Search Results for "ai-powered attacks"
Find videos related to your search query. Browse through our collection of videos matching "ai-powered attacks". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "ai-powered attacks"
50 results found

47:07
Live sessions Sep 30 - session Quantum Algorithms, Attacks and Models (director's cut)
PQCrypto conference videos
130 views

3:35
Will the US Be Able to Withstand Cyber Attacks on Critical Infrastructure? | GZERO World
GZERO Media
1.5K views

1:03:37
Cryptography as a Network Security Tool in Hindi Urdu|Types of cryptography attacks LECTURE 10
Virtual Comsats
1.0K views
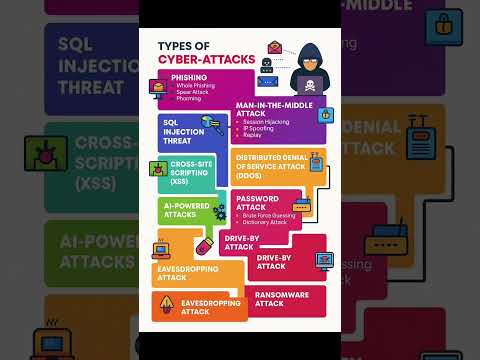
0:16
Types of Cyber-Attacks!!! #ccna #cybersecurity #networking #programming #techshorts #cryptocurrency
Networks Professionals
11 views

7:33
10 Most Common Cybersecurity Threats | Types of Cyber Attacks | Cybersecurity for Beginners |
E-Software Hub
4.2K views
0:52
Apple Reinforces iMessage Security Against Quantum Computer Attacks
Pick Digi
62 views
13:45
COURSERA:INTRODUCTION TO CYBER SECURITY TOOLS AND CYBER ATTACKS | WEEK 3:KEY CONCEPTS| QUIZ ANSWERS
Anand Ranjit Kumar Mukkala
15.0K views
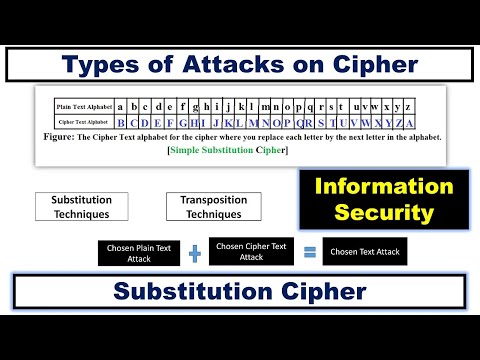
6:09
Types of Attacks on Cipher ~xRay Pixy
Ritika xRay Pixy
789 views

8:34
0317 Attacks on cryptography
Free Tech Courses
0 views

9:15
1.0: Security Goals and attacks- Cryptography and System Security
Ishita Lalan
12 views

1:33
UK accuses Russian military intelligence of global cyber attacks campaign
FRANCE 24 English
1.1K views
![Alfonso Muñoz - Stego attacks by design. A deep dive about stegomalware & ... [RootedCON2020-ES]](/image/i.ytimg.com/vi/5udFjDbSEaA/hqdefault.jpg)
1:02:26
Alfonso Muñoz - Stego attacks by design. A deep dive about stegomalware & ... [RootedCON2020-ES]
Rooted CON
844 views

28:41
USENIX Security '16 - Dancing on the Lip of the Volcano: Chosen Ciphertext Attacks on Apple iMessage
USENIX
186 views
3:04
Is Quantum Cryptography Vulnerable To Side-channel Attacks? - Quantum Tech Explained
Quantum Tech Explained
8 views

9:34
(CH7/2) Cryptography - Types of Cybersecurity Attacks Part 2
FENIXSOYA
30 views

8:26
Cryptography Part 6 - Cryptanalytic Attacks
Tom Olzak
6.3K views

55:57
Obvious in Hindsight From Side Channel Attacks to the Security Challenges Ahead
IACR
2.6K views
2:48
How Does Post-quantum Cryptography Protect Data From Attacks? - Emerging Tech Insider
Emerging Tech Insider
2 views

3:21
How Do Classical Side-channel Attacks Impact Quantum Cryptography? - Quantum Tech Explained
Quantum Tech Explained
2 views

