Search Results for "secure hash algorithm 256"
Find videos related to your search query. Browse through our collection of videos matching "secure hash algorithm 256". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "secure hash algorithm 256"
53 results found

12:36
MD5 Algorithm | What Is MD5 Algorithm? | MD5 Algorithm Explained | Network Security | Simplilearn
Simplilearn
125.9K views

7:34
RSA algorithm example|rsa algorithm encryption and decryption example|rsa example|rsa algorithm
Last Night Study
143.8K views

9:05
RSA Algorithm | RSA Algorithm Concept | RSA Algorithm with Example | Hindi / Urdu
Ask Faizan
1.8K views

23:17
RSA Algorithm || Rivest Shamir Adleman Public Key Cryptographic Algorithm || RSA Algorithm example
Dr. Riaz Khan
405 views

12:08
RSA algorithm|RSA algorithm example|rsa algorithm in cryptography and network security|RSA example
Last Night Study
3.3K views

9:10
RSA Algorithm Example | rsa example | rsa algorithm | rsa algorithm bangla | Zobayer Academy
Zobayer Academy
3.5K views

2:51
What is an Algorithm | How to write ALGORITHMS | Algorithm for Beginners | Introduction to Algorithm
Epic Learning
68.8K views

0:03
Algorithm types and algorithm examples #algorithm #factorial
Math360
173 views

0:54
What Exactly is An Algorithm? - Algorithm Explained - With Examples #datastructures #algorithm
Hazy Genesis
965 views

19:15
Hash Functions in hashing, Hashing in data structures, Types of hash functions, division method
CSIT Tutorials by KanyaKumari
4.5K views

7:53
Introduction to Hashing|Hashing in Data Strucutures|What is Hashing|Hash Table|Hash function
Scratch Learners
107.6K views
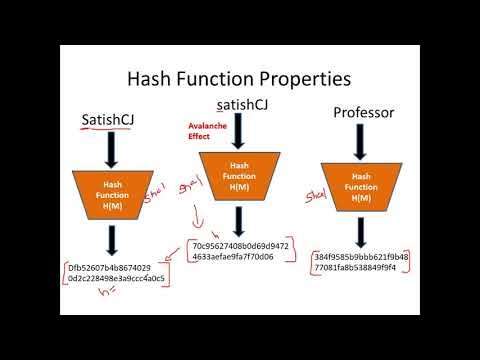
44:53
Introduction to Hash Functions and Application of Hash Functions in Cryptography - CSE4003
Satish C J
24.6K views

25:51
Hash Tables: Hash Functions, Sets, & Maps - DSA Course in Python Lecture 4
Greg Hogg
84.9K views

13:56
Hash Tables and Hash Functions
Computer Science Lessons
1.7M views

13:39
Introduction to Hashing in Data Structure | Hash Table, Hash Function | DSA using Java #56
ForMyScholars
27.2K views

26:41
What is HASHING ? | Why do we NEED it? | What is a Hash Function | (Example - Array vs Hash Table)
Simple Snippets
9.5K views

0:17
What is Hash and what it is used for? |#blockchain #blockchain #Hash #block #BlockchainSeekho
Blockchain Seekho
1.2K views

1:34
Hash Security, Pass-the-Hash, and PKI Explained | Security+ in 60 Seconds
Cyber Buddy
40 views
![[HINDI] What is a Cryptographic Hash? | Hash Functions | Hashing v/s Encryption | Beginner's Guide](/image/i.ytimg.com/vi/qMemCPACnWw/xhqdefault.jpg.pagespeed.ic.G9pQ20ONPm.jpg)
12:21
[HINDI] What is a Cryptographic Hash? | Hash Functions | Hashing v/s Encryption | Beginner's Guide
Bitten Tech
35.7K views

13:13
Hashing in Data Structure - Hashing in DSA - Hash Table - Hash Function - Collisions - Load Factor
Coding With Clicks
1.9K views

4:39
Reggae Instrumental Beat || Hash Hash
Purple Six Beats
22 views

3:06
Papas hash brown - Hash Browns
Cocina al Natural
4 views

6:03
Waffled Hash Browns - #BreakfastwithAB - Hash Brown Recipe
just cooking
4 views

