Cryptography Explained: Symmetric vs Asymmetric Encryption 🔐 (Part 2)
Dive deeper into cryptography with this second part, where we compare symmetric and asymmetric encryption methods. Perfect for beginners wanting to understand how data security works!

Penguin Fortress - Cybersecurity Information
253 views • Feb 9, 2023
About this video
This is the second of my videos on an introduction to cryptography. My earlier video gave a brief overview of cryptography, some of the history behind cryptography and an example using ROT13.
Part 1 about Cryptography, history and importance:
https://youtu.be/is31vSjddCM
In this video I’ll look at the importance on cryptography today and some additional concepts relevant to modern security.
The video includes the importance of cryptography in the CIA security triad.
Cryptography in various states at rest, in use, in transit.
Encryption algorithms. Kerckhoff's principle vs security by obscurity.
Differences between codes and ciphers.
For more details see:
http://www.penguinfortress.com/security/cryptography
Chapters:
00:00 Introduction to Cryptography
00:23 Importance of Cryptography
01:47 Encryption Algorithms
03:01 Codes and Ciphers
06:38 Symmetric Key Encryption
07:20 Asymmetric Key Encryption
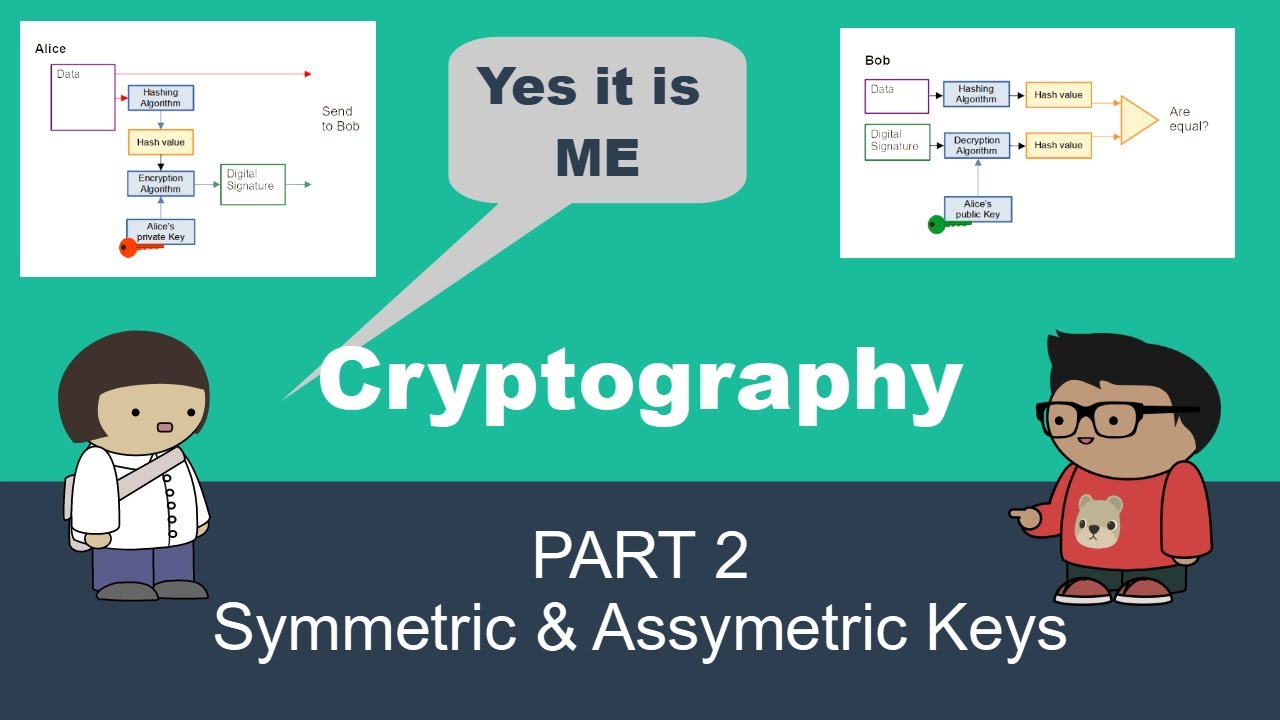
10:29 Hashes
11:07 Digital Signatures
12:25 Summary
#cybersecurity #cryptography
Part 1 about Cryptography, history and importance:
https://youtu.be/is31vSjddCM
In this video I’ll look at the importance on cryptography today and some additional concepts relevant to modern security.
The video includes the importance of cryptography in the CIA security triad.
Cryptography in various states at rest, in use, in transit.
Encryption algorithms. Kerckhoff's principle vs security by obscurity.
Differences between codes and ciphers.
For more details see:
http://www.penguinfortress.com/security/cryptography
Chapters:
00:00 Introduction to Cryptography
00:23 Importance of Cryptography
01:47 Encryption Algorithms
03:01 Codes and Ciphers
06:38 Symmetric Key Encryption
07:20 Asymmetric Key Encryption
10:29 Hashes
11:07 Digital Signatures
12:25 Summary
#cybersecurity #cryptography
Video Information
Views
253
Likes
2
Duration
13:11
Published
Feb 9, 2023