Search Results for "hash codes"
Find videos related to your search query. Browse through our collection of videos matching "hash codes". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "hash codes"
50 results found
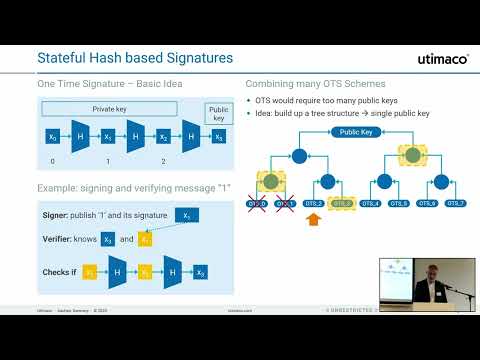
41:20
Stateful Hash-Based Signature Schemes
PKI Consortium
1.4K views

0:12
Cryptographic Hash Definition - Word of the Day
Simple Wealth Academy™️
45 views

40:28
Hash Function
Kifayat Ullah
474 views
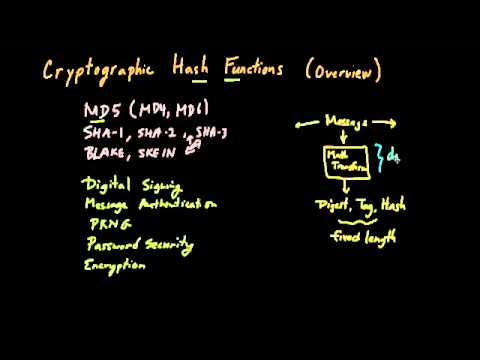
6:50
Cryptographic Hash Functions (Part 1): Overview
Sourcefire
52.3K views
24:32
C++ Builder - Hash functions, Symmetric + Asymmetric Cryptography, and Digital Signature (LockBox)
VCL Examples
3.1K views
45:47
An Introduction to Cryptographic Hash Function
Ravi Mittal
95 views

16:13
ACISP2020 Tightly Secure Chameleon Hash Functions in the Multi User Setting and Their Applications
Xiangyu Liu
230 views

13:16
Czym jest HASH i funkcja haszująca. MD5, SHA256 i wiele innych.
Dark Web Coder
13.5K views

0:20
Elon Musk - Transaction Hash Explained
Amos Dean
113 views
1:05
#OneMinuteBlockchain Five Requirements of a Cryptographic Hash Function
The Blockchain Blog
90 views
3:36
How To Create Hash SHA256 With PHP
Ridho Tegar
3.4K views

25:38
Hash-Funktionen im Detail erklärt | Teil 11 Kryptographie Crashkurs
Dr. Julian Hosp - Finanzen, Business und KI
6.1K views

49:06
Cryptographic Hash Functions (Contd...2)
nptelhrd
8.8K views

0:25
CyberSecurity Definitions | Secure Hash Algorithm (SHA)
Relative Security
3.2K views

1:02:56
Network Security - Cryptographic Hash Functions (Security Requirements and Attacks)
Waqas Ali
125 views

5:13
Cryptographic Hash Function (CHF) in Cryptography || Network Security in Telugu
Lab Mug
18.5K views
1:04:39
Message authentication and hash functions (part-1)
Keerthi Humsika K
58 views
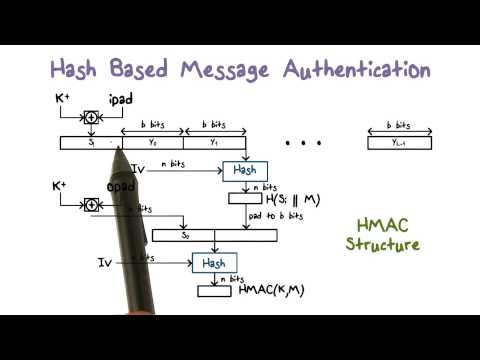
2:20
Hash Based Message Authentication
Udacity
59.1K views
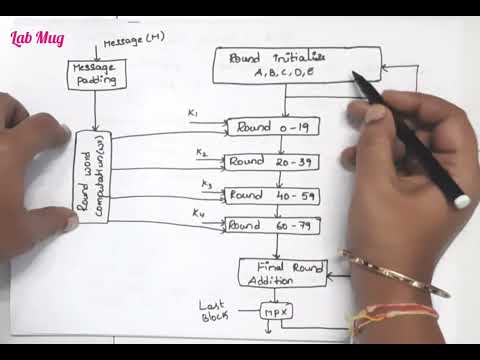
10:54
Secure Hash Algorithm (SHA) in Cryptography and Network Security #cryptography #networking #security
Lab Mug
11.2K views

