Digital Signature Standards and Algorithms: RSA and DSS Approaches Explained in Hindi Urdu
Explore the Digital Signature Standard and delve into the Digital Signature Algorithm with a focus on RSA and DSS approaches. This video also covers various types of message authentication, including MAC, as part of network security discussions in Hindi U

Ask Faizan
29.1K views • Nov 21, 2018
About this video
#askfaizan | #syedfaizanahmad | #digital signature
Types of Message Authentication | MAC | Part 2 | Network Security | Hindi Urdu https://youtu.be/C88ujAT8N0U
Types of Message Authentication | Message Encryption | Part 1 | Network Security | Hindi Urdu https://youtu.be/2eRGEntqpL4
DIFFIE HELLMAN KEY EXCHANGE ALGORITHM | Diffie-Hellman key exchange algorithm | HINDI URDU https://youtu.be/I6oUvYzPMXc
RSA Algorithm | RSA Algorithm Concept | RSA Algorithm with Example | Hindi / Urdu https://youtu.be/s3CH9c3Jcu0
How to find Euler's Totient Function https://youtu.be/6wHwTB-bRlw
DES | Simple Explanation | Data Encryption Standard Algo https://youtu.be/oR1JQJlXtq4
Network Security - Transposition Techniques https://youtu.be/h4MOqFkN9Tk
Block Cipher Modes of Operation | CTR mode https://youtu.be/Rp5HOTe4EbE
Block Cipher Modes of Operation | OFB mode https://youtu.be/F2RwmXwrdV8
Block Cipher Modes of Operation | CFB mode https://youtu.be/yF_iA7Rv7k4
Block Cipher Modes of Operation | CBC mode | Part 2 https://youtu.be/Q7LKmASkVSU
Block Cipher Modes of Operation | ECB mode | Part 1 https://youtu.be/mkY5mNSnuko
Hill Cipher | Complete Algorithm with Example https://youtu.be/B0Q7w7Fd7ms
Playfair Substitution Cipher https://youtu.be/w_xr7pj-O6c
Monoalphabetic Substitution Cipher https://youtu.be/Hw1T7GOnVW0
Caesar Cipher | Caesar Substitution Cipher https://youtu.be/2N9GlhysYJw
PlayList : Cryptography and Network Security : https://www.youtube.com/playlist?list=PLhwpdymnbXz7hvvqhqjIIG4tEdhAgQqll
In Asymmetric Encryption, two types of keys are used – Public key & Private key
Public key is shared to all
Private key is secret key
When message is Encrypted using Sender’s Private key then automatically process is called Digital Signature.
When there is trust issues between sender and receiver, something more than authentication is needed.
The most attractive solution to this problem is the Digital Signature.
The digital signature must have the following properties:
It must verify the author and date and time of the signature.
It must authenticate the contents at the time of the signature.
