Search Results for "lecture by bhanupriya"
Find videos related to your search query. Browse through our collection of videos matching "lecture by bhanupriya". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "lecture by bhanupriya"
50 results found

1:39:59
Lecture-18 (Cryptanalysis and DES)
Satyanarayana Reddy Arikatla
25 views
9:18
Extended Euclid Algorithm - Number Theory Advanced | C++ Placement Course | Lecture 37.1
Apna College
36.4K views
25:35
Week 2 : Lecture 11 : Principle of Cryptography: Part 1
NPTEL IIT Bombay
476 views

14:46
32) STATE ELIMINATION METHOD (FA to RE conversion) # ToC Lecture 32
Greeshma G S
7.9K views

2:16:00
Quantum computers. Lecture #10: Golden single qubit circuit. Ramsey. No cloning. Cryptography.
QTM Lab
137 views

25:00
Lecture 4. Bluetooth Security (Applied Cryptography 101: Real-World Deployments)
Cryptography 101
878 views

7:55
Symmetric & Asymmetric Cryptography | Why use Cryptography | Symmetric Cryptosystems | Lecture 6
Tinker Tech
61 views

37:21
Introduction to number theory lecture 18. Cryptography
Richard E Borcherds
8.4K views

9:39
Lecture 1 Introduction to Finite Automaton
WeightedFiniteStateTransducers
12.0K views

1:37:06
Calculus 1 Lecture 0.2: Introduction to Functions.
Professor Leonard
1.2M views

56:30
Algebraic Topology: Chains, Cycles, and Homology Classes - Oxford Mathematics 4th Year Lecture
Oxford Mathematics
6.5K views

12:42
Blockchain | Lecture 2 | Cryptography Primitives
Dr. Bipin Kumar Rai
736 views
4:14
The Boring lecture Survival
ashish chanchlani vines
44.4M views

19:34
Discrete Mathematics Lecture 2 | Principle of Mathematical Induction By Dr.Gajendra Purohit
Dr.Gajendra Purohit
1.3M views

42:03
THEORY OF COMPUTATION | FINITE AUTOMATA | LECTURE 02 | ALL UNIVERSITY | PRADEEP GIRI SIR
Pradeep Giri Academy
11.3K views

5:57
Trojan horse in cyber security | trojan in cyber security | Lecture 30
Simply Made
55.9K views

0:34
🔄 Public vs Private IP & NAT Explained | GATE 2026 CN Lecture | KnowledgeGate Live 9PM
KnowledgeGATE by Sanchit Sir
204 views

11:47
Understanding Parser and CFG | Left and Right Recursion | Compiler Design Lecture 11 | GTU 3170701
Engineering Unit
68 views

22:06
Lecture 4: Tautology, Contradiction & contingency, Unit-4, Discrete Mathematics. BKNMU
Jay K. Vadher
81 views

15:39
Computer system security unit 1/Hand written notes lecture 1 Aktu
Travelling with NIRO
208 views
7:00
IQIS Lecture 1.7 — Complexity classes
Artur Ekert
11.3K views

1:17:25
Lecture 1: Introduction to Cryptography by Christof Paar
Introduction to Cryptography by Christof Paar
872.8K views

11:38
Olivier Norek ! #booktube #lecture #auteur #polars
Madame rêve Encore de livres
825 views

1:26:46
Lecture 1 | Quantum Aspects of Cryptography
Atul Singh ARORA
97 views

15:09
IQIS Lecture 5.7 — Quantum key distribution
Artur Ekert
6.7K views

7:57
(NUMBER THEORY) Lecture 13: Primality test
Khadija Shakeel
551 views

6:46
Lecture 37 - Quantum Cryptography protocols -3 | Quantum Computing
THE QUANTUM SCIENTIST
37 views

23:50
Lecture 6: Data Encryption Standard (DES): Key Schedule and Decryption by Christof Paar - Summary
Youtube Summaries
6 views

