Passive Attacks Explained: The Silent Threat in Cybersecurity 🛡️
Discover what passive attacks are and how they pose a covert danger to your digital security. Learn the essentials in this quick cybersecurity guide! #shorts

Security For You
1.4K views • Jun 15, 2025
About this video
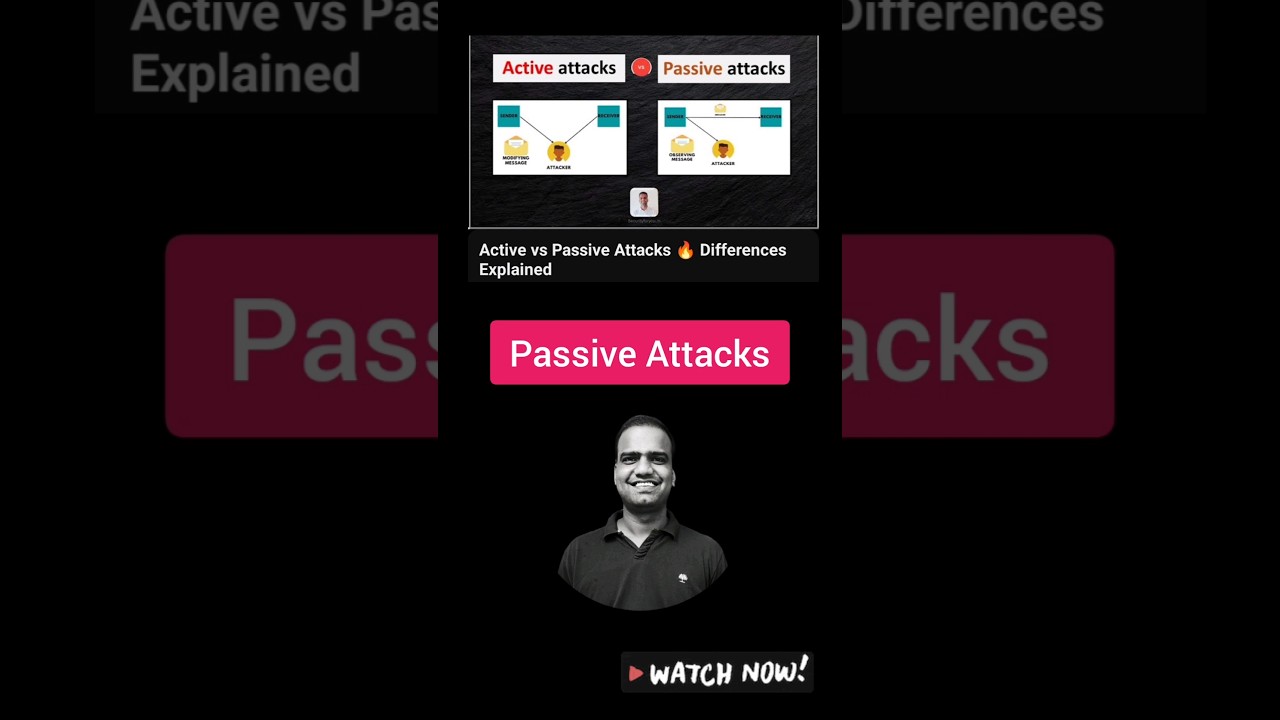
In this short but essential cybersecurity explainer, we dive into passive attacks — the silent threats in the digital world. These attacks are covert and non-intrusive, meaning the attacker’s goal is to gather data or monitor activity without making any changes to the system.
🕵️♂️ What Makes Passive Attacks Dangerous?
Passive attacks don’t interfere with a system’s availability or performance, which makes them hard to detect. However, they can severely compromise confidentiality by capturing sensitive information such as login credentials, email contents, or personal messages.
📡 Example of a Passive Attack:
Imagine an attacker using a packet sniffer to eavesdrop on unencrypted network traffic. They’re not altering the data — they’re silently watching and collecting valuable information without anyone knowing. That’s a classic example of a passive attack.
Because these attacks leave no obvious trace, detection is extremely difficult, making them a favorite method for intelligence gathering, corporate espionage, and cyber reconnaissance.
🎯 Perfect for beginners, cybersecurity students, or anyone looking to understand how modern attacks work without triggering alarms.
💡 Like, comment, and subscribe for more bite-sized cybersecurity knowledge!
Watch full video on active and passive attacks -
https://youtu.be/B89i747yC4A
#PassiveAttack #CyberSecurityShorts #NetworkSecurity #CyberThreats #InfoSecBasics #CyberAwareness #EthicalHacking #PacketSniffing #DigitalEavesdropping #DataPrivacy #CyberSecurityExplained #CyberSecurityForBeginners #CyberEducation #SilentAttacks #SystemMonitoring #HackersTactics #InformationSecurity #CyberCrimeAwareness #ConfidentialityBreach #CyberSecurityTips #NetworkMonitoring #SecurityRisks #CyberDefense #OnlineSafety #UnencryptedData #DigitalThreats #HackPrevention #CyberSurveillance #StealthHacking #CyberShorts
🕵️♂️ What Makes Passive Attacks Dangerous?
Passive attacks don’t interfere with a system’s availability or performance, which makes them hard to detect. However, they can severely compromise confidentiality by capturing sensitive information such as login credentials, email contents, or personal messages.
📡 Example of a Passive Attack:
Imagine an attacker using a packet sniffer to eavesdrop on unencrypted network traffic. They’re not altering the data — they’re silently watching and collecting valuable information without anyone knowing. That’s a classic example of a passive attack.
Because these attacks leave no obvious trace, detection is extremely difficult, making them a favorite method for intelligence gathering, corporate espionage, and cyber reconnaissance.
🎯 Perfect for beginners, cybersecurity students, or anyone looking to understand how modern attacks work without triggering alarms.
💡 Like, comment, and subscribe for more bite-sized cybersecurity knowledge!
Watch full video on active and passive attacks -
https://youtu.be/B89i747yC4A
#PassiveAttack #CyberSecurityShorts #NetworkSecurity #CyberThreats #InfoSecBasics #CyberAwareness #EthicalHacking #PacketSniffing #DigitalEavesdropping #DataPrivacy #CyberSecurityExplained #CyberSecurityForBeginners #CyberEducation #SilentAttacks #SystemMonitoring #HackersTactics #InformationSecurity #CyberCrimeAwareness #ConfidentialityBreach #CyberSecurityTips #NetworkMonitoring #SecurityRisks #CyberDefense #OnlineSafety #UnencryptedData #DigitalThreats #HackPrevention #CyberSurveillance #StealthHacking #CyberShorts
Video Information
Views
1.4K
Likes
1
Duration
0:42
Published
Jun 15, 2025
User Reviews
3.8
(1) Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now