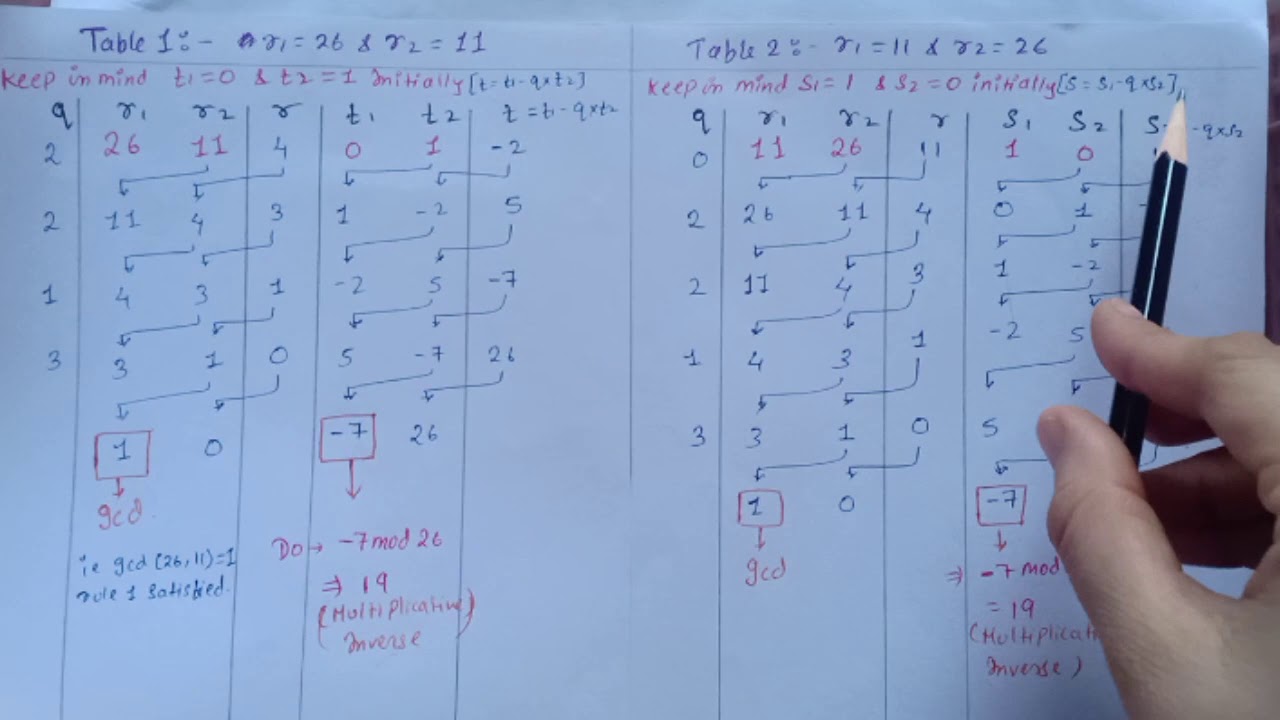
Cryptography and Network Security: Multiplicative Inverse Using Extended Euclidean Algorithm – Part 2
An in-depth explanation of finding the multiplicative inverse in cryptography through the Extended Euclidean Algorithm, focusing on practical implementation and examples.

Shreya's E-Learning
1.4K views • Jun 20, 2020
About this video
Cryptography and Network Security: Multiplicative Inverse using Extended Euclidean Algorithm
Video Information
Views
1.4K
Likes
32
Duration
9:02
Published
Jun 20, 2020
User Reviews
4.5
(1) Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.