Secure Your Enterprise Data at Rest with Vormetric Encryption Architecture 🔒
Discover how Vormetric's encryption, access control, and auditing solutions safeguard your enterprise data at rest. Read the whitepaper for a comprehensive overview!
Cto Buddy
4 views • Sep 24, 2013
About this video
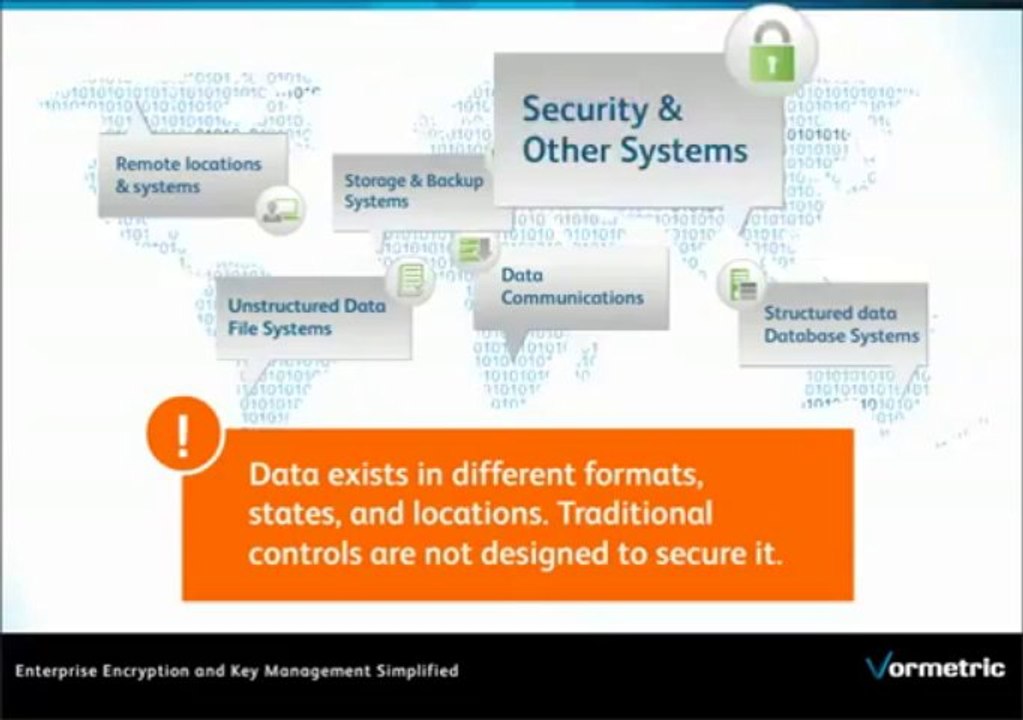
Protecting Enterprise Data with Encryption, Access Control & Auditing <br /><br />Vormetric Encryption Architecture Overview <br /><br />---------------------------------------------------------------------------------- <br /><br />Follow CTOBuddy on Facebook : <br />www.facebook.com/pages/CTOBuddy/163641553830817 <br /><br />Follow CTOBuddy on Twitter : <br />https://twitter.com/CTOBuddy <br /><br />Follow CTOBuddy on Youtube: http://www.youtube.com/channel/UChgnlRj2NPNgAeMRFBWYE_Q?sub_confirmation=1 <br /><br />---------------------------------------------------------------------------------- <br />Whitepaper Link of Vormetric: <br /><br />http://enterprise-encryption.vormetric.com/email-wp-eva-20120911-vormetric-enterprise-encryption-architecture-lp.html <br /><br />--------------------------------------------------------------------------------- <br /><br />This is an excerpt of Vormetric's Encryption Architecture Overview Whitepaper: Protecting Enterprise Data at Rest with Encryption, Access Controls and Auditing <br />More on subject : http://www.vormetric.com/datasecurity82 <br />This Vormetric whitepaper discusses data security threats and related incidents, such as security breaches, which can be harmful to any organization operating online. It then goes on to explain the real risks to the enterprise data and how to make encryption successful. The whitepaper also discusses Vormetric encryption, which is a comprehensive solution for key management and encryption of data at rest. The whitepaper on Vormetric Encryption Architecture consists of brief introduction to two most important components of Vormetric Encryption i.e., Data Security Manager and Encryption Expert Agents. <br />According to whitepaper, some of the advantages of using Vormetric Encryption solution are: <br />• Encryption and Access Controls <br />• Transparent Implementation <br />• High Performance <br />• Centralized Key and Policy Management <br />• Strong Separation of Duties <br />• Role-Based Administration and Domains <br />• Scalability <br />• Distributed IT Environments <br />• High Availability <br />• Fine-Grained Auditing
Video Information
Views
4
Duration
2:29
Published
Sep 24, 2013
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.