Search Results for "Efficient post-quantum signatures"
Find videos related to your search query. Browse through our collection of videos matching "Efficient post-quantum signatures". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Efficient post-quantum signatures"
50 results found

29:46
Building a Diversified 20 Stocks Portfolio: Maximizing Returns with Efficient Frontier Analysis20 stocks portfolio expected return standard deviation sharpe ratio efficient frontier capital assets line CAL and tengent portfolio
Ahscholars
318 views
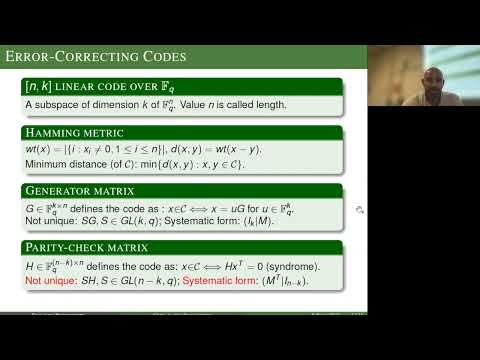
54:27
"Developing Innovative Frameworks for Efficient Code-based Signatures" - Edoardo Persichetti
De Componendis Cifris
122 views

19:58
Homomorphic Signatures with Efficient Verification for Polynomial Functions
IACR
828 views

0:15
Digital Signatures Explained | What are Digital Signatures and How Do They Work? | Digital signature
e TENDER GURU
1.6K views

1:26
E-Signatures vs. Digital Signatures (In About A Minute)
Eye on Tech
36.6K views

14:07
Hash-based signatures II - Lamport and Winternitz one-time signatures
Tanja Lange: Post-quantum cryptography
3.1K views

2:15
Electronic signatures explained – Part 3: Protecting electronic signatures with time stamps & PAdES
Signicat AS
2.8K views

9:26
Hash-based signatures V - Few-times signatures
Tanja Lange: Post-quantum cryptography
984 views

0:54
Post Fertilization events | post fertilization events in Hindi | post fertilization events biology | what is post fertilization events #cityclasses
cityclasses
34 views

1:06
Empire - Post-script: Towards a post post-Cold War era
Al Jazeera English
3 views

2:46
Post-Modern, Post-Indie, and Post-TV STREAMING NOW! - What to Watch
Cinefix
12 views

1:35
Post Delivery Girdle - Post Natal - Post Pregnancy Review
Heidecme
2 views

1:51
CUSTOM POST CARDS, CUSTOM POST CARDS, CUSTOM POST CARDS
mikebturner76
3 views

57:46
Vinod Vaikuntanathan / Efficient Fully Homomorphic Encryption from (Standard) LWE 5
Mathnet Korea
363 views

0:15
A super convenient and efficient universal grain crusher that everyone deserves the best experience
M&D Breeding equipment, fertilizer equipment
8.3M views

0:05
Logistics is the process of planning and executing the efficient transportation.
Premium Project
408.6K views
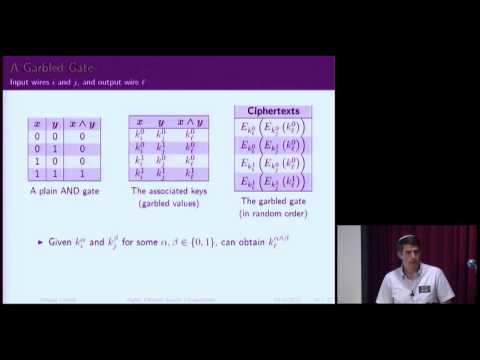
44:45
Yehuda Lindel:Highly Efficient Secure Two-Party Computation - the Road from Theory to Practice
The Open University of Israel
217 views
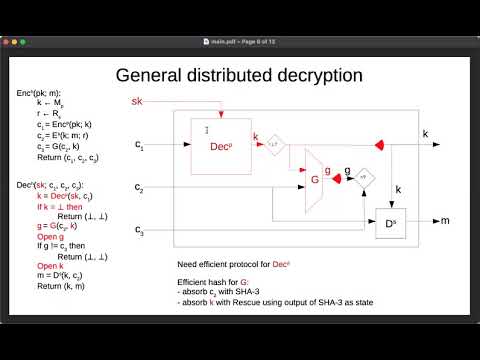
26:41
Gladius: LWR based efficient hybrid public key encryption with distributed decryption
IACR
214 views

