Search Results for "kerberos in network security"
Find videos related to your search query. Browse through our collection of videos matching "kerberos in network security". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "kerberos in network security"
50 results found

3:04:03
Cryptography and Network Security - Cryptography and Network Security Full Bangla Course
BD Techno Expert
1.2K views

7:31
A MODEL FOR NETWORK SECURITY -- NETWORK SECURITY
t v nagaraju Technical
14.7K views

0:11
Cryptography & Network Security #computer#network #security #secret #hacker #ethics #ethicalhacking
Right Ideas(Y!)😉
1.9K views

9:06
A Model for Network Security in cryptography and Network Security || Cryptography and NS
Lab Mug
10.9K views

9:25
Principles of Public key cryptography in Network Security || Cryptography and Network Security
Lab Mug
7.1K views

1:50
Network security project output - Network Security Project
Academic College Projects
11 views
1:15
Network Security Thesis output - Network Security Thesis for Research Scholars
Academic College Projects
12 views

10:16
Best Network Security Auditing Tool And Analysis Network Security
Crazy World
0 views

5:03
Checking the health of Security Network Protection and Security Network IPS sensors
Al Quran
6 views

2:24
Trusted System:Trusted System in network security| cryptography and network security| ICS|CNS |Hindi
Zixplain
15.7K views

1:20
Projects on Network Security and Cryptography | Thesis on Network Security and Cryptography
Phdtopic. com
516 views

18:03
02-Types of Attacks in Network Security | Active vs Passive Attacks | Cryptography &Network Security
Sundeep Saradhi Kanthety
406.7K views

4:49
Kerberos Authentication Protocol | Cryptography and System Security
Ekeeda
56 views

7:46
Kerberos in Cryptography and security systems | CSS series #8
Last moment tuitions
75.9K views
0:44
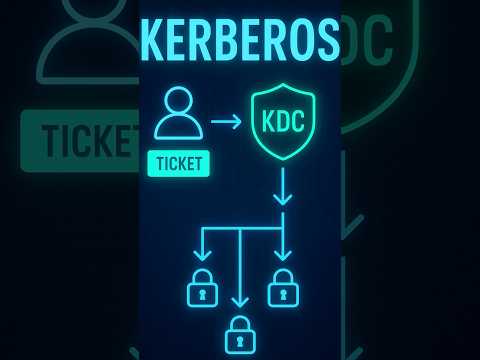
Kerberos Authentication Explained | How Login Tickets Work in Enterprise Security #CISSPFlashcards
Cyber Security Learning
3.2K views

5:51
Module 5: Kerberos | Security Architecture and Engineering | Cybersecurity
Flipped Classrooms
20 views

8:29
Kerberos in Tamil | Cryptography and Cyber Security in Tamil | Unit 4
4G Silver Academy தமிழ்
26.0K views

2:47
IP Security overview, IP Security architecture, Cryptography and Network Security.
Algorithm Pod
488 views

1:01:28
Cryptography & Network Security | CH1.2 The OSI Security Architecture & 1.3 Security Attacks
Computer & IT lectures
67 views

7:32
CRYPTOGRAPHY AND NETWORK SECURITY(2) Principles of security, Security Services
Algorithm Pod
143 views

8:46
Security Mechanisms | Computer Network Security | Information and Cyber Security |Full Course|Lec-04
Abhideep Online Education
11.7K views

6:31
Network Security vs Cyber Security | What is Security? | Explained in Hindi
Tech Guru Manjit
16.0K views

12:12
#5 Security Mechanisms In Network Security | Information Security |
Trouble- Free
71.0K views

0:06
Read Security+ Guide to Network Security Fundamentals (Cyber Security) PDF Free
Tbestavashvili
1 views

