TryHackMe OWASP Top 10 2025: Design Flaws Walkthrough
Explore A02, A03, A06, A10 and their relation to application design flaws in this comprehensive TryHackMe walkthrough. 🔐

Djalil Ayed
7.8K views • Nov 16, 2025
About this video
🎯 Learn about A02, A03, A06, and A10 and how they related to design flaws in the application.
🏷️🏷️ Room Link: https://tryhackme.com/room/owasptopten2025two
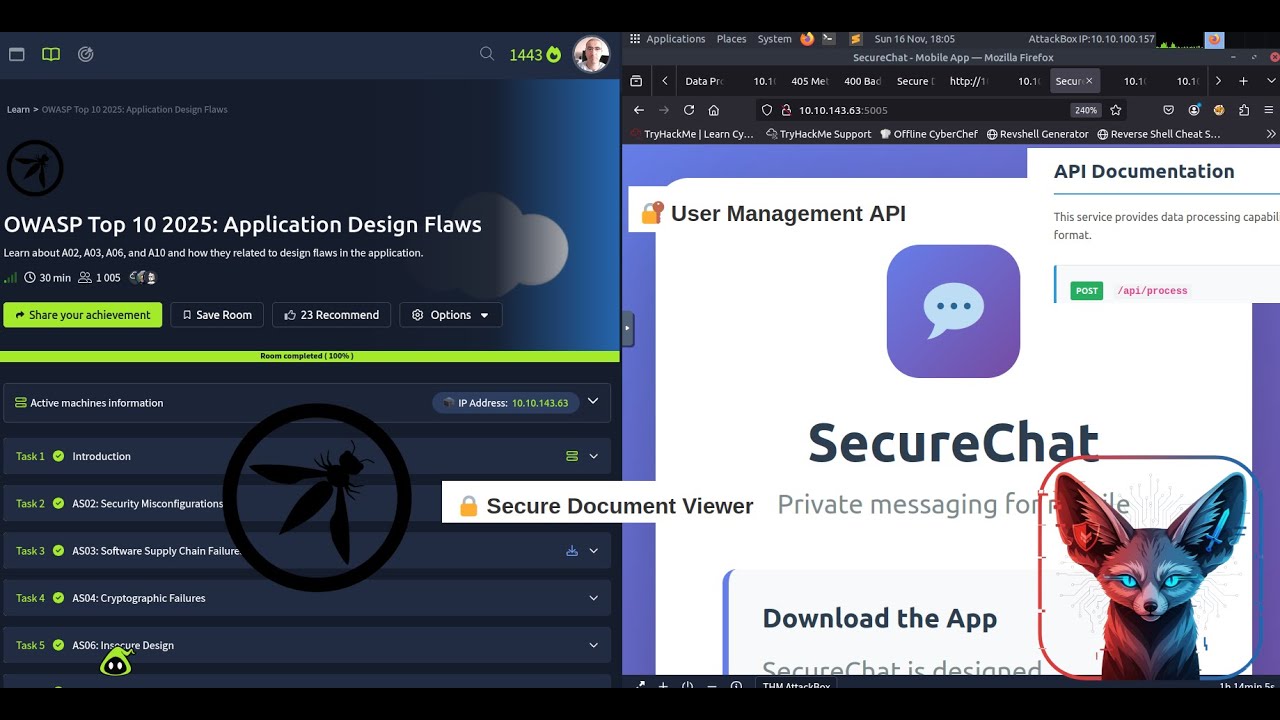
🎯 This room breaks each 4 of the OWASP Top 10 2025 categories. In this room, you will learn about the categories that are related to failures in architecture and system design. You will put the theory into practice by completing supporting challenges. The following categories are covered in this room:
📌 AS02: Security Misconfigurations
📌 AS03: Software Supply Chain Failures
📌 AS04: Cryptographic Failures
📌 AS06: Insecure Design
🎯 Room Tasks: 🎯
🐍 Task 1: Introduction
🐙 Task 2: AS02: Security Misconfigurations
- Navigate to 10[.]10[.]143[.]63[:]5002. It appears that the developers left too many traces in their User Management APIs.
🐧 Task 3: AS03: Software Supply Chain Failures
- Navigate to 10[.]10[.]143[.]63[:]5003. The code is outdated and imports an old lib/vulnerable_utils.py component. Can you debug it?
🐱 Task 4: AS04: Cryptographic Failures
- Navigate to 10[.]10[.]143[.]63[:]5004. Can you find the key to decrypt the file?
👻 Task 5: AS06: Insecure Design
- Navigate to 10[.]10[.]143[.]63[:]5005. Have they assumed that only mobile devices can access it?
🦓 Task 6: Conclusion
🎯 OWASP Top 10:2025 RC1 : https://owasp.org/Top10/2025/0x00_2025-Introduction/
⚠️ Educational Purpose Only
This content is for educational and authorized penetration testing purposes only. Always ensure you have permission before testing on any systems.
Don't forget to 👍 LIKE and 🔔 SUBSCRIBE for more cybersecurity tutorials!
#tryhackme #owasp #owasptop10
🏷️🏷️ Room Link: https://tryhackme.com/room/owasptopten2025two
🎯 This room breaks each 4 of the OWASP Top 10 2025 categories. In this room, you will learn about the categories that are related to failures in architecture and system design. You will put the theory into practice by completing supporting challenges. The following categories are covered in this room:
📌 AS02: Security Misconfigurations
📌 AS03: Software Supply Chain Failures
📌 AS04: Cryptographic Failures
📌 AS06: Insecure Design
🎯 Room Tasks: 🎯
🐍 Task 1: Introduction
🐙 Task 2: AS02: Security Misconfigurations
- Navigate to 10[.]10[.]143[.]63[:]5002. It appears that the developers left too many traces in their User Management APIs.
🐧 Task 3: AS03: Software Supply Chain Failures
- Navigate to 10[.]10[.]143[.]63[:]5003. The code is outdated and imports an old lib/vulnerable_utils.py component. Can you debug it?
🐱 Task 4: AS04: Cryptographic Failures
- Navigate to 10[.]10[.]143[.]63[:]5004. Can you find the key to decrypt the file?
👻 Task 5: AS06: Insecure Design
- Navigate to 10[.]10[.]143[.]63[:]5005. Have they assumed that only mobile devices can access it?
🦓 Task 6: Conclusion
🎯 OWASP Top 10:2025 RC1 : https://owasp.org/Top10/2025/0x00_2025-Introduction/
⚠️ Educational Purpose Only
This content is for educational and authorized penetration testing purposes only. Always ensure you have permission before testing on any systems.
Don't forget to 👍 LIKE and 🔔 SUBSCRIBE for more cybersecurity tutorials!
#tryhackme #owasp #owasptop10
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
7.8K
Likes
152
Duration
39:32
Published
Nov 16, 2025
User Reviews
4.6
(1) Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.