Search Results for "communications security"
Find videos related to your search query. Browse through our collection of videos matching "communications security". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "communications security"
50 results found

0:05
Read Error-Correction Coding for Digital Communications (Applications of Communications Theory)
Artzouig
1 views

11:33
Module 2: Network security and definitions | Communications and Network Security | Cybersecurity
Flipped Classrooms
2 views
11:45
NETWORKS AND COMMUNICATIONS SECURITY COURSERA ANSWERS WEEK 1 - 6
GILBERT ATWEKWATSE
448 views

2:05:52
Communications and Network Security | CISSP Training Videos
Simplilearn
160.9K views

11:08
Module 1: Brief introduction to cryptography | Communications and Network Security | Cybersecurity
Flipped Classrooms
2 views
![[PDF Download] Information Assurance: Security in the Information Environment (Computer Communications](/image/s1.dmcdn.net/v/D7aRX1cldHGr_Ey5g/xx720.pagespeed.ic.0AzhZq3dUt.jpg)
0:05
[PDF Download] Information Assurance: Security in the Information Environment (Computer Communications
Donammis42
1 views

0:07
Read Information Assurance: Security in the Information Environment (Computer Communications
Tegroothulsens
1 views

0:06
Read Communications and Multimedia Security. Advanced Techniques for Network and Data Protection:
Zotikishvili
0 views

0:08
Read Information and Communications Security: 7th International Conference ICICS 2005 Beijing
Zotikishvili
0 views

0:08
Read Security in Wireless Mesh Networks (Wireless Networks and Mobile Communications) Ebook
Lzakarashvili
0 views

0:07
Read Guide to Computer Network Security (Computer Communications and Networks) Ebook Online
Undiladze
2 views

0:08
Read Information and Communications Security: 6th International Conference ICICS 2004 Malaga
Chikovani 1981
0 views

0:07
Read Communications and Multimedia Security. Advanced Techniques for Network and Data Protection:
Chikovani 1981
0 views

0:05
Download Guide to Computer Network Security (Computer Communications and Networks) PDF Free
Ashjian
2 views

0:08
Read Information and Communications Security: 15th International Conference ICICS 2013 Beijing
Mlexer
0 views

0:05
Read Information Assurance: Security in the Information Environment (Computer Communications
Hecke
0 views

0:08
Read A Classical Introduction to Cryptography: Applications for Communications Security Ebook
Bbuhler
0 views

0:07
Read Information and Communications Security: 5th International Conference ICICS 2003 Huhehaote
Buxbaum
0 views

0:08
Read Communications and Multimedia Security. Advanced Techniques for Network and Data Protection:
Buxbaum
0 views

0:07
Read Security in RFID and Sensor Networks (Wireless Networks and Mobile Communications) PDF
Jeannette Paulsen
1 views

0:05
Download Security in Wireless Mesh Networks (Wireless Networks and Mobile Communications) PDF
Jeannette Paulsen
1 views

0:24
Read Information and Communications Security: 5th International Conference, ICICS 2003, Huhehaote,
Elaina Coffey
0 views

0:20
Read Communications and Multimedia Security. Advanced Techniques for Network and Data Protection:
Elaina Coffey
0 views

0:27
Read Information Assurance: Security in the Information Environment (Computer Communications and
Scott Genesis
0 views
0:25
Read Network Security: Data and Voice Communications (Mcgraw-Hill Series on Computer
Sophia Tran
0 views

0:25
Read Computer System Security: Basic Concepts and Solved Exercises (Computer and Communications
Breanna Bond
5 views

0:26
Download Guide to Computer Network Security (Computer Communications and Networks) PDF Online
London Schwartz
3 views

0:27
Read Information and Communications Security: 16th International Conference, ICICS 2014, Hong
Ciabattoni
0 views

0:26
Download Security in RFID and Sensor Networks (Wireless Networks and Mobile Communications) PDF
Giuditta
3 views
![[Read PDF] Information Assurance: Security in the Information Environment (Computer Communications](/image/s1.dmcdn.net/v/H0ZzQ1e0SUQ22BTpJ/xx720.pagespeed.ic.gf-aEABY4p.jpg)
0:24
[Read PDF] Information Assurance: Security in the Information Environment (Computer Communications
Dawoodbertrad
4 views

9:38
Asymmetric Key Cryptography Networking and Communications |Cyber Security| Ask Concept Builder
Ask Concept Builder
55 views

8:01
Web Security-Security Threats and their solution in hindi-Security Policy-computer network security
Unbeaten Learning
77.8K views

0:36
mandurah security system, home cctv security systems mandurah, cctv security systems mandurah, mandurah security systems, cctv system mandurah
lockdownse
1 views

1:56
Principles of Modern CDMA/ MIMO/ OFDM Wireless Communications NPTEL | Week 1 Quiz Assignment Answers
Coding Solutions
764 views

57:39
Cryptography; Securing Data Communications: Hardware and Software Concepts (24)
Bob Brown
54 views
4:41
Sécurité des communications - Chiffrements AES et RSA
Snlpdo Admin
101 views

3:37
Html Letter Encrypter | Securing Your Email Communications | Encrypting HTML Email Letters with Ease
JTran
5.0K views

1:35:17
Securing Future Communications with Quantum Key Distribution | Dr. Anindita Bannerjee
QuantumComputing India
627 views

27:19
97 - Quantum Communications, “Spooky” Quantum Entanglement, and Applications in the Space...
Constellations Podcast
87 views

17:39
Cryptography✅🔐🔢🙈the study of securing communications from outside observers✅🔐🔢🙈.
SomamBIKE
0 views
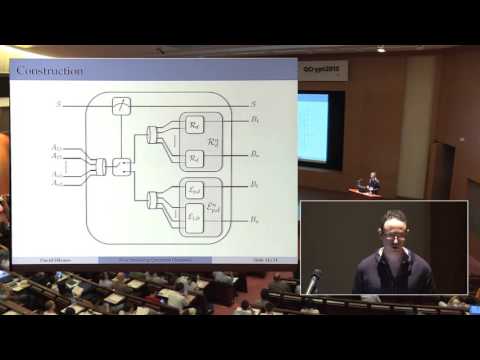
16:24
David Elkouss - Benchmarking the utility of a quantum channel for secure communications
QCrypt 2015
129 views

11:06
Communications Encryption for Preppers - Part 1 - One Time Pad
Learning Self-Reliance
21.9K views
0:11
Cryptography for Secure Communications: RSA
KD Sec n Tech
14 views

5:14
COURS DE NSI : SÉCURISATION DES COMMUNICATIONS (HTTPS) - Terminale
NOVELCLASS
5.1K views

3:15
How Does The BB84 Protocol Secure Quantum Communications? - Quantum Tech Explained
Quantum Tech Explained
13 views

0:48
Cryptographic Innovations: Safeguarding Communications
TechSavvy Plus
7 views

0:46
Romy Minko Holds an MSC in Mathematics of Cryptography and Communications
Romy Minko
23 views

1:56
PhD student explains Quantum Communications
Department for Science, Innovation and Technology
81.2K views

3:55
How does quantum cryptography work? Quantum Communications project
Pix Videos Production Company
1.2K views

0:47
The Evolution of Quantum Cryptography in Secure Communications
admn
12 views