14:40
SECURITY ATTACKS || TYPES || ACTIVE || PASSIVE || OSI SECURITY ARCHITECTURE --NETWORK SECURITY
t v nagaraju Technical
35.3K views
45:59
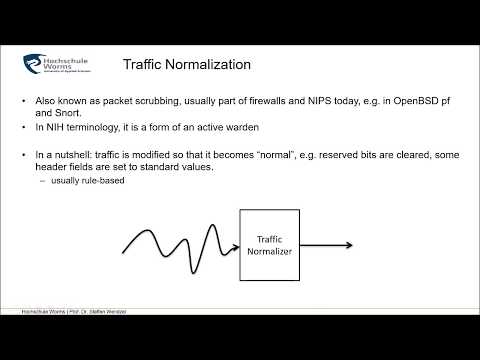
01731, Network Steganography / Network Information Hiding, Chapter 7a Network-level Countermeasures)
Steffen Wendzel
812 views
6:33
What Is Network Marketing Network Marketing Explained! What Is Network Marketing Anyways
Most Popular Videos
1 views

11:37
What is Pi Network | Pi Network in Pakistan | Pi Network kya Hai | Pi Cryptocurrency Review in urdu
90s Mentor
25 views

7:54
Network Marketing Nedir, Neden Network Marketing, Network Marketing Gerçeği
musaduman
3 views

0:36
mandurah security system, home cctv security systems mandurah, cctv security systems mandurah, mandurah security systems, cctv system mandurah
lockdownse
1 views

39:52
Network Security | What is a network and reference model? | Great Learning
Great Learning
4.4K views
12:05
What is Network Security? | Types of Network Attacks | How these Attacks are done
Tech Guru Manjit
14.6K views

11:03
Unit 4 Asymmetric Key Algorithm ▶️Cryptography and Network Security #makaut #ai#cryptography#network
Makaut Smashers
85 views

3:14
lecture 5 classification of encryption technique in cryptography & network security #viral network
GainThroughIT
17 views

0:08
Read Bundle: Network Defense: Fundamentals and Protocols + Network Defense: Security Policy
Sbjorn
0 views
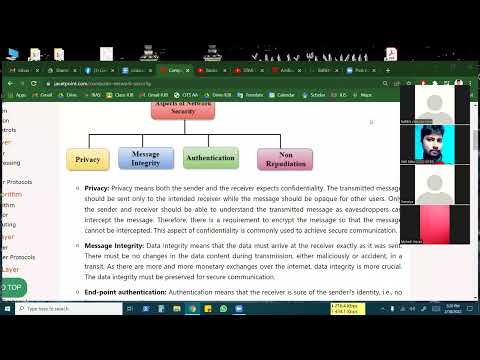
28:12
Computer Network & Lab | Network Security and Privacy | CSE | AKM Monzurul | University of Scholars
University of Scholars
12 views
8:59
Kerberos Protocol...Simplified Explanation
TechWithShas
406 views

11:39
Differences between Kerberos Version 4 and Version 5
not royal beast 2.5
13.5K views
29:52
Kerberos: Verstehen & Hacker Abwehren. Verteidige das Netzwerk vor Hacker-Angriffen!
ProSec
2.3K views

2:19
How Kerberos Works
Pravin Sonar
141.7K views
12:48
How Kerberos Authentication Works and Why You Should Use It Detailed Explanation in Telugu
Lucky Tech
7.7K views
13:41
Kerberos Version 5
Tech Classroom
53 views

16:52
Kerberos Authentication Explained | A deep dive
Destination Certification
424.5K views

4:51
Module 5: What is Kerberos?
Simple Security
46.8K views

1:01
What is Kerberos ? #cissptraining #cissp #cybersecurity #authentication #itsecurity #securityconcep
IT Tech Insights
5.6K views

8:58
Kerberos Explained Step by Step CISSP Domain 5 2025
Gagan (Gags) Singh CISSP
626 views

14:12
Kerberos Authentication
Mervin Pearce
57.5K views
20:25
INS: Unit-9 Remote User-Authentication (Kerberos)
Twinkal Patel
423 views
2:42
Kerberos
Udacity
86.7K views
8:19
Kerberos: Realm, Difference between Version 4 and 5 | CST409 | NSP MODULE 1 |KTU| Anna Thomas |SJCET
Anna Thomas
5.5K views