Passive Attacks in Cybersecurity: Easy to Launch, Hard to Detect 🔍
Discover how passive attacks work from an attacker’s perspective, why they are appealing, and their limitations. A quick and insightful cybersecurity overview! #shorts

Security For You
2.1K views • Jun 15, 2025
About this video
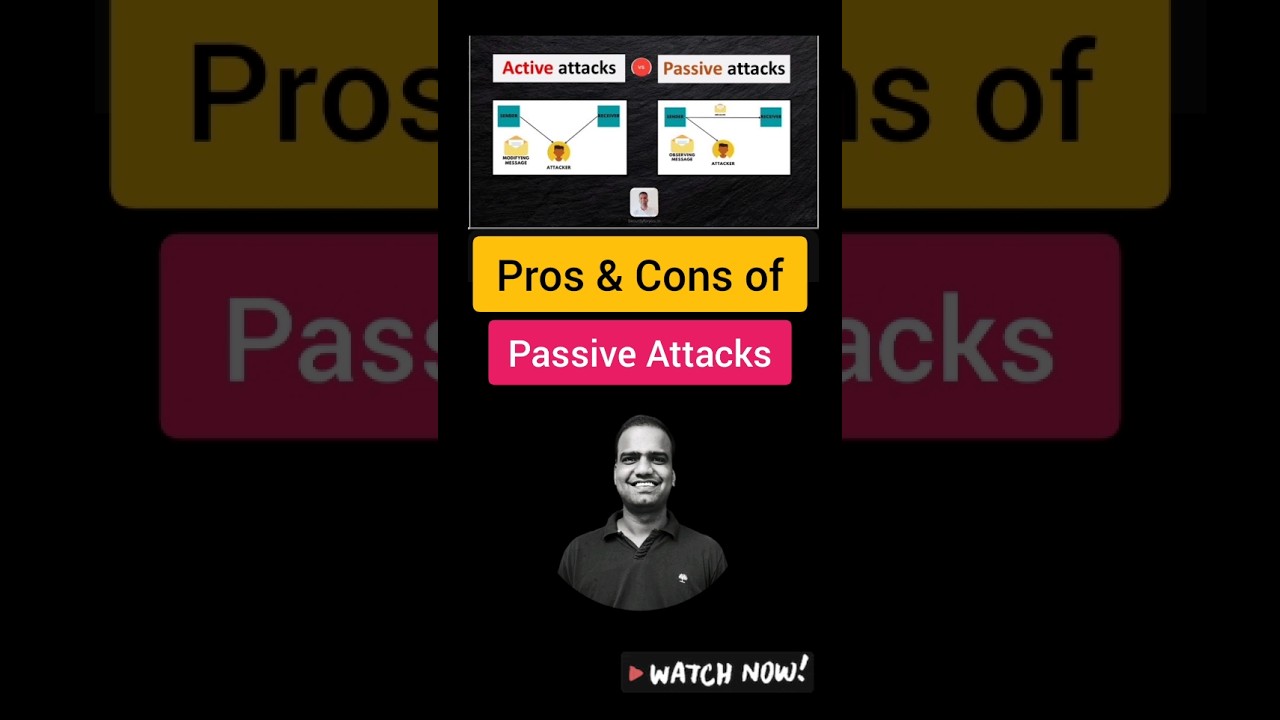
In this cybersecurity short, we look at passive attacks from the attacker’s point of view — what makes them appealing, and what their limitations are.
🔍 Advantages of Passive Attacks for Attackers
Passive attacks are attractive because they are hard to detect — attackers can monitor a system without being noticed, silently collecting sensitive information. These attacks require minimal effort, tools, or advanced skills, making them easy to carry out even by less experienced threat actors. The data collected can later be used for targeted attacks, fraud, or unauthorized access.
⚠️ Disadvantages for Attackers
However, passive attacks have their downsides too. They don’t cause immediate harm — there’s no data loss, no disruption, and no visible effect on the system. Attackers must wait and use the gathered data later to create impact. Also, they’re limited to observation only, as they can’t modify or disrupt anything directly.
This short is ideal for anyone learning about attack strategies in cybersecurity, helping viewers understand why some hackers choose stealth over impact — and what risks come with that approach.
💡 Like, share, and subscribe for more quick insights on how cyber attacks work in real-world scenarios.
Watch full video on active and passive attacks -
https://youtu.be/B89i747yC4A
#PassiveAttack #CyberSecurityShorts #EthicalHacking #InfoSecBasics #DigitalEspionage #CyberThreats #CyberAwareness #NetworkMonitoring #CyberAttackTypes #SilentHacking #SystemSurveillance #DataCollection #SecurityRisks #CyberExplained #CyberCriminals #ObservationOnly #LowEffortHacks #MinimalToolsHacking #CyberSecurityEducation #HackerTactics #SpyAttacks #CyberSecurityTips #DataPrivacy #CovertCyberAttacks #CyberSurveillance #HackersPerspective #CyberShorts #SilentCyberAttacks #DigitalSpying #CyberIntelligenceGathering
🔍 Advantages of Passive Attacks for Attackers
Passive attacks are attractive because they are hard to detect — attackers can monitor a system without being noticed, silently collecting sensitive information. These attacks require minimal effort, tools, or advanced skills, making them easy to carry out even by less experienced threat actors. The data collected can later be used for targeted attacks, fraud, or unauthorized access.
⚠️ Disadvantages for Attackers
However, passive attacks have their downsides too. They don’t cause immediate harm — there’s no data loss, no disruption, and no visible effect on the system. Attackers must wait and use the gathered data later to create impact. Also, they’re limited to observation only, as they can’t modify or disrupt anything directly.
This short is ideal for anyone learning about attack strategies in cybersecurity, helping viewers understand why some hackers choose stealth over impact — and what risks come with that approach.
💡 Like, share, and subscribe for more quick insights on how cyber attacks work in real-world scenarios.
Watch full video on active and passive attacks -
https://youtu.be/B89i747yC4A
#PassiveAttack #CyberSecurityShorts #EthicalHacking #InfoSecBasics #DigitalEspionage #CyberThreats #CyberAwareness #NetworkMonitoring #CyberAttackTypes #SilentHacking #SystemSurveillance #DataCollection #SecurityRisks #CyberExplained #CyberCriminals #ObservationOnly #LowEffortHacks #MinimalToolsHacking #CyberSecurityEducation #HackerTactics #SpyAttacks #CyberSecurityTips #DataPrivacy #CovertCyberAttacks #CyberSurveillance #HackersPerspective #CyberShorts #SilentCyberAttacks #DigitalSpying #CyberIntelligenceGathering
Video Information
Views
2.1K
Duration
0:40
Published
Jun 15, 2025
User Reviews
3.7
(2) Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.