15:06
Multiparty Key Exchange, Efficient Traitor Tracing, and More from Indistinguishability Obfuscation
IACR
287 views

0:55
The efficient compute frontier.
Welch Labs
5.4M views
3:45
Efficient Fixed Width Adder Tree Design FINAL YEAR MAJOR VLSI IEEE PROJECTS IN HYDERABAD
TRU PROJECTS
292 views
12:45
Exploiting Circular Shifts for Efficient Chaotic Image Encryption
Lazaros Moysis
112 views

14:15
Abdusalam Bashire, Homomorphic Encryption Algorithm for an Efficient E-Voting System
SEAS UDC
219 views
3:13
Efficient Zero-Knowledge Arguments in Discrete Logarithm Setting: Sublogarithmic Proof or Subli...
IACR
143 views

15:55
DOE CSGF 2022: Communication-Efficient Secure Two-Party Computation From Minimal Assumptions
Krell Institute
27 views
10:02
Thesis Mid Video || 'An Efficient DCT-based Video Steganography using Dual Fisher-Yates Algorithm'
Sk 乇qnx乡Shüvø
42 views

13:38
Image Encryption: Efficient Encryption & Compression via Random Permutation
Oladokun Pelumi
45 views

2:51:43
3-HOUR STUDY WITH ME | Hyper Efficient, Doctor, Focus Music, Pomodoro 50-10
iCanStudy
3.4M views

25:30
MiMC: Efficient Encryption and Cryptographic Hashing with Minimal Multiplicative complexity
IACR
582 views

0:37
Efficient solutions to systems of equations! SAT Review
Brian Hsieh
1.0K views

2:48
uniform embedding for efficient jpeg steganography
teja shwi
91 views

22:57
Efficient Evaluation of Activation Functions over Encrypted Data
IEEE Symposium on Security and Privacy
303 views
28:40
Time- and Space-Efficient Arguments from Groups of Unknown Order
IACR
353 views

7:59
ICCD 2021 - An Efficient Non-Profiled Side-Channel Attack on the CRYSTALS-Dilithium
陈朝晖
370 views

1:41
An Efficient Elliptic Curve Cryptography Based Without Pairing KPABE for Internet of Things
IFoxProjects
12 views

0:25
Mastering Data Structures The Key to Efficient Software Development! 💻
BioTech Whisperer
7 views
14:21
Efficient and Expressive Keyword Search Over Encrypted Data in Cloud
Micans Infotech Project CSE Video 2017-2018
136 views

59:35
Vinod Vaikuntanathan / Efficient Fully Homomorphic Encryption from (Standard) LWE 4
Mathnet Korea
244 views
23:57
Efficient Boolean Search over Encrypted Data with Reduced Leakage
IACR
206 views

0:14
5 x BitAxe Supra bitcoin home mining. Quiet, efficient and easy to setup.
BTCtutorials
28.4K views

2:55
Why Is Elliptic Curve Cryptography Efficient For Encryption? - Internet Infrastructure Explained
Internet Infrastructure Explained
1 views

20:45
Simple and Efficient Public-Key Encryption from Computational Diffie-Hellman in the Standard Model.
IACR
1.2K views

28:01
Vinod Vaikuntanathan / Efficient Fully Homomorphic Encryption from (Standard) LWE 6 -1
Mathnet Korea
110 views

24:30
A Novel & Efficient 3D Multiple Images Encryption Based on Chaotic Systems & Swapping Operations
Dr. Muhammad Hanif
915 views

1:00:15
Vinod Vaikuntanathan / Efficient Fully Homomorphic Encryption from (Standard) LWE 3
Mathnet Korea
304 views

36:20
Complexity Theory and Efficient Algorithms
Automata Hub
283 views

1:05:04
Efficient Cryptography for the Next Generation Secure Cloud
Microsoft Research
377 views
58:40
Making IP=PSPACE practical: Efficient Interactive Certification of BDD Algorithms
IFCPAR/ CEFIPRA
38 views
![Towards more Practical Secure Computation: Efficient Protocols for Secure Linear Algebra [1/2]](/image/i.ytimg.com/vi/Hs-7ixoSqAA/xhqdefault.jpg.pagespeed.ic.BPwrxXKFrf.jpg)
41:29
Towards more Practical Secure Computation: Efficient Protocols for Secure Linear Algebra [1/2]
Microsoft Research
77 views
23:10
Efficient Attribute-based Proxy Re-Encryption with Constant Size Ciphertexts
CRSInd
442 views