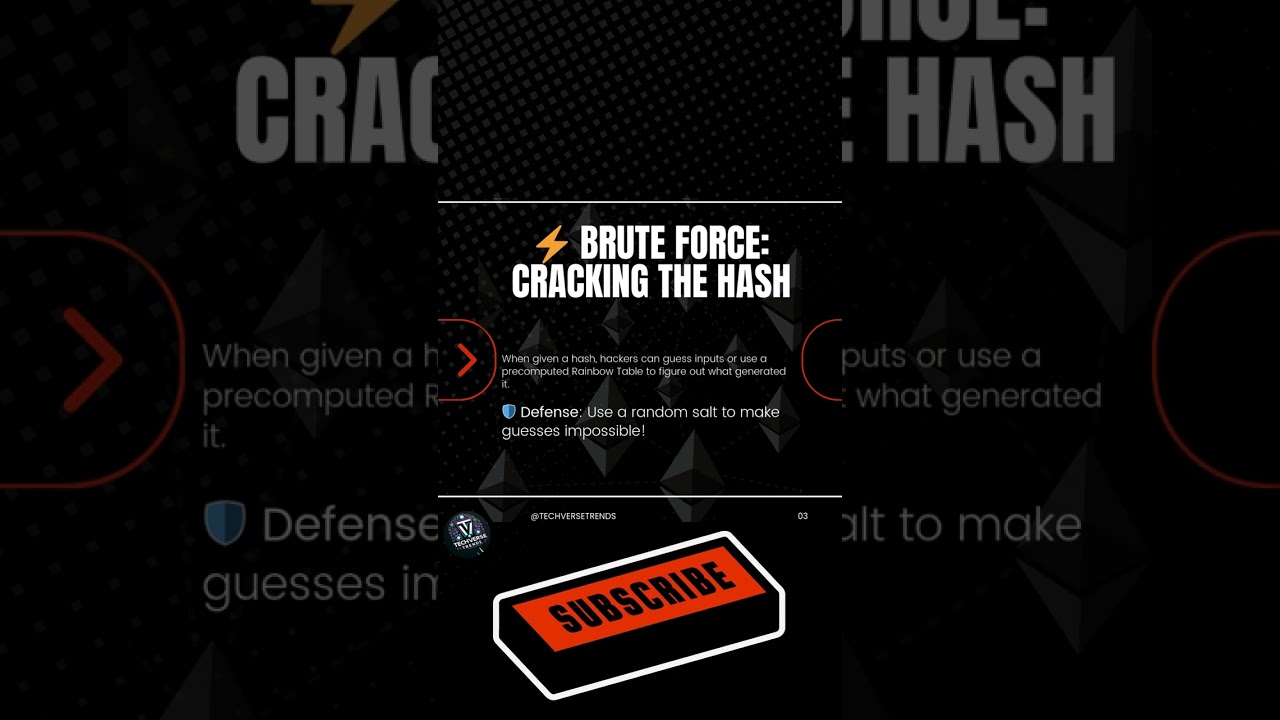
Ever wondered how data is protected in the digital world? Enter cryptographic hash functions like SHA256! These one-way functions transform input into unique, fixed-length hashes that are nearly impossible to reverse. But here’s the twist—hackers can brute-force their way to the original input using precomputed Rainbow Tables or by guessing common inputs. That’s where salting comes in, adding a random, unique value to the input to make cracking it virtually impossible. 🛡️
In our task, we’re unraveling the mystery of a hash by matching it to a color from a predefined list. Using tools like utf8ToBytes, sha256, and toHex, we loop through each possible color, hash it, and compare it to find the match. It’s a fun, hands-on way to see the power of cryptography in action—and understand why it’s so crucial in keeping our digital world secure. Ready to crack the code? 🔐✨
#Cryptography #Hashing #SHA256 #CyberSecurity #CodingLife #LearnToCode #JavaScript #TechEducation
In our task, we’re unraveling the mystery of a hash by matching it to a color from a predefined list. Using tools like utf8ToBytes, sha256, and toHex, we loop through each possible color, hash it, and compare it to find the match. It’s a fun, hands-on way to see the power of cryptography in action—and understand why it’s so crucial in keeping our digital world secure. Ready to crack the code? 🔐✨
#Cryptography #Hashing #SHA256 #CyberSecurity #CodingLife #LearnToCode #JavaScript #TechEducation
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
242
Likes
5
Duration
1:00
Published
Jan 6, 2025
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.