7:28
Passwords & hash functions (Simply Explained)
Simply Explained
389.8K views
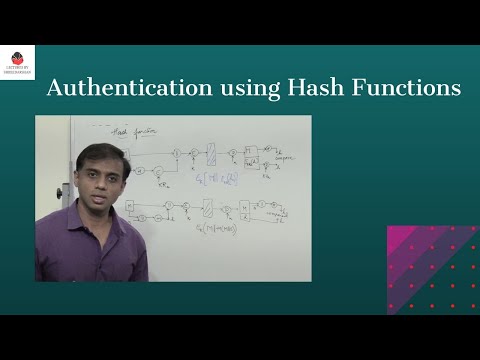
16:37
Message Authentication using Hash Functions - Network Security
Lectures by Shreedarshan K
4.3K views
25:15
Cryptography - Symmetric and Asymmetric key, Hash Function and Digital Signatures
அறிவு பரிணாமம் - Knowledge Evolution
76 views

0:56
Hash function cryptography simple explanation in a car ride #shorts #computerscience #hashfunctions
ByteSize Dialogues
4.7K views
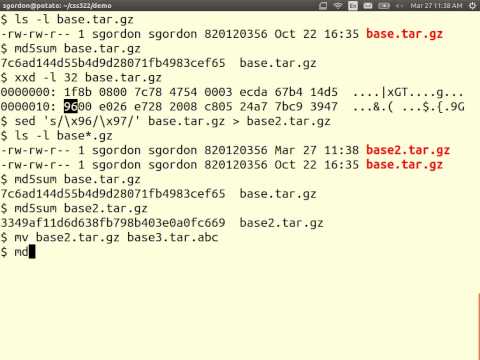
39:09
Cryptography Hash Functions (CSS322, L18, Y14)
Steven Gordon
1.1K views

0:16
🛡️Cryptographic Hash Functions 🔒 #knowledge #shorts #short #tech
TechWiseNow
81 views

50:17
An introduction to Stateful Hash-Based Signature Schemes
wolfSSL
573 views
![Basics of Crypto Part 1 - Block (SHA256 Cryptographic Hash Function) [Compact]](/image/i.ytimg.com/vi/DELAC8fWOR8/hqdefault.jpg)
1:55
Basics of Crypto Part 1 - Block (SHA256 Cryptographic Hash Function) [Compact]
Unofficed
135 views

0:36
Learn Hashing in 1 Minute | What is Hashing | How Hashing Works | Hash Function Explained #shorts
Tech Leaks
1.8K views

0:39
The TOP 3 Hash Function MISTAKES That Could RUIN Bitcoin
World Economic and Cryptocurrency News
395 views

9:50
Cryptography Explained. Symmetric and Asymmetric Encryption. Hash functions. Digital signatures.
Encyclopedia
136 views
0:12
What is hash function?
Algovenger
36.7K views

0:51
Exploring Cryptographic Hash Functions
esperanza
26 views
17:52
Hash Table - Data Structures & Algorithms Tutorials In Python #5
codebasics
425.9K views

0:36
Understanding Hash Collisions in Cybersecurity
CyberPhormX
673 views

15:47
FERMAT THEOREM,EULER'S THEOREM, EULER'S TOTIENT FUNCTION, DISCRETE & HASH ALGO IN CRYPTOGRAPHY
COMPUTER SCIENCE & ENGINEERING
84 views

0:17
hash tree | blockproof. | Blockchain Glossary
blockproof.
13 views

3:13
Brute-Force Attack on MAC - Cryptographic Hash and Integrity Protection
Ho Quang Ninh
727 views

14:14
Types of Cryptography/ Symmetric/ Asymmetric/Hash function in Hindi
Competitive Exams TechPrep
1.4K views

16:17
Hash-based signatures I - Basic concepts
Tanja Lange: Post-quantum cryptography
4.7K views

0:41
Understanding Crypto Hash Functions
Crypto Bytes Basics
74 views

48:34
ZKPodcast: Alan Szepieniec on Hash Functions & Supersonic SNARKs
Zero Knowledge
147 views

59:18
CSE571-11-11: Cryptographic Hash Functions
Raj Jain
8.1K views

0:40
What is a Crypto Hash & Why It’s Essential for Blockchain Security?
THE BIT INSIGHT
48 views

19:45
Cryptography 101: Symmetric vs. Asymmetric Explained Simply! HASH function | For Beginners |
ɢᴏᴡʀʏᴠᴇʀsᴇ
23 views
1:36:49
Winter School on Cryptography Symmetric Encryption: Cryptanalysis of Hash Functions - Eli Biham
Bar-Ilan University - אוניברסיטת בר-אילן
632 views

15:24
Cryptographic Hash Functions: Part 1
myAcademic-Scholartica
9.4K views

3:17
Cryptographic Security: Understanding Hash Functions and Their Implications for Investment in 2025
Crypto Luminary
4 views

40:57
13-Message Authentication in Cryptography 🔐 | MAC vs Hash Functions vs Encryption
Sundeep Saradhi Kanthety
234.7K views
13:26
Learn Hash Tables in 13 minutes #️⃣
Bro Code
507.5K views
1:33
Introduction to Hash Function: Simply Described by Animation
Mehdi Hatamian
359 views