Search Results for "cryptanalysis secrets"
Find videos related to your search query. Browse through our collection of videos matching "cryptanalysis secrets". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "cryptanalysis secrets"
50 results found

26:58
Cryptanalysis and its Variants, Linear Attack
Introduction to Cryptology
4.8K views
1:18:18
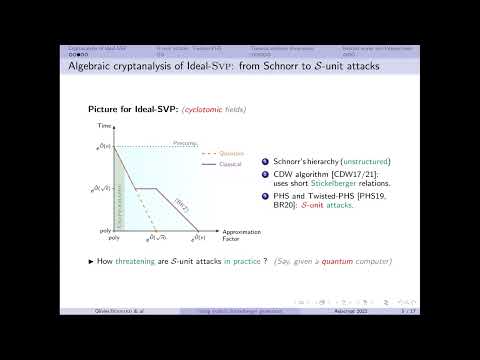
Asiacrypt 2022 Session on Lattice Algorithms and Cryptanalysis
IACR
270 views
40:45
ELEC441 - L5 - Part 2- Classical Cipher and Cryptanalysis
Tamer Khattab
122 views
37:30
Cryptography and Cryptanalysis (class-3)
The NSU Universe
8 views
0:50
Kerckhoff's principle | #cryptography | #cryptanalysis
chandu's smart class
253 views

14:21
Cryptanalysis of the Vigenère Cipher Part 2 / Classical Cryptography /Cryptography / MSc Mathematics
MATICA
532 views
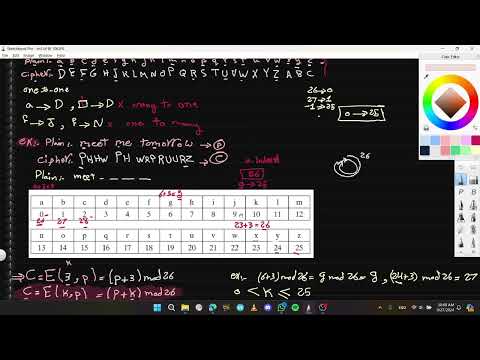
18:18
Cryptography - CH3 - pt4: Cryptanalysis for monoalphabetic ciphers
يوسف شبل — Yossef Shebl
123 views

10:34
Cryptanalysis and type of attacks
Travel and Explore
903 views

0:54
Drones' Cryptanalysis - Smashing Cryptography with a Flicker
IEEE Symposium on Security and Privacy
182 views

23:04
Basics of Cryptology – Part 21 (Cryptanalysis – The Index of Coincidence (IoC))
Cryptography for Everybody
2.4K views
2:03
Cryptography, Cryptanalysis, Cryptology
Roger Zimmerman
246 views

2:29
What is a Ciphertext-only attack in cryptanalysis?
The Security Buddy
3.4K views

1:24:32
Winter School on Cryptography: Basic Cryptanalysis - Vadim Lyubashevsky
Bar-Ilan University - אוניברסיטת בר-אילן
4.3K views

12:31
#Cryptography in Hindi 2025 Complete Guide ,#InformationSecurity,#Cryptanalysis #Cryptology, #IT_CS
Notes Tube
37 views

17:40
Cryptography Lecture 08 Types of Attacks for Cryptanalysis
5lel
216 views

24:47
Basics of Cryptology – Part 4 (Modern Cryptanalysis – Shannon's Entropy and Brute-Force Attack)
Cryptography for Everybody
5.4K views

15:42
Panel Discussion on "PQC and its impact on Cryptography and Cryptanalysis"
PKIIndia
42 views

20:45
Yu Sasaki | Cryptanalysis of Reduced NORX
Horst Goertz Institute for IT Security
132 views

24:41
Cryptanalysis of Masked Ciphers: A not so Random Idea
IACR
268 views
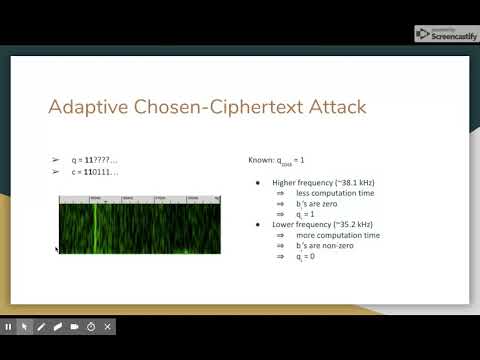
9:46
RSA Key Extraction via Low-Bandwidth Acoustic Cryptanalysis
Jade Liu
132 views

