Kerberos Authentication and Login Tickets in Enterprise Security
A concise explanation of how Kerberos authentication and login tickets function within enterprise security systems, suitable for CISSP preparation.

Cyber Security Learning
3.2K views • Jun 10, 2025
About this video
Kerberos Authentication Explained | How Login Tickets Work in Enterprise Security #CISSPFlashcards
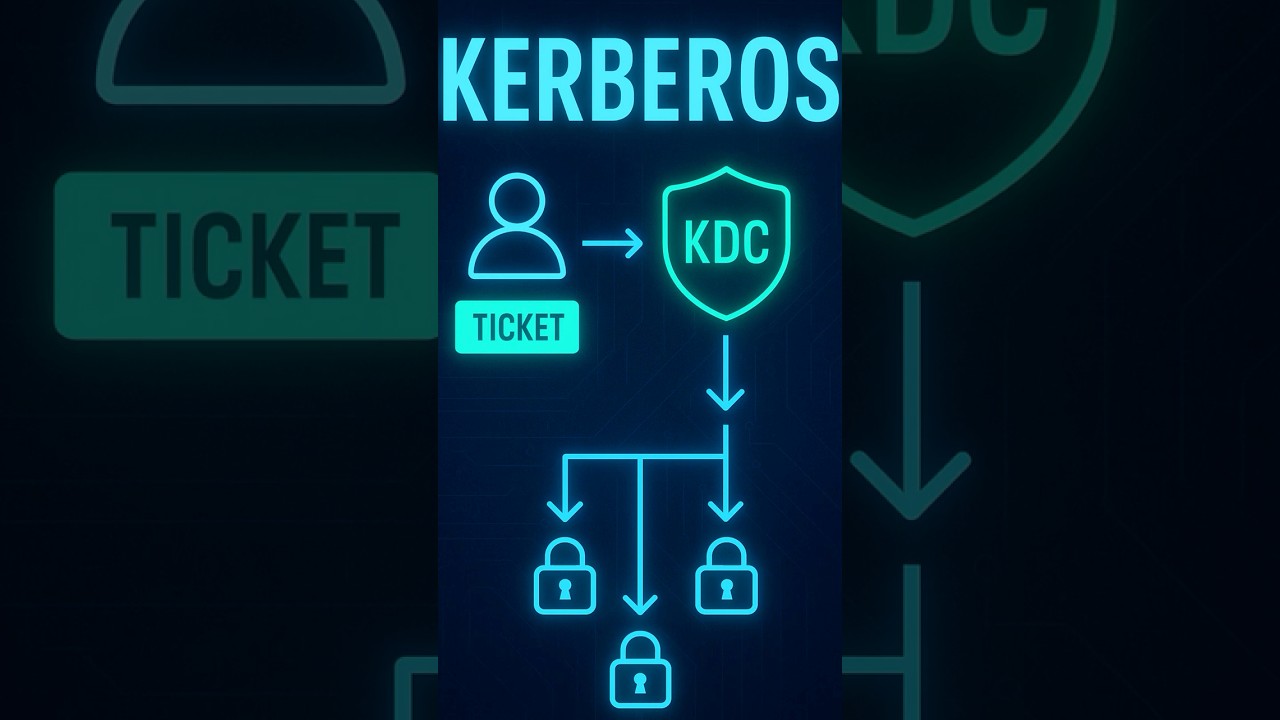
In this CISSP flashcard short, we explore the Kerberos authentication protocol—one of the most critical topics in enterprise network security and a guaranteed guest on your CISSP exam. If you’ve ever used single sign-on at work or accessed services across a corporate network without logging in each time, you’ve probably used Kerberos. It’s everywhere, from Active Directory environments to secure enterprise systems, and it’s a textbook example of how secure authentication is designed at scale. Kerberos is a trusted third-party authentication protocol that uses symmetric encryption to verify identities and grant access without passwords flying around the network. When a user logs in, they are issued a ticket from a central authority known as the Key Distribution Center (KDC). This ticket can then be used to request access from the Ticket Granting Server (TGS), which issues additional service tickets—like backstage passes for secure systems. No need to enter credentials again and again. Instead, these tickets prove who you are. Fast. Secure. Reusable. And that’s the genius of Kerberos. It reduces the attack surface, prevents password replay, and keeps credentials out of the clear. Understanding this protocol is key for CISSP Domain 5: Identity and Access Management. You’ll need to know how the protocol works, who the key players are—the client, the KDC, the Authentication Server (AS), the Ticket Granting Server (TGS), and the application server—and why symmetric encryption matters. The KDC is the master here. It holds the secret keys and handles authentication. It first confirms your identity and then grants a Ticket Granting Ticket (TGT). That TGT can then be exchanged for service-specific access tickets. So instead of entering your password again, your TGT vouches for you. This makes Kerberos incredibly efficient in environments where users need to access many different systems—think large companies, universities, or government networks. Kerberos is not just a login protocol—it’s a system of mutual trust, secret keys, and encrypted ticket exchanges that enables scalable, secure identity verification. You’ll also want to know this: Kerberos does not work well across trust boundaries (like between unrelated domains or companies), which is why it’s commonly used within but not between organizations. In the real world, Kerberos supports secure email, file sharing, database access, and more—all without risking your credentials. On the exam, expect Kerberos to appear in scenario questions involving centralized authentication, service access without repeated logins, and even discussions around cryptographic protocols and authentication flaws. You might be asked to identify its role in network security, its reliance on symmetric encryption, or to compare it with alternatives like RADIUS, SAML, or OAuth. Understand its ticket-based flow, its use of time-based expiration (important to prevent replay attacks), and how replay prevention relies on accurate time synchronization across systems. If time is out of sync, Kerberos fails. That’s why systems using it must rely on protocols like NTP (Network Time Protocol). In short, Kerberos is essential knowledge for CISSP candidates—and real-world security professionals. You’ll see it in firewalls, VPN access, Active Directory logins, cloud identity bridges, and SSO implementations. Memorize the flow. Know the purpose of the TGT. Understand its encryption. And always remember: it’s not just about who you are—it’s about proving it securely and efficiently. This short helps lock that in. Watch it twice if you need to. Subscribe for more CISSP flashcards and master every concept you need to pass with confidence.
