Search Results for "understanding hmac"
Find videos related to your search query. Browse through our collection of videos matching "understanding hmac". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "understanding hmac"
50 results found

1:15:07
Lecture 25: MAC (Message Authentication Codes) and HMAC by Christof Paar
Introduction to Cryptography by Christof Paar
63.8K views
7:24
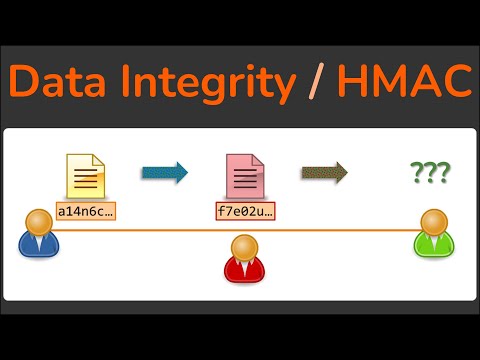
Data Integrity - How Hashing is used to ensure data isn't modified - HMAC - Cryptography
Practical Networking
77.9K views
7:05
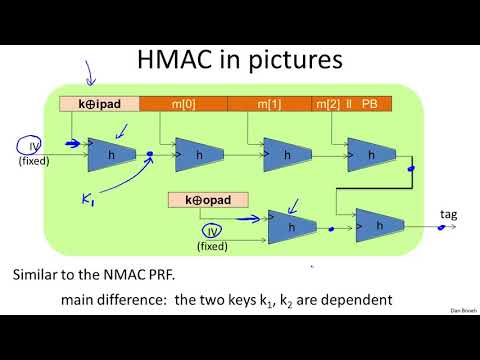
HMAC - Cryptography I
Nguyen Duong Anh
80 views

11:03
Learn the ART of CRYPTOGRAPHY - SHA-1 HMAC Hashing Explained (Urdu/Hindi)
Cybersecurity Academy - CertificationHUB
184 views

6:52
MAC / HMAC - Message Authentication Code / Hash Bashed Message Authentication Codes
Practical Networking
30.0K views

8:10
#36 HMAC (Hash Based) & CMAC (Cipher Based) |CNS|
Trouble- Free
232.6K views
22:00
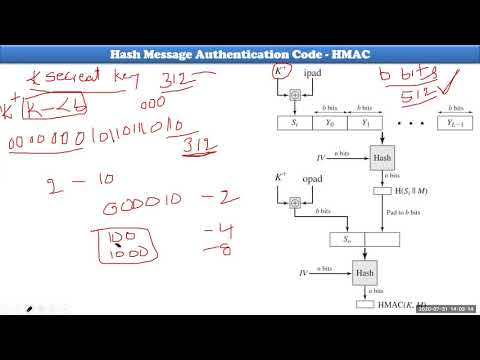
CNS HMAC
Kallam Gopala Reddy
312 views

9:00
HMAC and CMAC in Cryptography Hash Function || Network Security in Telugu
Lab Mug
10.9K views

9:24
Securing Stream Ciphers (HMAC) - Computerphile
Computerphile
326.5K views
20:35
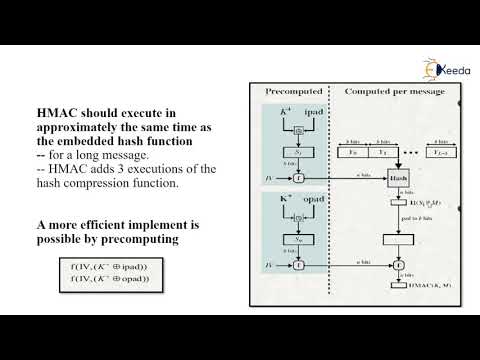
HMAC | Cryptography and Network Security
Ekeeda
677 views
1:09:59
Go UUID HMAC
Learn To Code
945 views
10:26
Razorpay integration in asp.net web app | HMac SHA256 signature create and matching
New Arts
1.4K views

0:46
HMAC Promo take 2
Players 2Pros
29 views

12:48
Função de Hash - MD5 e SHA - Código HMAC - Aula completa
Prof. Sergio Villarreal
3.7K views
57:46
Applied Cryptography: 3. Hash functions and HMAC
Applied Cryptography by University of Tartu
635 views

