Search Results for "Memorization technique"
Find videos related to your search query. Browse through our collection of videos matching "Memorization technique". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Memorization technique"
50 results found

0:09
Memorization technique that never failed me 😏💪🏻
Christina Wong
9.3M views

4:34
CISSP Stone Cold Memorization: The OSI Model in Domain 4, Network Security #cissp #cybersecurity
Steve McMichael - CPA to Cybersecurity
2.7K views
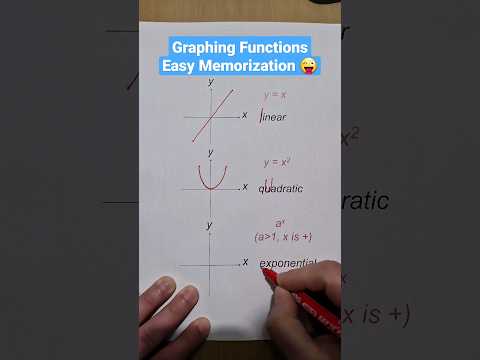
0:13
Memorization Trick for Graphing Functions (pt.1) | Algebra Tricks 😜 #math #algebra #school
NikiMath
78.8K views
1:06
Learn LOGIC over MEMORIZATION! #programming
Code Monkey
11.8K views

0:11
Graphs: Easy Memorization Tricks-1 #physics #neet #maths #education #graph
PhyEducate
121.7K views
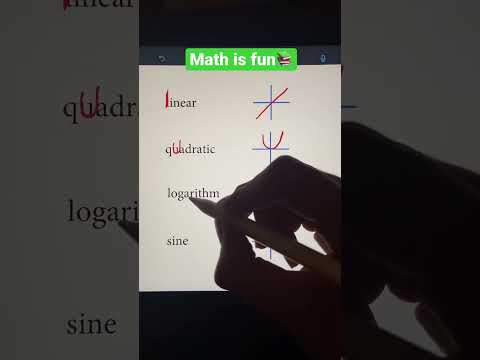
0:15
Memorization Trick for Graphing Functions Part 1 | Algebra Math Hack #shorts #math #school
Justice Shepard
32.1M views

6:47
How to Memorize Math Formulas | Math Formula Memorization
Ron White Memory Expert - Memory Training & Brain Training
133.0K views

0:06
Download Memory Tips for Math Memorization and Learning Styles: The Successful Way to Teach
Ishmael Tsuyoshi
1 views
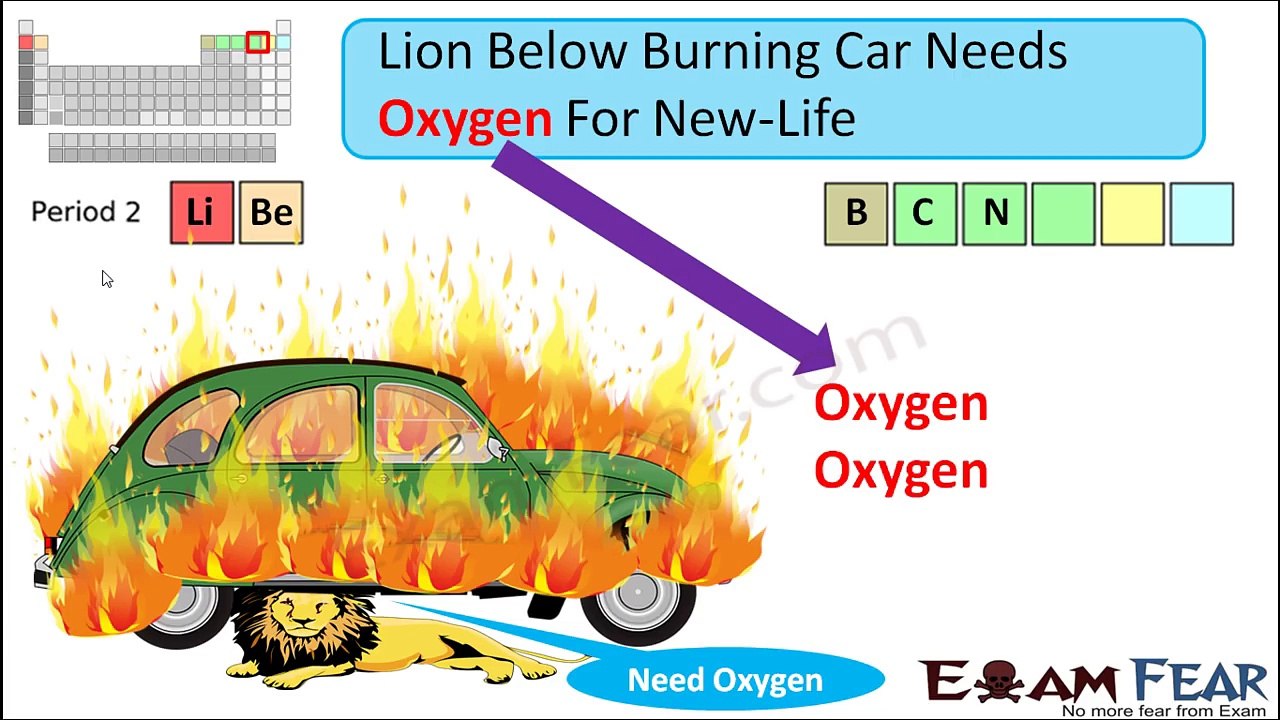
25:56
How to Memorize Periodic Table easily with Story in few Minutes (Memorization Tips)
kneeapoma
252 views

