Search Results for "lattice Boltzmann"
Find videos related to your search query. Browse through our collection of videos matching "lattice Boltzmann". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "lattice Boltzmann"
50 results found

46:54
Lattice algorithms and lattice-based cryptography
Sergey Dovgal
999 views

8:04
IBM Research 5 in 5 Science Slam: Lattice Cryptography
IBM Research
10.4K views
0:20
Lattice Based Security Model #cissp #latticesecurity #securitymodel #learncybersecurity
Quick Cybersecurity Study
106 views

25:11
PQCrypto 2023: Session VI: New NTRU Records with Improved Lattice Bases (Julian Nowakowski)
QuICS
152 views

1:04:18
Expressive encryption from hard lattice problems
Microsoft Research
624 views

2:38
Lattice cryptography: A new unbreakable code
Michigan Engineering
21.0K views

4:04
Lattice-Based Zero-Knowledge Proofs and Applications: Shorter, Simpler, and More General
IACR
13.7K views

29:28
CCS 2016 - ΛОλ: Functional Lattice Cryptography
CCS 2016
379 views

7:08
Introduction to Lattice Based Cryptography
Matthew Dozer
38.2K views

28:41
Attacking RSA with lattice reduction techniques (LLL)
David Wong
20.5K views

43:28
Rongchan Zhu: Makeenko-Migdal equations for 2D Yang–Mills: from lattice to continuum
Hausdorff Center for Mathematics
66 views

3:44
What Is Lattice-based Cryptography? - SecurityFirstCorp.com
SecurityFirstCorp
23 views

20:10
Saber on ARM: CCA secure module lattice based key encapsulation on ARM
IACR
327 views

29:57
Lecture 5. SIS/LWE and lattices (The Mathematics of Lattice-Based Cryptography)
Cryptography 101
1.4K views
1:18:18
Asiacrypt 2022 Session on Lattice Algorithms and Cryptanalysis
IACR
270 views
1:11:47
Lattice-Based Cryptography
Microsoft Research
8.2K views
10:36
Haskell Implementation of Key-Homomorphic PRF based on Lattice Cryptography
Michigan Engineering - Honors Program
180 views

9:54
Lattice (GATE Problems) - Set 1
Neso Academy
52.4K views

18:54
Post Quantum Crypto - Lattice Methods
Bill Buchanan OBE
10.1K views

57:21
Attacking Lattice-based Cryptography with Martin Albrecht
Security Cryptography Whatever
383 views

7:23
Lattice-based Post-Quantum Cryptography (PQC)
Hello InfoSec
24 views

17:53
Post-Quantum Cryptography: Lattice based Digital Signature Scheme
Elucyda
3.1K views

1:00:06
Winter School on Cryptography: A History of Lattice-Based Encryption - Vadim Lyubashevsky
Bar-Ilan University - אוניברסיטת בר-אילן
5.9K views

9:54
Lattice-Based Post-Quantum Cryptography
Akhil Chandra Gorakala
317 views
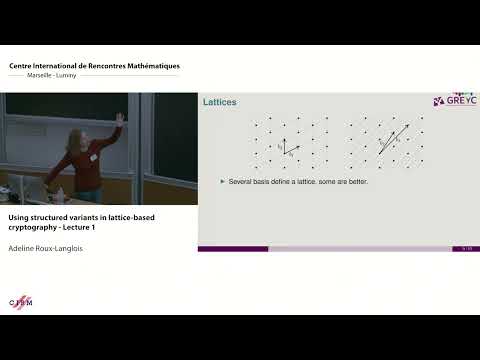
1:25:34
Adeline Roux-Langlois : Using structured variants in lattice-based cryptography - Lecture 1
Centre International de Rencontres Mathématiques
329 views

13:50
Quantum Computer & Lattice Based Post Quantum Cryptography(PQC)
경배
161 views

1:15:50
017 Estimating the difficulty of breaking lattice-based cryptography w/ Martin Albrecht
FHE_org
1.0K views

1:47:21
Daniele Micciancio - Lattice-based public-key cryptography
Institute for Quantum Computing
3.0K views
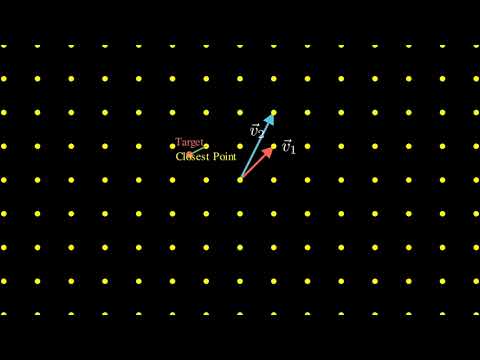
5:04
Lattice Based Cryptography in the Style of 3B1B
GATP Collin, Boden, and Armaan
3.3K views

1:08:11
Lattice-Based Post-Quantum Cryptography: A Comprehensive Guide
Hello InfoSec
29 views

1:08:42
15 Vadim Lyubashevsky on Lattice-Based Digital Signatures
Workshop on Lattices with Symmetry
1.5K views
42:10
Eurocrypt 2023 session: Lattice Cryptanalysis
IACR
247 views
25:51
Watermarking Cryptographic Functionalities from Standard Lattice Assumptions
IACR
831 views

1:12:48
Lattice-Based Cryptography
Microsoft Research
7.3K views

50:55
Sky Cao: Expanded regimes of area law for lattice Yang-Mills theories
Hausdorff Center for Mathematics
94 views

1:13:53
Lattice-Based SNARKs and Post-Quantum Cryptography | Proof is in the Pudding Session 04
Archetype
226 views

22:05
V5: Cryptanalytic Applications (Lattice Basis Reduction)
Cryptography 101
83 views

4:23
Lattice-Based Cryptography: Mathematical Foundations for Post-Quantum Security
g Fun Facts online
22 views

2:20
What Is Lattice-Based Cryptography? - CryptoBasics360.com
CryptoBasics360
171 views

1:30:39
01 Daniele Micciancio on "Lattice Cryptography: Introduction and Open Questions"
Conference on Mathematics of Cryptography
731 views
47:15
s-12: Lattice Cryptanalysis
IACR
269 views

0:46
The beauty of Shor's Algorithm and lattice cryptography #podcast #cryptocurrency #crypto
Bitcoin Takeover Shorts
720 views
![[English] How to use lattice in CTF? - SECCON 2020 sharsable writeup by Kurenaif](/image/i.ytimg.com/vi/g6EruH_29ew/hqdefault.jpg)
7:28
[English] How to use lattice in CTF? - SECCON 2020 sharsable writeup by Kurenaif
kurenaif
3.4K views

56:49
Lattice Attacks for Variants of LWE
Microsoft Research
2.2K views

0:17
What are lattice-based cryptographic algorithms?
Intelligence Gateway
367 views
2:45
What is the difference between Public & Private key Cryptography? By Lattice.
Lattice
190 views

21:01
V3: Gram-Schmidt Orthogonalization (Lattice Basis Reduction)
Cryptography 101
114 views
55:42
Classical and quantum algorithms for lattice problems achieving subexponential approximation factor
Fields Institute
129 views

6:56
Accelerating Lattice based Proxy Re Encryption schemes on GPUs - Short version
CANS - Cryptology and Network Security
65 views

13:27
USENIX Security '24 - SWOOSH: Efficient Lattice-Based Non-Interactive Key Exchange
USENIX
165 views
Page 1