Christian Paquin on Transitioning to Quantum-Safe Crypto at DEF CON 27 🔐
Discover how Christian Paquin discusses the urgent need to migrate to quantum-resistant cryptography to safeguard data against future quantum threats at DEF CON 27's Crypto and Privacy Village.

DEFCONConference
1.5K views • Nov 27, 2019
About this video
A non-trivial quantum computer would break the public key cryptography in use today. They might be at least a decade away, but nothing prevents adversaries to record and store selected internet traffic today for later quantum-assisted decryption. It is therefore prudent to start the migration to quantum-safe cryptography.
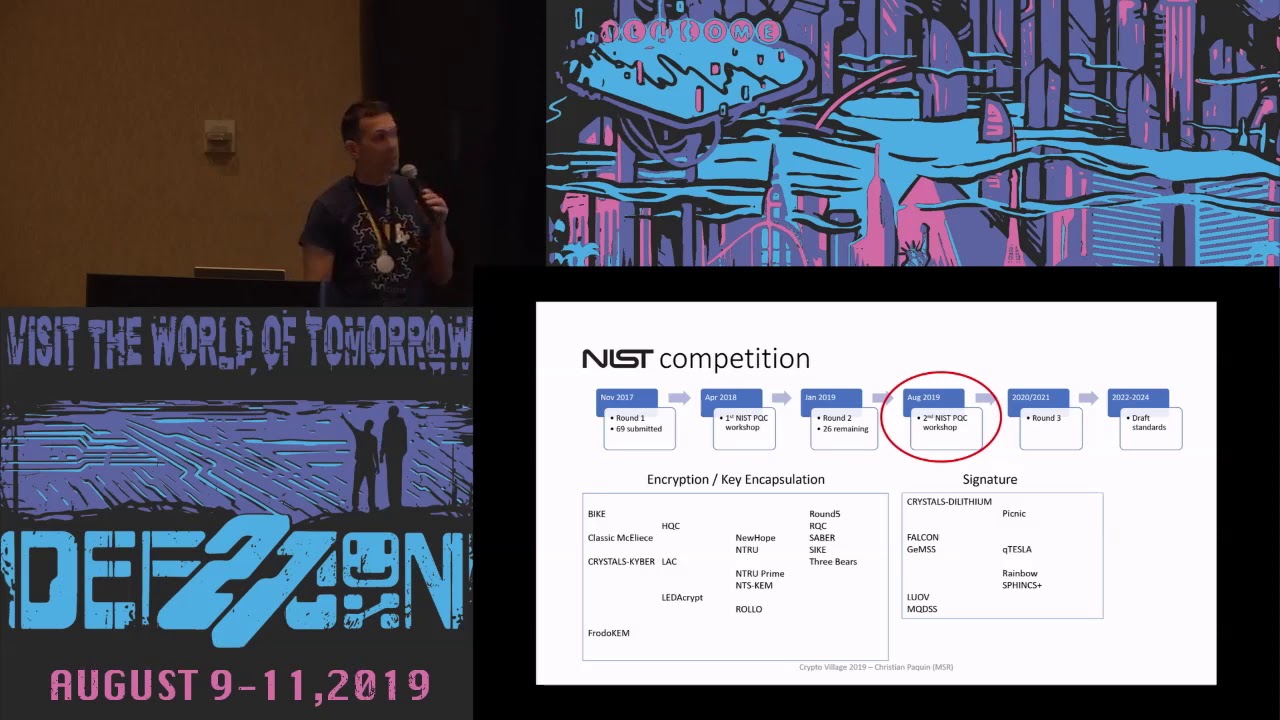
NIST is well underway in its post-quantum standardization process. Adoption of these quantum-safe alternatives will however depend on the progress in integrating them into internet standards and systems. We describe how TLS and SSH can be adapted to use post-quantum cryptography. We examine various design considerations and report on our experiences in adding post-quantum and hybrid key exchange and authentication to these protocols. We describe the Open Quantum Safe project, which enables developers and researchers to experiment with post-quantum cryptography in various languages, applications, and protocols, including via our forks of OpenSSL and OpenSSH.
Finally, we report on the performance of this new cryptography, and demonstrate conventional and post-quantum hybrid TLS 1.3 and SSH connections.
BIO
Christian Paquin - I am a crypto specialist in Microsoft Research's Security and Cryptography team. I’m currently involved in projects related to post-quantum cryptography, such as the Open Quantum Safe project. I’m also leading the development of U-Prove, a privacy-enhanced authentication technology. In my time at MSR, I’ve worked on projects involving various privacy-enhancing technologies, smart cloud encryption (e.g., searchable and homomorphic encryption), and the intersection of AI and security. Prior to joining Microsoft in 2008, I was the Chief Security Engineer at Credentica, a crypto developer at Silanis Technology working on digital signature systems, and a security engineer at Zero-Knowledge Systems working on TOR-like systems.
NIST is well underway in its post-quantum standardization process. Adoption of these quantum-safe alternatives will however depend on the progress in integrating them into internet standards and systems. We describe how TLS and SSH can be adapted to use post-quantum cryptography. We examine various design considerations and report on our experiences in adding post-quantum and hybrid key exchange and authentication to these protocols. We describe the Open Quantum Safe project, which enables developers and researchers to experiment with post-quantum cryptography in various languages, applications, and protocols, including via our forks of OpenSSL and OpenSSH.
Finally, we report on the performance of this new cryptography, and demonstrate conventional and post-quantum hybrid TLS 1.3 and SSH connections.
BIO
Christian Paquin - I am a crypto specialist in Microsoft Research's Security and Cryptography team. I’m currently involved in projects related to post-quantum cryptography, such as the Open Quantum Safe project. I’m also leading the development of U-Prove, a privacy-enhanced authentication technology. In my time at MSR, I’ve worked on projects involving various privacy-enhancing technologies, smart cloud encryption (e.g., searchable and homomorphic encryption), and the intersection of AI and security. Prior to joining Microsoft in 2008, I was the Chief Security Engineer at Credentica, a crypto developer at Silanis Technology working on digital signature systems, and a security engineer at Zero-Knowledge Systems working on TOR-like systems.
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
1.5K
Likes
35
Duration
25:34
Published
Nov 27, 2019
User Reviews
4.5
(1) Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now