3:27
Hash brown _ Hash brown recipe
RAUF KITCHEN TIPS
0 views

8:19
LEC11| Blockchain | Cryptographic Hash Function & Properties of Hash Function by Mrs. G. Sowmya
MLID - MLR Institute of Technology
2.3K views

37:31
Five* non-cryptographic hash functions enter. One hash function leaves.
Linux.conf.au 2016 -- Geelong, Australia
4.7K views

58:18
How to make hash, hash oil, and marijuana butter
Billman2112
6 views

5:19
How to make Hash oil with Hash and Aceton (QWACETON) and smoking it.
Carolyne Jeffries
158 views

2:18
BRUSSELS SPROUTS HASH WITH EGGS - brussels sprouts hash and eggs
huong tran
16 views

9:29
Blessings Breakfast in Hash Cafe || Sarapan penuh berkah di Hash cafe || MaMiTa ViVa
MaMiTa ViVa
1 views

0:35
Bubble Hash | Check out Automatic Bubble Hash Equipment
Aether Green
8 views

3:39
Hash Identifier in Kali Linux - Find-My-Hash in Kali Linux, Kali Linux Full Course (part-37)
HD Movies Only
6 views

3:19
video sur plusieur sorte de hash cannabis weed hash
thc_thr
1 views

16:12
Bubble Hash | Find Out the Automatic Bubble Hash Washer
Aether Green
57 views

0:46
What Is Hash Collision and What Does It Mean To Be Resistant To Hash Collisions?
Binance Academy
1.3K views

7:40
Hash function based on CBC in cryptography | Hash function based on cipher block chaining
Chirag Bhalodia
24.0K views

3:43
Mr Hash - Le gardien de la crypte (Prod : Mr Hash)
zeblakinho
112 views
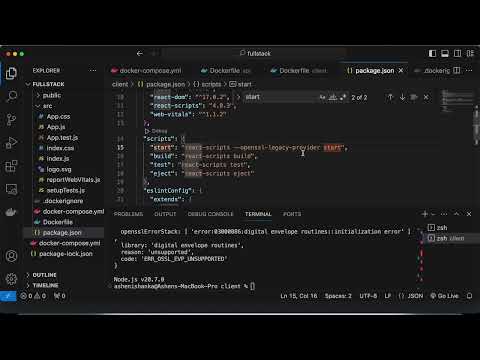
1:14
error:0308010C:digital envelope routines::unsupported at new Hash (node:internal/crypto/hash:68:19)
Coffee Programmer
11.5K views

10:47
Hash function | S8 ECE | SECURE COMMUNICATION
bushara abdulrahim
3.1K views

0:35
Cracking The Code - Exploring Secure Hash Algorithms - SHA Short #cybersecurity #hashing
Technically U
1.1K views

16:13
ACISP2020 Tightly Secure Chameleon Hash Functions in the Multi User Setting and Their Applications
Xiangyu Liu
230 views

1:02
How does a hash help secure blockchain technology #BlockchainSecurity #HashFunction #crypto
Cryptobit
9 views

5:45
What is a crytographically secure hash function?
internet-class
1.3K views

0:13
Difference between unconditionally secure and computationally secure in cryptography and .....
SUKANYA BASU
973 views

8:37
SSH (Secure shell) protocol in Hindi | Secure shell protocol in Network Security
Abhishek Sharma
84.3K views

46:18
Roll Your Own Secure Cloud Storage with SSHFS - Secure Shell File System - Hak5
Hak5
5 views

4:10
Difference between Computationally Secure and Unconditional Secure Cipher | Information Security
Easy Engineering Classes
6.4K views

0:55
Overview of Secure Aggregation #ai #artificialintelligence #machinelearning #aiagent Overview Secure
NextGen AI Explorer
12 views

2:05
Secure USB Flash Drive - SanDisk Enterprise Secure ...
John Objet
1 views

0:05
Read Secure Software and Comm. on Handheld Devices: Secure Software and Communication on Handheld
Isaksen
2 views
24:20
"தமிழ்நாட்டில் மன்னர் ஆட்சியை ஒழிக்கணும்" -VCK Aadhav Arjuna | Vijay | DMK | Oneindia Arasiyal
Oneindia Tamil
1.9K views

1:00
Encryption_ The Art of Protecting Secret
Badea3
244 views

3:24
Jasminer X16-Q 1950M: Crypto Hardware Ethash ETHW ETC Mining Machine Overview
Beacon Tech
704 views