Step-by-Step Guide to Solving an AES Encryption Example 🔐
Learn how to solve a complete AES encryption example with detailed steps. Perfect for understanding the AES transformation process. Follow my blog for more tutorials: https://www.chira...

Chirag Bhalodia
122.1K views • May 26, 2022
About this video
AES Example | AES Encryption Example | AES solved Example | Solved Example of AES encryption | AES Transformation Function
Follow my blog: https://www.chiragbhalodia.com/2021/09/aes-algorithm.html
In this video, I have explained introduction of AES. Then explained all transformation fuctions of AES with example (Example from William Stallings book) is in this video. Watch carefully. AES Solved example.
Introduction of AES:
AES uses 128 bits of plain text. AES consists of multiple rounds of processing different key bits like,
128 bits key – perform 10 rounds of encryption
192 bits key – perform 12 rounds of encryption.
256 bits key – perform 14 rounds of encryption.
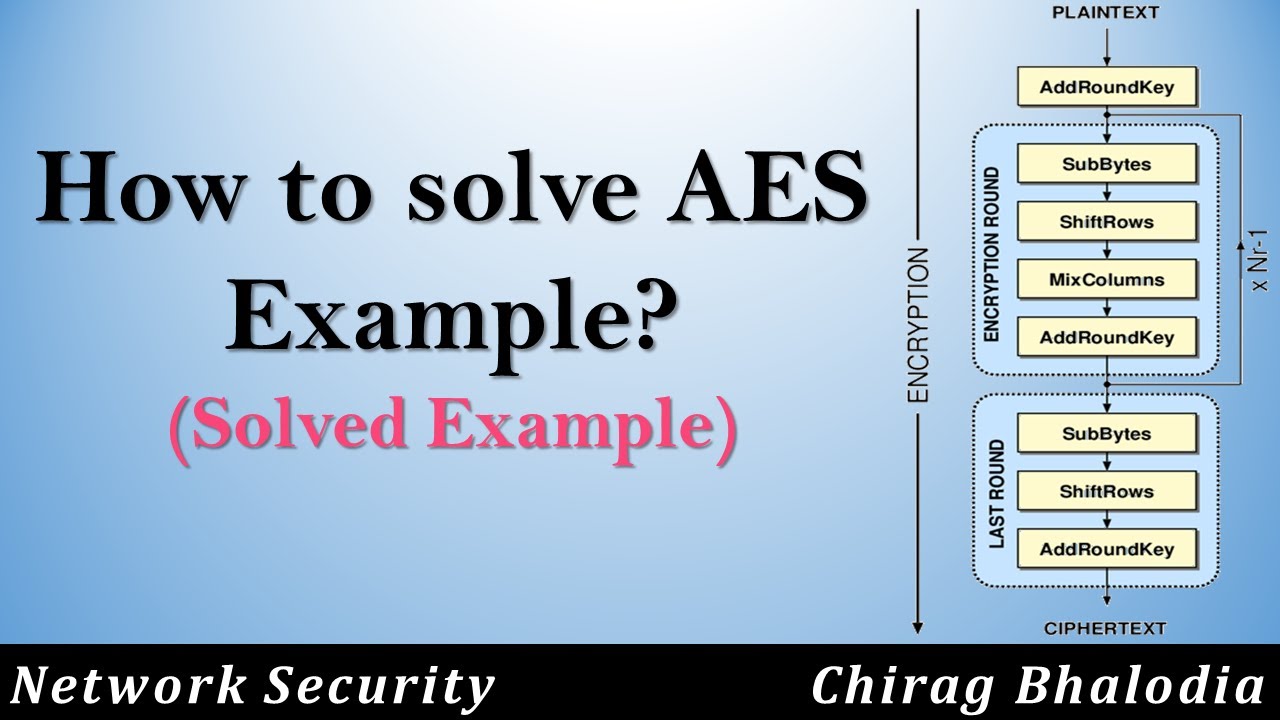
For encryption, each round consists of the following four steps: Sub Bytes,
Shift Rows, Mix Columns, Add Round Key.
Above steps also called AES transformation function.
AES Sub BytesTransformation Function:
First transformation function of AES is called as Substitute Bytes (Sub Bytes). It is also known as forward substitute bytes transformation. AES defines a 16 x 16 matrix of byte values, called an S-box, that contains a permutation of all possible 256 8-bit values. These row and column values serve as indexes into the S-box to select a unique 8-bit output value.