7:48
IMPORTANT MEMORIZATION TIPS AND TRICKS FOR LAW STUDENTS
Learn with Nisa Legal
6 views

7:46
Color Memorization (Amazing People - Russia)
Erwin Balines
635 views

0:11
Cryptography techniques || Substitutional technique || Transpositional technique || UNIT 01
Online Learning
5.0K views
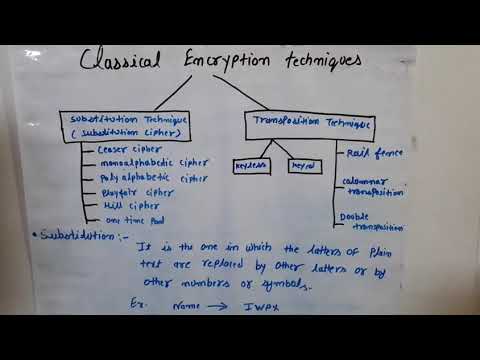
4:05
Classical encryptiin techniques, substitution technique, transposition technique
Gaurav Khatri
498 views

23:16
NIS-3.2-1 : Types of Cipher Technique (Substitution Cipher Technique, Caesar cipher)
rathod_sir
361 views

4:05
Substitution Cipher Technique V/s Transposition Cipher Technique in Cryptography and Network Securit
Short Tricks Learning
631 views

0:46
What technique do you use during competitive eating?: Competitive Eating Strategy And Technique
Scribble
1 views

5:42
Hair Cutting Technique: Mahogany Cutting Technique
Grant Sharp
8.7K views

3:05
Steganography: How to send secret file using steganography technique || by tech knowledge
tech knowledge
92 views

6:31
Hill cipher technique
Sivaraman
4 views

4:14
Row Transposition Technique|| Cryptography and Network Security
Lab Mug
7.1K views

56:41
Day 21 - What Is Image Steganography? | Secret Data Hiding Technique
Cyber SecGuru
59 views

6:17
Show, Don't Tell Writing Technique | EasyTeaching
EasyTeaching
124.7K views

7:57
griet-it-2012- a cryptographic technique for heterogenous sensor networks.wmv
Maruti Kumar
18 views

1:36
How to hide files/data behind any file using command prompt- Crptography Technique
TechSci City
1.1K views
1:01
Technique pour avouer ses sentiments à son crush 😂 #crush #sms #message #dm #histoire #humour
MrFromages
314.9K views

16:00
PLAYFAIR CIPHER WITH EXAMPLE||SUBSTITUTION TECHNIQUE||MATHEMATICS OF CRYPTOGRAPHY-- NETWORK SECURITY
t v nagaraju Technical
45.9K views