20:58
16-HMAC Algorithm Explained 🔐 | Hash-Based Message Authentication Code in Network Security
Sundeep Saradhi Kanthety
168.4K views
29:42
Message Authentication Code (MAC) and HMAC - Cryptography - Cyber Security CSE4003
Satish C J
37.3K views
8:08
MAC in Hindi - Message Authentication Code Process, Significance, HMAC Concept
Easy Engineering Classes
111.9K views

13:49
V4b: CBC-MAC and HMAC (Applied Cryptography 101)
Cryptography 101
1.1K views
12:51
Cryptography with Python 30: HMAC, Encrypt-then-MAC and GCM
Cyrill Gössi
1.1K views
5:15
HMAC Nested MAC Method || Lesson 73 || Cryptography || Learning Monkey||
Wisdomers - Computer Science and Engineering
1.1K views

11:19
MAC function ,HMAC,CMAC in Cryptography and cyber security tamil||CCS||Anna university reg-2021.
Murugan Tech World
7.8K views
6:09
HMAC & Message Authentication Codes (MACs) - Why Hashing alone is NOT ENOUGH for data integrity
JayPMedia
6.7K views

9:40
Message Authentication Codes: CMAC and HMAC
Cihangir Tezcan
4.8K views

6:33
HMAC explained | keyed hash message authentication code
Jan Goebel
85.3K views

7:40
MAC Based on Hash Function | HMAC in network security
Chirag Bhalodia
67.7K views

2:55
Understanding Food, Understanding the World
LORI WORLD
34 views

52:39
Understanding the Bible - Understanding God's Heart
GBI ROCK MALANG
3 views

3:13
Understanding MIDI / Understanding Samplers and Sampling
ProAudioDVDs
9 views
![[PDF] Understanding Jung Understanding Yourself [Read] Online](/image/s2.dmcdn.net/v/EF-xk1cr8X1ZRIYhy/xx720.pagespeed.ic.4H4tiGirdi.jpg)
0:08
[PDF] Understanding Jung Understanding Yourself [Read] Online
Walaamas
2 views

8:32
Understanding Computational Complexity Theory - Resources in Computation (9 Minutes)
Microlearning Daily
76 views

1:12
Understanding the Time Complexity of Function f4
blogize
1 views
1:05
Understanding the PCP Theorem
blogize
29 views

1:38
Understanding the Limitations of the Vigenere Cipher: Can Double Encryption Make It Unbreakable?
vlogize
4 views

0:30
Deeper Understanding - Georgia Tech - Computability, Complexity, Theory: Algorithms
Udacity
412 views

0:48
Is Bitcoin the Future? Understanding the Difference Between Bitcoin and Crypto
Digital Business & Crypto
517 views

8:54
Understanding Encryption! | ICT #9
Sabin Civil Engineering
328.8K views

0:35
Understanding AES Encryption: Simply Explained in 60 Seconds! #ytshorts #secure #internet
Tamilayrus - தமிழ்அய்ரஸ்
785 views

24:54
Understanding and implementing a Hash Table (in C)
Jacob Sorber
412.3K views

1:10:02
Single Systems | Understanding Quantum Information & Computation | Lesson 01
Qiskit
271.7K views

1:00:52
Quantum Circuits | Understanding Quantum Information & Computation | Lesson 03
Qiskit
77.5K views

0:56
#Shorts: What Is A Computer Encryption And How Does It Work? | Understanding Data Protection
COMPUTER LITERACY VIDEOS
85 views

0:37
NDA Geography Question Solved: Understanding Humidity #nda #geography #shorts #dw #humidity
Defence Wallah
16.6K views
5:51
P & NP Classes: Understanding Tractability in Data Algorithms @DatabasePodcasts
Database Podcasts
18 views

2:27
understanding cryptography||cipher cryptography can be divided into types
bytecode nitik
34 views

0:52
Understanding Calculus in One Minute... 🤯
Becket U
669.6K views

1:35
Understanding the get_feature_names Error in Scikit-Learn's OneHotEncoder
blogize
16 views
1:42
Understanding the Difference Between OneHotEncoder and mode_onehot_pipe in Scikit-learn
vlogize
1 views

40:24
Understanding and Explaining Post-Quantum Crypto with Cartoons
RSA Conference
31.5K views

3:15
Understanding earthquakes: The science behind what makes the earth shake | CBC Kids News
CBC Kids News
856.4K views