TryHackMe OWASP Top 10 2025: Data Handling Walkthrough
Explore A04, A05, and A08 on insecure data handling with this full TryHackMe walkthrough. 🛡️ Room Link: https://tryhackme.com/room/owasptopten2025three
Djalil Ayed
3.0K views • Nov 16, 2025
About this video
🎯 Learn about A04, A05, and A08 as they related to insecure data handling.
🏷️🏷️ Room Link: https://tryhackme.com/room/owasptopten2025three
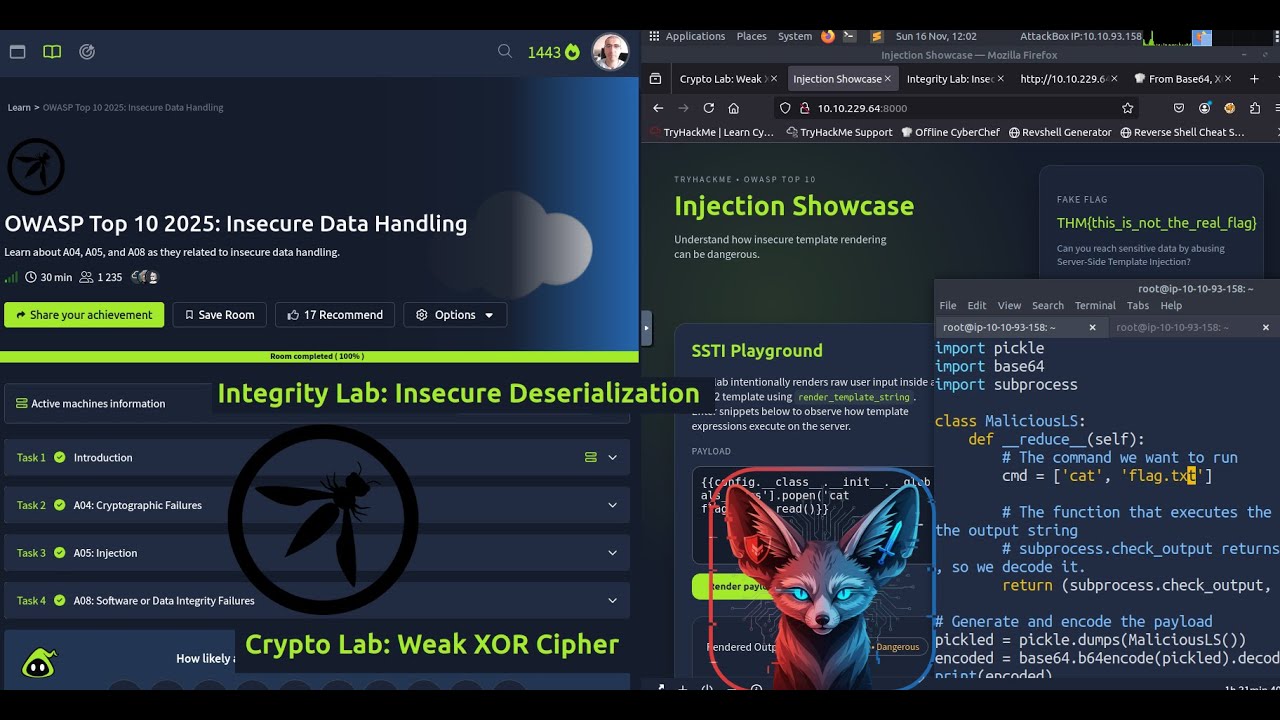
This room will introduce you to 3 elements of the OWASP Top 10 list (2025). In this room, you will learn about the elements relating to application behaviour and user input. We will cover these vulnerabilities briefly, how to prevent them, and finally, you will practice exploiting these vulnerabilities:
📌 A04: Cryptographic Failures
📌A05: Injection
📌 A08: Software or Data Integrity Failures
🎯 Room Tasks: 🎯
[00:00] 🦮 Task 1: Introduction & Lab
[02:05] 🦮 Task 2: A04: Cryptographic Failures
- Decrypt the encrypted notes. One of them will contain a flag value. 🦮 What is it?
[07:45] 🦮 Task 3: A05: Injection
- Perform an SSTI attack on the practical. You need to read the contents of flag.txt that is located within the same directory as the web application.
[11:59] 🦮 Task 4: A08: Software or Data Integrity Failures
- Use Python to pickle a malicious, serialised payload that reads the contents of flag.txt and submits it to the application. What are the contents of flag.txt?
🎯 OWASP Top 10:2025 RC1 : https://owasp.org/Top10/2025/0x00_2025-Introduction/
🎯🎯 Code and commands used on the video: https://github.com/djalilayed/tryhackme/tree/main/OWASP%20Top%2010%202025:%20Insecure%20Data%20Handling
⚠️ Educational Purpose Only
This content is for educational and authorized penetration testing purposes only. Always ensure you have permission before testing on any systems.
Don't forget to 👍 LIKE and 🔔 SUBSCRIBE for more cybersecurity tutorials!
#tryhackme #owasp #owasptop10
🏷️🏷️ Room Link: https://tryhackme.com/room/owasptopten2025three
This room will introduce you to 3 elements of the OWASP Top 10 list (2025). In this room, you will learn about the elements relating to application behaviour and user input. We will cover these vulnerabilities briefly, how to prevent them, and finally, you will practice exploiting these vulnerabilities:
📌 A04: Cryptographic Failures
📌A05: Injection
📌 A08: Software or Data Integrity Failures
🎯 Room Tasks: 🎯
[00:00] 🦮 Task 1: Introduction & Lab
[02:05] 🦮 Task 2: A04: Cryptographic Failures
- Decrypt the encrypted notes. One of them will contain a flag value. 🦮 What is it?
[07:45] 🦮 Task 3: A05: Injection
- Perform an SSTI attack on the practical. You need to read the contents of flag.txt that is located within the same directory as the web application.
[11:59] 🦮 Task 4: A08: Software or Data Integrity Failures
- Use Python to pickle a malicious, serialised payload that reads the contents of flag.txt and submits it to the application. What are the contents of flag.txt?
🎯 OWASP Top 10:2025 RC1 : https://owasp.org/Top10/2025/0x00_2025-Introduction/
🎯🎯 Code and commands used on the video: https://github.com/djalilayed/tryhackme/tree/main/OWASP%20Top%2010%202025:%20Insecure%20Data%20Handling
⚠️ Educational Purpose Only
This content is for educational and authorized penetration testing purposes only. Always ensure you have permission before testing on any systems.
Don't forget to 👍 LIKE and 🔔 SUBSCRIBE for more cybersecurity tutorials!
#tryhackme #owasp #owasptop10
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
3.0K
Likes
61
Duration
17:44
Published
Nov 16, 2025
User Reviews
4.5
(2) Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.