Search Results for "cryptographic method"
Find videos related to your search query. Browse through our collection of videos matching "cryptographic method". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "cryptographic method"
50 results found

20:32
Bisection method numerical analysis in hindi | Bisection method to find roots | Bisection Method
Mechanical in Hindi
41 views

8:50
Introduction to Cryptographic Attacks | Types of Cryptographic Attacks Explained With Measures
Shree Learning Academy
2.3K views

0:34
How To Pronounce Cryptographic🌈🌈🌈🌈🌈🌈Pronunciation Of Cryptographic
Isabella Saying
33 views

0:34
Cryptographic | CRYPTOGRAPHIC meaning
Word Mastery Channel
0 views

0:02
How to pronounce Cryptographic / Cryptographic pronunciation
Raccoon Teaches You
48 views

9:59
VTU June 19 - Definition And Properties of Cryptographic Hash - Cryptographic And Network Security
Education
66 views

6:55
Attacks on Cryptographic Hash Algorithms || what is cryptographic? || Best Mind Like
Best Mind Like
45 views
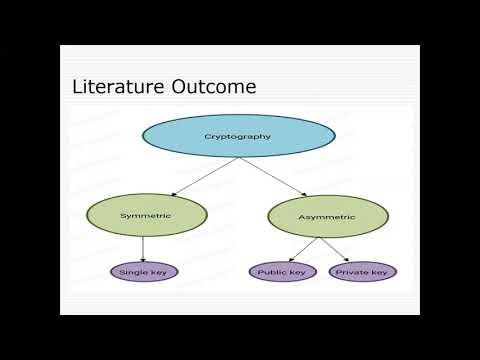
20:59
Project Presentation (Security in Vehicular AD-HOC Network using Hybrid Cryptographic Method)
Zehra Afzal
85 views
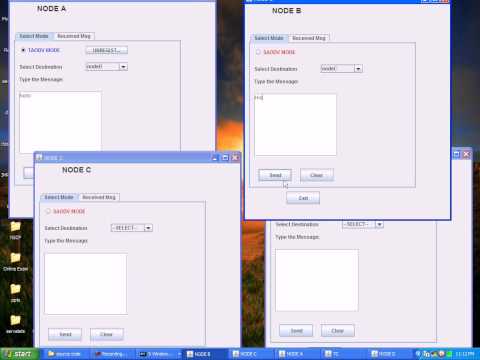
4:08
Cryptographic Versus Trust-based Method s for MANET Routing Security
projectsnine
604 views

14:08
Information encryption method based on a combination of steganographic and cryptographic algorithm’s
Василь Триснюк
22 views
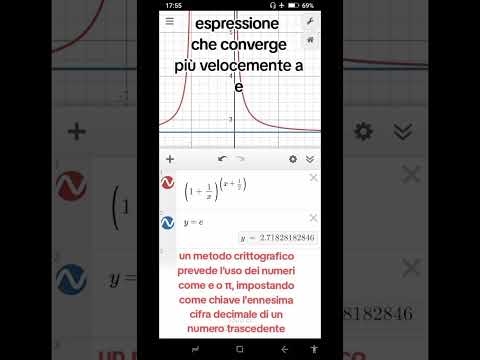
0:09
a cryptographic method uses transcendental numbers, setting the nth decimal digit as the key
La Raccolta
134 views
2:34
What is the cryptographic method where one party can prove to another that they know a value, with..
EmmaCrypto
105 views

8:25
TUBE METHOD/ABO GROUPING METHOD /PART 3 / ABO GROUP SYSTEM/ PART 7
LAB TECH CLASSROOM by VMG
5.3K views

9:30
Introduction to Greedy Method || General Method || Control Abstraction || Applications || DAA
Sudhakar Atchala
62.3K views

3:44
S.T.A.R vs C.A.R interview method - Best interview method/technique
CareerShakers
8.6K views

0:45
Forward and reverse blood grouping method. How to prepare cell suspension for reverse method? Next
Pathofied Mindful tips
2.5K views

4:31
How to Apply RGPV degree in offline method OR Online method|| मात्र 15दिन मैं डिग्री कैसे लाए..?
Humsafar Shubham
17.6K views