AES Shift Rows Transformation Function:
Second transformation function of AES is called as Shift Rows. It is also called as forward shift row transformation. Rules of shifting rows are as below,
Row 1 ⇒ No Shifting
Row 2 ⇒ 1 byte circular left shift
Row 3 ⇒ 2 bytes circular left shift
Row 4 ⇒ 3 bytes circular left shift
AES Mix Column Transformation Function:
Third transformation function of AES is called as Mix Columns, operates on each column individually. Each byte of a column is mapped into a new value that is a function of all four bytes in that column. Here in this function State Array is Output of Shift Rows function.
AES Add Round Key Transformation Function:
Fourth transformation function of AES is called as Add Round Key. It is also known as forward add round key transformation. The 128 bits of State are bitwise XORed with the 128 bits of the round key. Add Round Key proceeds one column at a time.
0:00 Introduction
0:15 Outline
0:45 Introdcution of AES
2:13 AES Sub Bytes (Explain with example)
5:47 AES Shift Rows (Explain with example)
8:50 AES Mix Column (Explain with example)
32:27 AES Add Round Key (Explain with example)
If you like my video contents, please LIKE, COMMENT, SUBSCRIBE & SHARE with your friends.
--------------------------------------------------------------------------------------------------------------
Check out other video on my channel
Block Cipher and Stream Cipher:
https://youtu.be/-gQrm5j0RkQ
Confusion & Diffusion (Frustrated Statistical Analysis or Claud Shannon Properties):
https://youtu.be/PJrW6ZqQipo
Feistel Cipher Structure (to understand DES):
https://youtu.be/emJ0p6h48u4
Data Encryption Standard (DES) Algorithm:
https://youtu.be/cVhlCzmb-v0
DES Example using Animation:
https://youtu.be/3YBwhWuXZ0o
Strength & Weakness of DES, Avalanche effect in DES:
https://youtu.be/Xy1hver_aaw
Advanced Encryption Standard (AES) Algorithm with structure:
https://youtu.be/X8whYEWoDSI
AES Example using Animation:
https://youtu.be/ZPLEtxxjCYA
Key expansion in AES:
https://youtu.be/14SAn4IEAHk
--------------------------------------------------------------------------------------------------------------
You can always connect with me at:
Follow my blog:
https://www.chiragbhalodia.com
Like my Facebook page:
https://www.facebook.com/chiragbhalodia25
Follow me on Instagram:
https://www.instagram.com/chiragbhalodia.25
Follow me on twitter:
https://twitter.com/chiragsbhalodia
Join telegram group:
https://t.me/chiragbhalodia
Subscribe me on youtube:
https://www.youtube.com/c/ChiragBhalodia
Follow me on Quora:
https://www.quora.com/profile/Chirag-Bhalodia-2
--------------------------------------------------------------------------------------------------------------
Playlist available on my channel:
Network Security (CNS, INS, IS):
https://youtube.com/playlist?list=PLzQqHxFtQGyfiYWaDnasLdy1JPK3JS06o
Computer Network (CN) with animation:
https://youtube.com/playlist?list=PLzQqHxFtQGycfs9Vn8BYy0ic0wh-oL9UC
VFX Animation & Fun Videos:
https://youtube.com/playlist?list=PLzQqHxFtQGyd9esvf-t5XYOKhxQS0tDWx
Comupter Organization & Architecture (COA, CA, CO):
https://youtube.com/playlist?list=PLzQqHxFtQGyd-uDzS9vov8hJfm03X_SzC
Assembly Language Programming:
https://youtube.com/playlist?list=PLzQqHxFtQGyeTa82xQyceYxaf-iyZBICw
Computer Graphics:
https://youtube.com/playlist?list=PLzQqHxFtQGycg_TJBA6uFGDLwbotjs68h
#chirag_bhalodia
#chiragbhalodia
#networksecurity
#cryptography
#AES_Solved_Example
#How_to_solve_aes_example
Keep learning, keep supporting 🤝✨💯
Follow my blog: https://www.chiragbhalodia.com/2021/09/aes-algorithm.html
In this video, I have explained introduction of AES. Then explained all transformation fuctions of AES with example (Example from William Stallings book) is in this video. Watch carefully. AES Solved example.
Introduction of AES:
AES uses 128 bits of plain text. AES consists of multiple rounds of processing different key bits like,
128 bits key – perform 10 rounds of encryption
192 bits key – perform 12 rounds of encryption.
256 bits key – perform 14 rounds of encryption.
For encryption, each round consists of the following four steps: Sub Bytes,
Shift Rows, Mix Columns, Add Round Key.