56:02
session-6: Symmetric Cryptanalysis
IACR
256 views
59:25
Symmetric Cryptanalysis 1 (Crypto 2023)
IACR
117 views
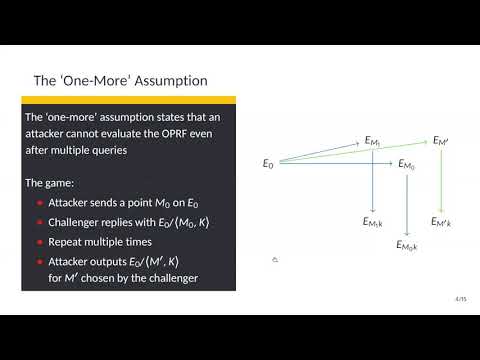
27:06
Cryptanalysis of an oblivious PRF from supersingular isogenies
IACR
121 views
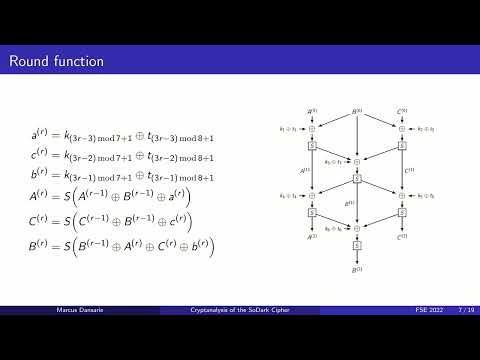
16:15
Cryptanalysis of the SoDark Cipher for HF Radio Automatic Link Establishment
IACR
233 views
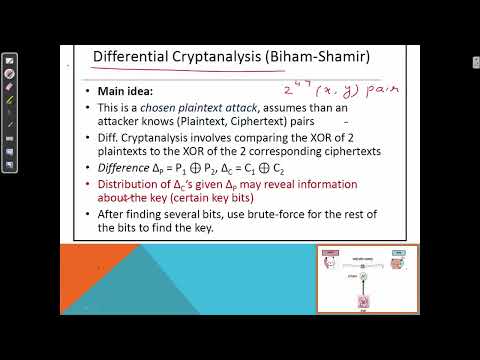
15:48
Cryptanalysis of DES - Week 7 (1/4)
ChupaniMunyanyo
50 views
0:11
DISA icai Cryptography, Cryptology, Cryptanalysis
CA Rajat Agrawal - ProKhata
228 views

1:29:58
Differential Cryptanalysis: an Introduction for Humans
OWASP Cape Town
3.0K views

1:15:11
Day 2 Session 1 / Cryptanalysis and side - Channel Analysis I
Ingeniería, Ciencia y Tecnología - URosario
92 views
7:30
Cryptanalysis: breaking the code
The Math Multiverse
77 views

56:30
Linear Cryptanalysis
nptelhrd
30.7K views

24:06
Vigenère Cipher Cryptanalysis Revisited – The Undeciverable Cipher Deciphered
Cryptography for Everybody
13.1K views
1:43:52
ACNS 2018 - Session 7 Symmetric key cryptanalysis
COSIC - Computer Security and Industrial Cryptography
46 views

11:25
Cryptanalysis 6.5: Experimentally Verifying a Theoretical Distinguisher
Cihangir Tezcan
255 views

9:10
Cryptography and Network Security- Introduction to Encryption, Decryption, Cipher, Cryptanalysis
WELCOME ENGINEERS
195 views

5:34
Cryptanalysis and its types in Hindi | What is Cryptology in Network Security
Bakchod Engineer
57 views

21:36
Cryptanalysis 7.3: Impossible Differential Attack on HIGHT Block Cipher
Cihangir Tezcan
412 views
22:12
Differential Cryptanalysis - talk 2/2 (FSE 2025)
IACR
20 views
19:28
Linear Cryptanalysis of DES with Asymmetries
IACR
669 views
0:20
Create an AI data encryption hacker 🔥🔐? #shorts #worldrecord #hacker #bruteforce #cryptanalysis
CR!BA⊥
219 views
1:37:51
Session on Cryptanalysis II
IACR
174 views

0:58
Drones' Cryptanalysis - Smashing cryptography with a Flicker
Cyber Security Labs @ Ben Gurion University
2.4K views

8:18
2.2 Cryptography and Cryptanalysis
EngiNerd
144 views
4:29
Difference between Cryptography, Cryptology and Cryptanalysis | Information Security Lectures Hindi
Easy Engineering Classes
11.7K views
![[cryptography series] episode 2 : "cryptanalysis"](/image/i.ytimg.com/vi/aay2eN0q-cc/hqdefault.jpg)
20:29
[cryptography series] episode 2 : "cryptanalysis"
CLEARSEC
260 views
7:37
Multimedia - Cryptology - Cryptanalysis - Playfair Cipher - Arabic - Video 6 continue
Alaa Abdelmohsen
108 views

0:39
How to say "cryptanalysis's"! (High Quality Voices)
/ The WordBox / #1 Pronunciation Guide Videos
2 views

21:57
Cryptography and cryptanalysis (Lecture Two-1) Dr. Faez
Mathematics Department\ Mustansiriyah University
186 views

18:58
Panel Discussion on "PQC and its impact on Cryptography and Cryptanalysis"
PKIIndia
15 views

11:19
Cryptanalysis of RSA using Genetic Algorithm | Research paper Review
khanjan joshi
170 views
15:21
AI Driven Cryptanalysis | breaking codes and strengthening security
Tharunika
2 views