1:34
How to find a boyfriend Drama Method Review Scam Alert - Drama Method review
Teddylonger79
47 views

0:19
Read How to Solve It: A New Aspect of Mathematical Method: A New Aspect of Mathematical Method
Nando Patulopol
5 views
1:26
The Drama Method The Drama Method Review
Dorethea4sf
1 views
1:26
The Drama Method The Drama Method Review
Jenifferovy
1 views

1:09
Drama Method PDF - Get Access To Drama Method PDF Now!
Carita53k
3 views

1:27
Download The Drama Method Aaron Fox Pdf - What Is The Drama Method
Penelopefnz
3 views

2:30
The Drama Method Reviews - Drama Method
Shawnnarsa
1 views

2:27
The Drama Method | The Drama Method-The Emotional Hook Formulas
Marvel0iq
1 views
1:26
The Drama Method | The Drama Method Review
Felicitasa3u
0 views
![drama method relationships | Drama Method [Discount link here]](/image/s1.dmcdn.net/v/DSNUJ1e9M4zhlmAR4/x720)
2:04
drama method relationships | Drama Method [Discount link here]
Delphineu1c
0 views
2:49
Drama Method - The Real ""Drama Method"" Review
Juneayw
1 views
![drama method reviews | Drama Method [Discount link here]](/image/s2.dmcdn.net/v/DTLAH1e0Z_OiYye5d/x720)
2:04
drama method reviews | Drama Method [Discount link here]
Marjorieei0
0 views
6:14
google adsense loading method | google adsense loading method 2024 | Google Adscence #baqgamers
Gadget Explorer
355 views

0:06
Grouping method #grouping #method #statistics #micro #macro #class11 #rkmclasses #rkmclassesonline
RKM CLASSES
5.2K views

0:33
How Cryptographic Hash Functions Keep You Safe! 🔍 #cryptocurrency #bitcoin #blockchain #shorts
Cryptocurrency Classroom
94 views
2:24
OWASP TOP 10 - Sensitive Data Exposure / Cryptographic failures
WhiteHats
3.2K views

23:38
The Price Of Active Security In Cryptographic Protocols
Fidelity Center for Applied Technology (FCAT®)
31 views

6:31:26
Cryptographic Ledger Database, Analysis & Applications in Decentralized Blockchain & Financial World
HKEBA
71 views

37:26
A complete overview of SSL/TLS and its cryptographic system
TECH SCHOOL
136.0K views

16:03
A Cryptographic Implementation: Hybrid Encryption
Luciano Scarpaci
25 views

12:21
Rapid Prototyping of Cryptographic Systems on Chip - By Dr. Issam W. Damaj
Dr. Issam Damaj
68 views

0:31
CS8792 / Cryptographic and network security / Unit -3 (30 MCQ ) important Questions with answers..
Lincy's Style
416 views

29:55
Cryptographic hash function: Introduction
Introduction to Cryptology
3.7K views

6:06
Unplugged: The show. Part 8: Cryptographic protocols
UC Computer Science Education
14.4K views

0:47
The Enigma Machine: Cryptographic Innovator
Bored Sapien
318 views
7:57
griet-it-2012- a cryptographic technique for heterogenous sensor networks.wmv
Maruti Kumar
18 views

0:58
The Secret Codes of the Enigma Machine: Cryptographic Turning Point
History with AI
263 views

11:58
SSProve: A Foundational Framework for Modular Cryptographic Proofs in Coq (CSF 2021)
Philipp Haselwarter
44 views
17:31
BIKE - Cryptographic Engineering
Danny Silvestre Suarez
243 views

6:03
Cryptanalysis - Cryptographic Services - Network Security - CCNA - KevTechify | vid 63
Kev Techify
221 views

1:38:51
PETS 2022 Moti Yung Keynote Privacy Integrated Computing” Cryptographic Protocols in Practice
All Hacking Cons
17 views

10:14
Bitcoin - Cryptographic hash function
Khan Academy
284.5K views

1:05
The Science of Blockchain: Cryptographic Trust
Thought Shot
190 views
Page 1