41:24
Discrete Mathematical Structures, Lecture 3.7: The Euclidean algorithm
Professor Macauley
1.5K views

6:52
Symmetric key cryptography, cyber security lecture series part -17
Gaurav Khatri
457 views

21:37
Diffie-Hellman Key exchange Algorithm | Lecture | Cryptanalysis | Cryptography
Cybersecurity Mechanic
592 views

1:03:35
Digital Forensics in Action: Encryption, Decryption & Steganography Explained (Lecture 13)
Cipherbase technologies
46 views

9:25
Automata Theory : Lecture #1: Introduction to Automata Theory
Sharon Roji
178 views

54:20
History of Mathematics: Classical algebra: 19th-century beginnings of modern algebra. 3rd Yr Lecture
Oxford Mathematics
8.1K views

1:51
Matrix lecture 33 | possible eigen values of idempotent matrix | Kohei Adachi | GATE | CSIR-NET
AJEDU • 10M•
41 views

30:37
Unit 5 Cryptography Lecture 6 Part I 21 12 2020 EC 71 72
Ashish Mishra
2 views

7:34
Security in Digital Image Processing:Importance of Digital Image Security: Module V,Lecture 5,EC703A
Dr. SANGITA ROY
28 views

1:36:56
Automata, Verification and Infinite Game Lecture - 8
STCS TIFR
19 views

10:05
RSA Example Lecture 1 | p=7, q=11, plaintext=m=9, Find public key (e), private key (d) & ciphertext
TRN CSE Tutorials
2.2K views
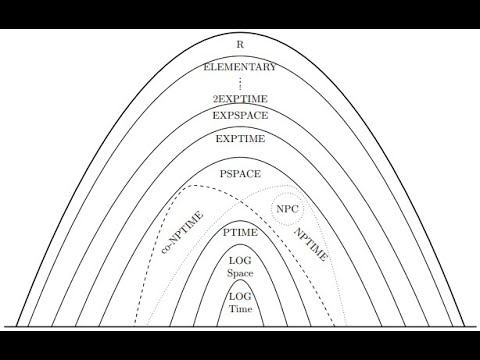
27:35
Preliminary Philosophy (Computability Theory Lecture 1)
Tex Talks
1.6K views

27:57
''Introduction to Cryptography'' Computer System Security Lecture 01 By Ms Chelsi Sen, AKGEC
AKGEC Digital School
99 views

4:19
lecture 1 type of cryptography.#viral #network #security #engineering #cipher
GainThroughIT
6 views

28:09
Triple Integration | Evaluation of Triple Integration Problems | Engineering Mathematics | Lecture 1
Abhijeet Men Academy Amravati
68 views
![Lecture - 2 on Cryptography [ Classification of Cryptography, part 1 ] With a story](/image/i.ytimg.com/vi/3gV7Fj0vHbQ/hqdefault.jpg)
9:57
Lecture - 2 on Cryptography [ Classification of Cryptography, part 1 ] With a story
afroza sultana
148 views

1:21:16
Cris Moore - "Sending Secrets: Cryptography & Privacy in a Quantum World" (C4 Public Lecture)
Santa Fe Institute
611 views
7:38
MONOALPHABETIC CIPHER || SUBSTITUTION TECHNIQUE || CRYPTOGRAPHY || LECTURE 6 || HIRALSHASTRI
Shastri Hiral
112 views

18:31
CISSP Lecture 41 CISSP Security Operations
URDUIT Academy
2.4K views

1:19:38
John Hennessy and David Patterson 2017 ACM A.M. Turing Award Lecture
Association for Computing Machinery (ACM)
144.9K views

1:08:56
IMS Public Lecture: Alan Turing, Computing, Bletchley, and Mathematics
Institute for Mathematical Sciences
170 views

44:15
Computability Theory - Lecture 08 - Bart Kastermans
Kiseki No Sedai
36 views
Previous Page 2