Search Results for "Which encryption type uses a SHARED key"
Find videos related to your search query. Browse through our collection of videos matching "Which encryption type uses a SHARED key". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Which encryption type uses a SHARED key"
50 results found

1:10
Magic Key Extractor Key Gen (Magic Key Extractormagic key extractor 2015)
Brenda Diaz
27 views

1:00
Key locksmith Dubai, key repairing, key making, key locksmith, locksmith Dubai
Ummeammarah11
2 views

0:48
°FIFA 14° °KEYGEN°°KEY GENERATOR°°ACTIVATION°°PRODUCT KEY°°SERIAL KEY°°LICENCE KEY
morientesmalaka
241 views
![Mirrakey License Key Generator Key Gen [Mirrakey License Key Generatormirrakey license key generator 2015]](/image/s2.dmcdn.net/v/8_ZGQ1e0GZW5oh8l_/xx720.pagespeed.ic.P1ZMrUV2OK.jpg)
1:50
Mirrakey License Key Generator Key Gen [Mirrakey License Key Generatormirrakey license key generator 2015]
Bob Sanderson
6 views

3:17
Best Key West Restaurants | Best Key West Nightclubs | Best Key West DJs | Whats Hot Key West
LJ Cange
1 views

6:43
Network & Cyber Security Lecture: Symmetric key Encryption (Private Key) Key Based Cryptography
Sanjay Pathak
1.8K views

26:08
(1) Public Key Encryption: DH key exchange and key generation in RSA
Rands
150 views

5:06
Public Key Encryption (Asymmetric Key Encryption)
Sunny Classroom
182.1K views

5:41
What is Cryptography in Sinhala | Symmetric Key Encryption and Asymmetric Key Encryption- Tearn
Tearn
154 views

3:17
A/L ICT 2016 MCQ 22 Sinhal | Asymmetric Key Encryption & Public Key Encryption Explained Sinhala
ICT Notes Hub
24 views

8:10
Types of Encryption | Symmetric Key and Asymmetric Key Encryption
A Z Computing
10.6K views

5:32
Symmetric Key vs Asymmetric Key encryption in Hindi / Urdu #RSA #DES #AES #Encryption #KeyExchange
An IT Learner
489 views

6:50
Encryption & types of Encryption./ Secret key and public key cryptography
KD tutorial
1.1K views

2:12
Symmetric Key Encryption vs. Public Key Encryption
The Security Buddy
156 views

6:57
Computer Network Security Public Key Encryption / Asymmetric Key Encryption in Hindi
DrMonika Varshney
758 views

8:45
Public Key Encryption Examples - The advantages of Public Key Encryption
Fullstack Academy
2.2K views

4:52
Private Key Encryption (Symmetric Key Encryption)
Sunny Classroom
137.4K views

2:14
Symmetric Encryption and Asymmetric Encryption|Public key cryptography vs Private key cryptography
Last Night Study
209 views

15:37
Digital Envelops | Encryption using Public key and Symmetric key Encryption Hindi Urdu (IT430)
theITeducation.com
568 views

9:27
What is Encryption? Symmetric Key and Public Key Encryption?
Glorious Frog
602 views

4:42
Public Key Encryption (PKE) in hindi | Public key encryption example | Digital Forensic
Zixplain
7.7K views

16:07
What is Encryption? | Public Key and Private Key? |End-to-End Encryption?Concept explain(in Hindi)
K A FAROOQUI
129 views

6:54
Symmetric Key Encryption and Asymmetric Key Encryption
Kaur Khalsa Classes
80 views

3:10
Public key Encryption (Asymmetric Key Encryption)
Myexamnote
40 views

0:36
Encryption and Encryption Key Explaineeddd !! 🔥🔥 #networks #encryption
Coding Adda
574 views

5:50
What is Encryption? Symmetric & Asymmetric Encryption? Public Key Encryption?
Chalo Seekho
66 views

14:02
Data Encryption | Symmetric Vs Asymmetric Encryption | Public-Private Key Encryption | Explained
Gourab Banerjee
292 views

19:38
Encryption||Decryption||Secret Key||Conventional encryption||Asymmetric Encryption
Shiksha Academic & Tutorials
277 views

34:32
Asymmetric Encryption | Public Key Encryption | RSA Encryption Algorithm | DSS | ECC | IS Lec 6
Techno Learn
378 views

1:11
What is Encryption? Explain Encryption, Define Encryption, Meaning of Encryption
Audioversity
261 views

0:22
Blood And Its Uses : What happens if someone is given the wrong blood type?
VideojugHealthWellbeing
1 views

5:13
Corcodile meat and skin uses ,,in which countries corcodile farming is a business
Cosmic
6 views

2:34
A boy in lahore makes bike which not uses petrol
Rasalaa Official
2 views

0:34
Straight Talk uses Verizon and AT&T’s network which is what Misty appreciates.
333quivertree
1 views

5:25
Auto Key Cipher : Type of Encryption Decryption Method | Poly-alphabetic Substitution Cryptography
Quick Trixx
43.9K views

2:21
What is Encryption? Example, Symmetric Cryptographic, and Type of Encryption? #commercecrazehub
Commerce Craze Hub
228 views

3:01
276 Historical Uses of Symmetric Cryptography GÇö Running Key and Concealment
Rezky Wulandari
1.8K views

27:46
CYSAT 2025 – Post-Quantum Cryptography: Key challenges and uses for embedded systems and satellites.
CYSAT
157 views

1:01
How Your Key Fob Uses Radio Waves and Cryptography #howitworks #facts #mindblown
How it Works?
102 views

0:58
What is Quantum key distribution | DRDO uses QKD technology #Shorts
GLOBAL Updates
1.5K views

2:53
Recology Uses Analytics to Create a Cleaner Future with Key Info
Keyinfo
18 views
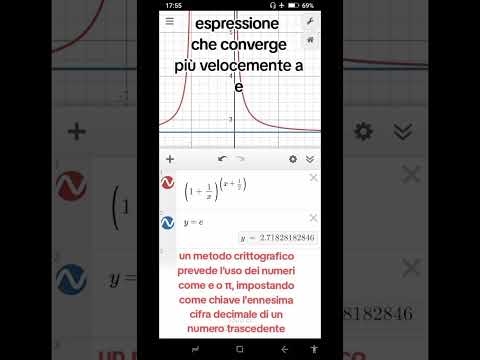
0:09
a cryptographic method uses transcendental numbers, setting the nth decimal digit as the key
La Raccolta
134 views

1:39
Danish brewery uses recycled human pee as one of the key ingredients in its craft beer
Mashable
4 views

0:12
Asymmetric encryption uses two keys
Next Gen Synthetix
64 views

0:50
Encryption Basics: Types, Uses, and Benefits | Abc Hack Tech
Abc Hack Tech
176 views

0:56
“Asymmetric encryption 🔐 uses a pair of keys—public 🗝️ and private 🔑 #coding #linuxcommands
gst_software
68 views

9:50
Modular Athematic | uses in Classical Encryption Techniques | Cryptography | Chapter 2 | Lecture 14
Koncept Recall
6 views
0:41
How WhatsApp uses end-to-end encryption to keep your messages secure #shorts #programming #coding
Tom Shaw
7.0K views

8:29
Symmetric vs Asymmetric Encryption Differences and Uses
CyberMindz
13 views

3:59
"Game Over" - 90s OldSchool Type Beat | Underground Hip-Hop Boom Bap Type Beat | Anabolic Beatz
Anabolic Beatz
14.4M views
Previous Page 2