Mastering the HSM Cryptographic Key Lifecycle 🔑: From Generation to Destruction
Discover the complete journey of cryptographic keys within HSMs, covering stages like generation, storage, distribution, rotation, recovery, revocation, and destruction to ensure maximum security.

CyberStoicITy
105 views • Jul 28, 2025
About this video
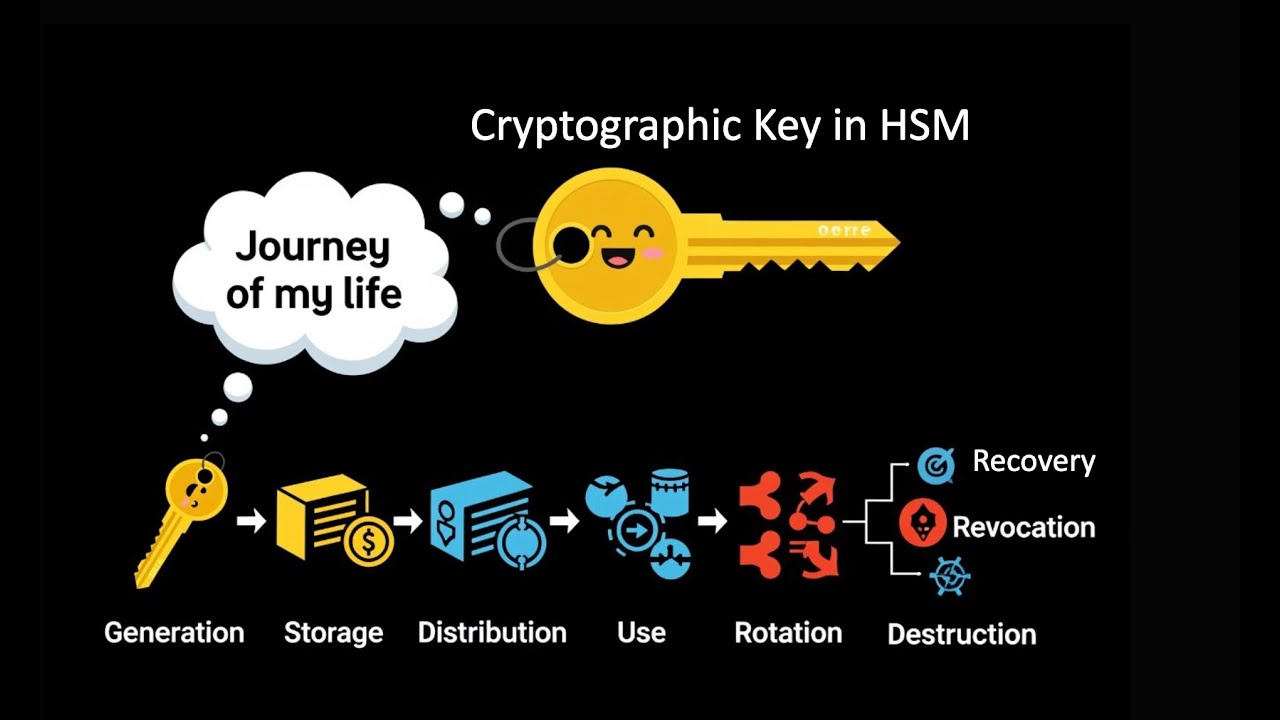
Learn about the different stages of a cryptographic key lifecycle in HSM - Generation, Storage, Distribution, Use, Rotation, Recovery, Revocation and Destruction.
CHAPTERS
00:00 Intro
01:08 Key Generation
02:30 Key Storage
03:12 Key Distribution
04:00 Key Use
04:45 Key Rotation
06:06 Key Backup and Recovery
07:35 Key Revocation and Destruction
08:20 Policy Enforcement and Insider Threat Mitigation by HSM
10:18 Security Approach
Follow the channel to get notification on any new video upload!
CHAPTERS
00:00 Intro
01:08 Key Generation
02:30 Key Storage
03:12 Key Distribution
04:00 Key Use
04:45 Key Rotation
06:06 Key Backup and Recovery
07:35 Key Revocation and Destruction
08:20 Policy Enforcement and Insider Threat Mitigation by HSM
10:18 Security Approach
Follow the channel to get notification on any new video upload!
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
105
Likes
13
Duration
10:51
Published
Jul 28, 2025
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.