7:41
An RSA-Based Secure Image Steganography Technique Using Adaptive Data Hiding - Mid
Akash Joy
7 views

0:21
Satisfying art with glue gun technique!🎨 #art #artideas #craftideas #paintingideas #viralshorts
Mr.RS.technologist
3.0M views

31:43
Data Hiding with Encrypted Multi Secret Sharing using Modified LSB Technique
IJERT
167 views
8:21
Final Year Projects | AN OVERVIEW OF DATA HIDING TECHNIQUE:-STEGANOGRAPHY
ClickMyProject
659 views

0:10
Technique of taekwondo fight 🥋
PS Taekwondo
2.6M views
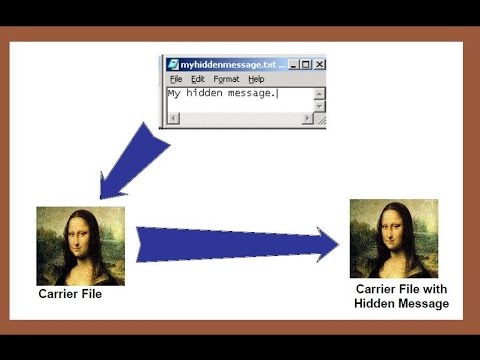
5:51
Steganography technique
Kids& Code
1.8K views

4:46
Demonstration of Implementation of Image Steganography using LSB Technique and Morse Code.
ProkillerGirl
110 views

12:59
Caesar Cipher Encryption and Decryption with Solved Example || Substitution Technique
A Z Computing
37.3K views
1:01
Kisiko Manane Ki Ninja Technique!! 🤣 😂 #k3g #srk #funny #kareenakapoorkhan #hrithikroshan #kajol
Just Chill
19.2M views

15:14
BEHAVIOURAL Interview Questions & Answers! (The STAR Technique for Behavioral Interview Questions!)
CareerVidz
663.7K views

10:53
PART 4 | HASH FUNCTION ATHENTICATION TECHNIQUE IN CRYPTOGRAPHY & NETWORK SECURITY (BANGLA)
COMPUTER SCIENCE WITH BHASKAR SIR
229 views

11:08
5 STAR Interview Questions and ANSWERS! How To Use The STAR Technique!
CareerVidz
87.8K views
2:25:42
Cryptography in network& computer security |Cryptography Encryption Technique| chapter three #በአማርኛ
Universal-tube
6.2K views

10:57
Additive Shift Ceaser Cipher Technique || Lesson 5 || Cryptography || Learning Monkey ||
Wisdomers - Computer Science and Engineering
435 views

7:38
MONOALPHABETIC CIPHER || SUBSTITUTION TECHNIQUE || CRYPTOGRAPHY || LECTURE 6 || HIRALSHASTRI
Shastri Hiral
112 views

4:55
A new image encryption technique combining Elliptic Curve Cryptosystem with Hill cipher in Matlab
OKOKPROJECTS
204 views

12:06
TRANSPOSITION TECHNIQUES || RAIL FENCE TECHNIQUE || COLUMNAR TRANSPOSITION -- NETWORK SECURITY
t v nagaraju Technical
11.8K views

16:50
The Caesar Cipher: A Simple Yet Powerful Cryptographic Technique
Harshit Jain
78 views

11:57
Playfair Cipher- Cipher Substitution Technique #CS8792 #Crypto #Security
2klearners
64 views

4:58
Mono Alphabetic Substitution Technique in CNS Cryptography & Network Security in Tamil
Won the ARREARS
21.9K views

0:39
Amazing Fishing Technique In River Big Monster Fish Video#fish#video
Attractive Fish Content
41.5M views

43:20
Encryption Techniques From Traditional To Modern Encryption Technique - Devconf2025
DevConf
61 views

0:14
Collar grab self defence technique #fighttechniques #martialarts #boxing
Kishor Joshi self defence and fitness.
7.5M views

5:09
Modified Caesar Cipher - Encryption & Decryption | Substitution Cipher Technique
Simple Snippets
15.2K views