It must be verifiable by third parties, to resolve disputes.
Approaches of Digital Signature -
RSA approach
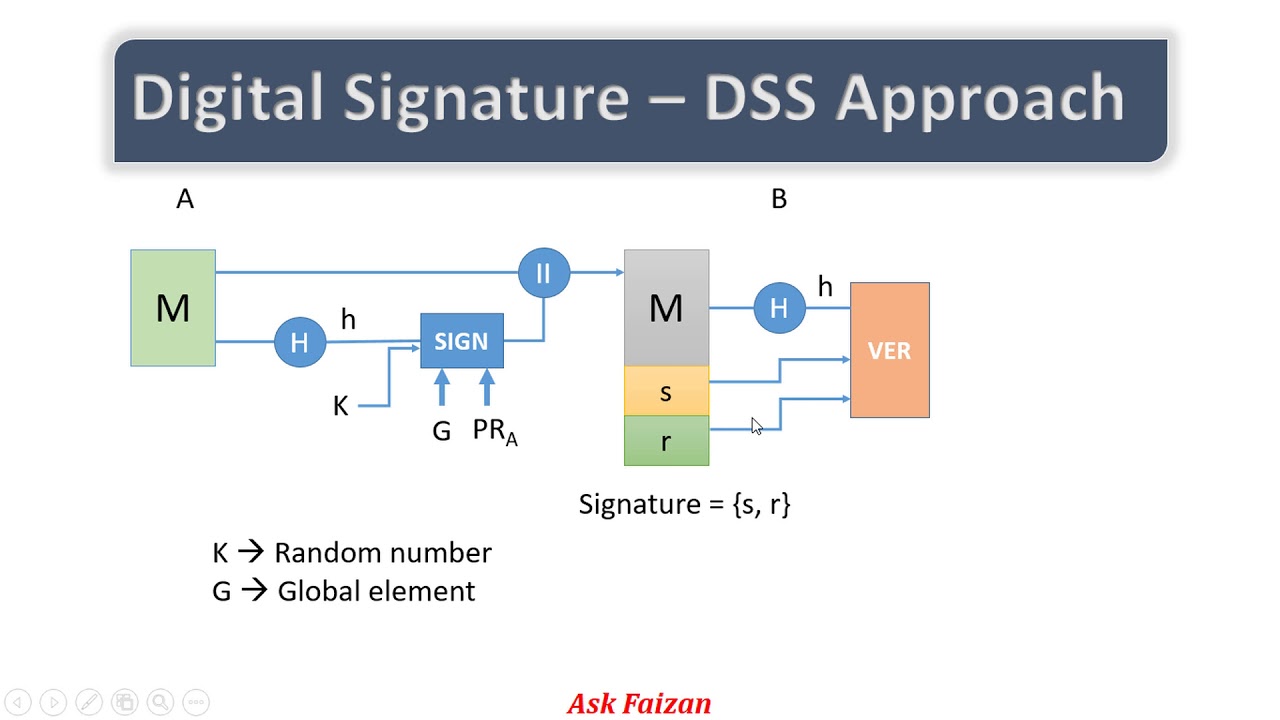
DSS / DSA approach
Types of Message Authentication | MAC | Part 2 | Network Security | Hindi Urdu https://youtu.be/C88ujAT8N0U
Types of Message Authentication | Message Encryption | Part 1 | Network Security | Hindi Urdu https://youtu.be/2eRGEntqpL4
DIFFIE HELLMAN KEY EXCHANGE ALGORITHM | Diffie-Hellman key exchange algorithm | HINDI URDU https://youtu.be/I6oUvYzPMXc
RSA Algorithm | RSA Algorithm Concept | RSA Algorithm with Example | Hindi / Urdu https://youtu.be/s3CH9c3Jcu0
How to find Euler's Totient Function https://youtu.be/6wHwTB-bRlw
DES | Simple Explanation | Data Encryption Standard Algo https://youtu.be/oR1JQJlXtq4
Network Security - Transposition Techniques https://youtu.be/h4MOqFkN9Tk
Block Cipher Modes of Operation | CTR mode https://youtu.be/Rp5HOTe4EbE
Block Cipher Modes of Operation | OFB mode https://youtu.be/F2RwmXwrdV8
Block Cipher Modes of Operation | CFB mode https://youtu.be/yF_iA7Rv7k4
Block Cipher Modes of Operation | CBC mode | Part 2 https://youtu.be/Q7LKmASkVSU
Block Cipher Modes of Operation | ECB mode | Part 1 https://youtu.be/mkY5mNSnuko
Hill Cipher | Complete Algorithm with Example https://youtu.be/B0Q7w7Fd7ms
Playfair Substitution Cipher https://youtu.be/w_xr7pj-O6c
Monoalphabetic Substitution Cipher https://youtu.be/Hw1T7GOnVW0
Caesar Cipher | Caesar Substitution Cipher https://youtu.be/2N9GlhysYJw
PlayList : Cryptography and Network Security : https://www.youtube.com/playlist?list=PLhwpdymnbXz7hvvqhqjIIG4tEdhAgQqll
In Asymmetric Encryption, two types of keys are used – Public key & Private key
Public key is shared to all
Private key is secret key
When message is Encrypted using Sender’s Private key then automatically process is called Digital Signature.
When there is trust issues between sender and receiver, something more than authentication is needed.
The most attractive solution to this problem is the Digital Signature.
The digital signature must have the following properties:
It must verify the author and date and time of the signature.
It must authenticate the contents at the time of the signature.
It must be verifiable by third parties, to resolve disputes.
Approaches of Digital Signature -
RSA approach
DSS / DSA approach
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
29.1K
Likes
489
Duration
13:36
Published
Nov 21, 2018
User Reviews
4.6
(5) Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.