10:34
Cryptanalysis and type of attacks
Travel and Explore
903 views

2:37
What are the Biggest Cyber Attacks on Critical Infrastructure? - Ask Archer
Archer
228 views
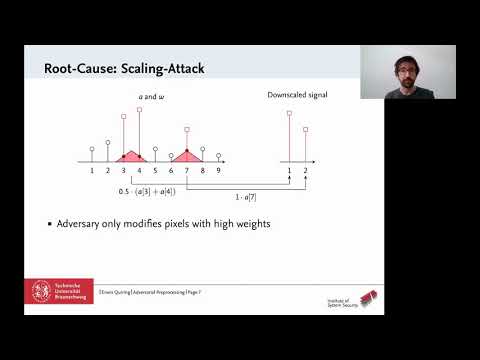
11:15
USENIX Security '20 - Adversarial Preprocessing: Understanding and Preventing Image-Scaling Attacks
USENIX
817 views
0:19
The 4 Types Of Web Attacks Every Pentester Should Know!
Infosec Mastery - Ethical Hacking for Beginners
322 views

17:40
Cryptography Lecture 08 Types of Attacks for Cryptanalysis
5lel
216 views

9:31
Cryptographic Attacks - CompTIA Security+ SY0-701 - 2.4
Professor Messer
116.9K views

5:15
Inside AIS-189: How India’s Cars Are Getting Cyber-Protected || Cyber Attacks || Cryptography
Gettobyte
2 views
0:06
phishing #cybersecurity #cyber #attacks #shorts
Cybergram
272 views

3:41
Jonas Vingegaard's Top 5 Most ICONIC Attacks
Finlay Oliver
64.7K views
3:40
How Hackers Perform Online Password Cracking with Dictionary Attacks
Null Byte
192.8K views
9:37
cryptography and network security: Introduction, security goals, attacks,services and techniques
Pravisha candideyes
145 views

14:08
Attacks-Malicious Code-Brute Force(KTU CS 472 Principles of Information Security-S8CS-Mod 1 Part 6)
KTU Computer Science Tutorials
1.3K views

3:16
What is Cyber Security? How You Can Protect Yourself from Cyber Attacks
Kaspersky
99.4K views
1:05:34
Winter School on Cryptography Symmetric Encryption: Attacks Against Record Layers - Kenny Paterson
Bar-Ilan University - אוניברסיטת בר-אילן
570 views

0:11
🐅🐕 Tiger Attacks House Dog! #cctv #viral #ai
CCTV-Vision
3.1M views
0:28
The 2 Deadliest Cyber Attacks Hitting Every Business
Cyber Houston
928 views
3:51
Cryptanalytic Attacks
Prabhu Subramanian Lectures
18.8K views

3:48
Aquaman (2018) - The Trench Attacks Scene (7/10) | Movieclips
Movieclips
2.7M views

0:05
Types of Password Attacks #cybersecurity #networking #shorts
Build IT Skill
926 views

0:59
PhiLock-Q The zenith of computer encryption vs quantum attacks
WILLIAM HUNTER
865 views

1:06
Quantum Attacks: Are Your Encryption Algorithms Safe? (RSA, ECC, AES)
THE PREMINENT
197 views
5:56
Watch this to prevent DDoS attacks...
Jelvix | TECH IN 5 MINUTES
33.3K views

11:01
Attacks on Subscriber Watermarking Technologies - IABM Future Trends Channel Presentation
Friend MTS
92 views

48:11
Public Policies to Protect Critical Infrastructure from Cyber Attacks
International Society of Automation - ISA
727 views

14:11
Dengue attacks continue in Sindh | ARY News 7 AM Headlines | 1st Nov 2025
ARY News
5.3K views

5:13
20 Cryptographic Attacks
Consuelo guevara
9 views
3:55
How Hackers Break Encryption | Cryptanalysis Attacks Made Simple
Cyber Technology
83 views
11:18
Cryptography Attacks - Security+ SY0-601 1.2.13
Cyberkraft
515 views
8:46
Agent Ching Attacks – Full Film | Hindi | Atlee & Ranveer | Sreeleela, Bobby Deol
Ching's Secret
85.0M views

12:06
7 3 Chosen ciphertext attacks 12 min
Jake Danniel
329 views

0:45
Social Engineering Attacks | TapSwap Curious Facts
TapSwap Official
3.7K views