Above steps also called AES transformation function.
AES Sub BytesTransformation Function:
First transformation function of AES is called as Substitute Bytes (Sub Bytes). It is also known as forward substitute bytes transformation. AES defines a 16 x 16 matrix of byte values, called an S-box, that contains a permutation of all possible 256 8-bit values. These row and column values serve as indexes into the S-box to select a unique 8-bit output value.
AES Shift Rows Transformation Function:
Second transformation function of AES is called as Shift Rows. It is also called as forward shift row transformation. Rules of shifting rows are as below,
Row 1 ⇒ No Shifting
Row 2 ⇒ 1 byte circular left shift
Row 3 ⇒ 2 bytes circular left shift
Row 4 ⇒ 3 bytes circular left shift
AES Mix Column Transformation Function:
Third transformation function of AES is called as Mix Columns, operates on each column individually. Each byte of a column is mapped into a new value that is a function of all four bytes in that column. Here in this function State Array is Output of Shift Rows function.
AES Add Round Key Transformation Function:
Fourth transformation function of AES is called as Add Round Key. It is also known as forward add round key transformation. The 128 bits of State are bitwise XORed with the 128 bits of the round key. Add Round Key proceeds one column at a time.
0:00 Introduction
0:15 Outline
0:45 Introdcution of AES
2:13 AES Sub Bytes (Explain with example)
5:47 AES Shift Rows (Explain with example)
8:50 AES Mix Column (Explain with example)
32:27 AES Add Round Key (Explain with example)
If you like my video contents, please LIKE, COMMENT, SUBSCRIBE & SHARE with your friends.
--------------------------------------------------------------------------------------------------------------
Check out other video on my channel
Block Cipher and Stream Cipher:
https://youtu.be/-gQrm5j0RkQ
Confusion & Diffusion (Frustrated Statistical Analysis or Claud Shannon Properties):
https://youtu.be/PJrW6ZqQipo
Feistel Cipher Structure (to understand DES):
https://youtu.be/emJ0p6h48u4
Data Encryption Standard (DES) Algorithm:
https://youtu.be/cVhlCzmb-v0
DES Example using Animation:
https://youtu.be/3YBwhWuXZ0o
Strength & Weakness of DES, Avalanche effect in DES:
https://youtu.be/Xy1hver_aaw
Advanced Encryption Standard (AES) Algorithm with structure:
https://youtu.be/X8whYEWoDSI
AES Example using Animation:
https://youtu.be/ZPLEtxxjCYA
Key expansion in AES:
https://youtu.be/14SAn4IEAHk
--------------------------------------------------------------------------------------------------------------
You can always connect with me at:
Follow my blog:
https://www.chiragbhalodia.com
Like my Facebook page:
https://www.facebook.com/chiragbhalodia25
Follow me on Instagram:
https://www.instagram.com/chiragbhalodia.25
Follow me on twitter:
https://twitter.com/chiragsbhalodia
Join telegram group:
https://t.me/chiragbhalodia
Subscribe me on youtube:
https://www.youtube.com/c/ChiragBhalodia
Follow me on Quora:
https://www.quora.com/profile/Chirag-Bhalodia-2
--------------------------------------------------------------------------------------------------------------
Playlist available on my channel:
Network Security (CNS, INS, IS):
https://youtube.com/playlist?list=PLzQqHxFtQGyfiYWaDnasLdy1JPK3JS06o
Computer Network (CN) with animation:
https://youtube.com/playlist?list=PLzQqHxFtQGycfs9Vn8BYy0ic0wh-oL9UC
VFX Animation & Fun Videos:
https://youtube.com/playlist?list=PLzQqHxFtQGyd9esvf-t5XYOKhxQS0tDWx
Comupter Organization & Architecture (COA, CA, CO):
https://youtube.com/playlist?list=PLzQqHxFtQGyd-uDzS9vov8hJfm03X_SzC
Assembly Language Programming:
https://youtube.com/playlist?list=PLzQqHxFtQGyeTa82xQyceYxaf-iyZBICw
Computer Graphics:
https://youtube.com/playlist?list=PLzQqHxFtQGycg_TJBA6uFGDLwbotjs68h
#chirag_bhalodia
#chiragbhalodia
#networksecurity
#cryptography
#AES_Solved_Example
#How_to_solve_aes_example
Keep learning, keep supporting 🤝✨💯
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
122.1K
Likes
2.0K
Duration
37:52
Published
May 26, 2022
User Reviews
4.7
(24) Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.