DEFCON 18: pyREtic – Advanced In-Memory Reverse Engineering of Obfuscated Python Bytecode 🐍 (Part 2/3)
Discover how to analyze and reverse engineer protected Python applications using pyREtic at DEFCON 18. Learn techniques to uncover hidden code in obfuscated Python bytecode.

Christiaan008
910 views • Oct 6, 2010
About this video
Speaker: Rich Smith
Increasing numbers of commercial and closed source applications are being developed in Python. Developers of such applications are investing more & more to stop people being able to see their source code through a variety of code obfuscation techniques. At the same time Python is an increasingly present component of 'Cloud' technologies where traditional bytecode decompilation techniques fall down through lack of access to files on disk.
The pyREtic presentation discusses the techniques and subsequent toolkit developed while trying to audit one such closed source Python application. The methodology behind the approaches used as well as practicalities of reverse engineering at the Python level (rather than the assembly level that we are all more familiar with) will be discussed as well as releasing a toolkit.
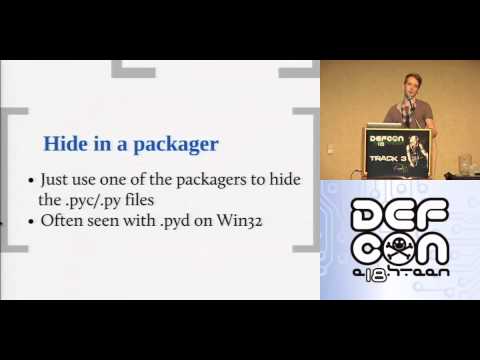
The toolkit is able to reverse Python applications from live objects in memory as opposed to decompiling .pyc bytecode files, it also shows how to defeat the techniques most commonly employed to obfuscate Python code today. This will allow people to find bugs in code that was previously opaque to them.
For presentations, whitepapers or audio version of the Defcon 18 presentations visit: http://defcon.org/html/links/dc-archives/dc-18-archive.html
Increasing numbers of commercial and closed source applications are being developed in Python. Developers of such applications are investing more & more to stop people being able to see their source code through a variety of code obfuscation techniques. At the same time Python is an increasingly present component of 'Cloud' technologies where traditional bytecode decompilation techniques fall down through lack of access to files on disk.
The pyREtic presentation discusses the techniques and subsequent toolkit developed while trying to audit one such closed source Python application. The methodology behind the approaches used as well as practicalities of reverse engineering at the Python level (rather than the assembly level that we are all more familiar with) will be discussed as well as releasing a toolkit.
The toolkit is able to reverse Python applications from live objects in memory as opposed to decompiling .pyc bytecode files, it also shows how to defeat the techniques most commonly employed to obfuscate Python code today. This will allow people to find bugs in code that was previously opaque to them.
For presentations, whitepapers or audio version of the Defcon 18 presentations visit: http://defcon.org/html/links/dc-archives/dc-18-archive.html
Video Information
Views
910
Likes
4
Duration
14:58
Published
Oct 6, 2010
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.