#CISSP #Kerberos #Authentication #CyberSecurity #IAM #SingleSignOn #CISSPFlashcard #TicketBasedSecurity #NetworkSecurity #CISSPExam #SecurityProtocols #Encryption #CyberLearning #AccessControl #VeedIOShorts #SecurityArchitecture
In this CISSP flashcard short, we explore the Kerberos authentication protocol—one of the most critical topics in enterprise network security and a guaranteed guest on your CISSP exam. If you’ve ever used single sign-on at work or accessed services across a corporate network without logging in each time, you’ve probably used Kerberos. It’s everywhere, from Active Directory environments to secure enterprise systems, and it’s a textbook example of how secure authentication is designed at scale. Kerberos is a trusted third-party authentication protocol that uses symmetric encryption to verify identities and grant access without passwords flying around the network. When a user logs in, they are issued a ticket from a central authority known as the Key Distribution Center (KDC). This ticket can then be used to request access from the Ticket Granting Server (TGS), which issues additional service tickets—like backstage passes for secure systems. No need to enter credentials again and again. Instead, these tickets prove who you are. Fast. Secure. Reusable. And that’s the genius of Kerberos. It reduces the attack surface, prevents password replay, and keeps credentials out of the clear. Understanding this protocol is key for CISSP Domain 5: Identity and Access Management. You’ll need to know how the protocol works, who the key players are—the client, the KDC, the Authentication Server (AS), the Ticket Granting Server (TGS), and the application server—and why symmetric encryption matters. The KDC is the master here. It holds the secret keys and handles authentication. It first confirms your identity and then grants a Ticket Granting Ticket (TGT). That TGT can then be exchanged for service-specific access tickets. So instead of entering your password again, your TGT vouches for you. This makes Kerberos incredibly efficient in environments where users need to access many different systems—think large companies, universities, or government networks. Kerberos is not just a login protocol—it’s a system of mutual trust, secret keys, and encrypted ticket exchanges that enables scalable, secure identity verification. You’ll also want to know this: Kerberos does not work well across trust boundaries (like between unrelated domains or companies), which is why it’s commonly used within but not between organizations. In the real world, Kerberos supports secure email, file sharing, database access, and more—all without risking your credentials. On the exam, expect Kerberos to appear in scenario questions involving centralized authentication, service access without repeated logins, and even discussions around cryptographic protocols and authentication flaws. You might be asked to identify its role in network security, its reliance on symmetric encryption, or to compare it with alternatives like RADIUS, SAML, or OAuth. Understand its ticket-based flow, its use of time-based expiration (important to prevent replay attacks), and how replay prevention relies on accurate time synchronization across systems. If time is out of sync, Kerberos fails. That’s why systems using it must rely on protocols like NTP (Network Time Protocol). In short, Kerberos is essential knowledge for CISSP candidates—and real-world security professionals. You’ll see it in firewalls, VPN access, Active Directory logins, cloud identity bridges, and SSO implementations. Memorize the flow. Know the purpose of the TGT. Understand its encryption. And always remember: it’s not just about who you are—it’s about proving it securely and efficiently. This short helps lock that in. Watch it twice if you need to. Subscribe for more CISSP flashcards and master every concept you need to pass with confidence.
#CISSP #Kerberos #Authentication #CyberSecurity #IAM #SingleSignOn #CISSPFlashcard #TicketBasedSecurity #NetworkSecurity #CISSPExam #SecurityProtocols #Encryption #CyberLearning #AccessControl #VeedIOShorts #SecurityArchitecture
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
3.2K
Duration
0:44
Published
Jun 10, 2025
User Reviews
3.8
(3) Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now