Search Results for "hmac method"
Find videos related to your search query. Browse through our collection of videos matching "hmac method". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "hmac method"
50 results found
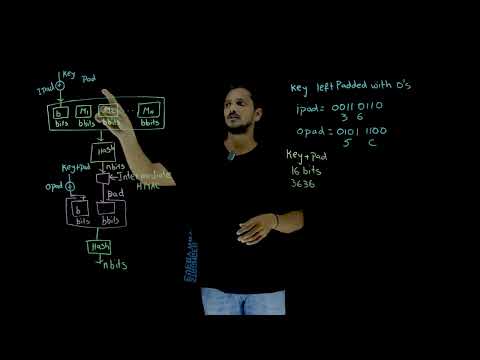
5:15
HMAC Nested MAC Method || Lesson 73 || Cryptography || Learning Monkey||
Wisdomers - Computer Science and Engineering
1.1K views

20:32
Bisection method numerical analysis in hindi | Bisection method to find roots | Bisection Method
Mechanical in Hindi
41 views

1:15:07
Lecture 25: MAC (Message Authentication Codes) and HMAC by Christof Paar
Introduction to Cryptography by Christof Paar
63.8K views
7:24
Data Integrity - How Hashing is used to ensure data isn't modified - HMAC - Cryptography
Practical Networking
77.9K views
7:05
HMAC - Cryptography I
Nguyen Duong Anh
80 views

11:03
Learn the ART of CRYPTOGRAPHY - SHA-1 HMAC Hashing Explained (Urdu/Hindi)
Cybersecurity Academy - CertificationHUB
184 views

6:52
MAC / HMAC - Message Authentication Code / Hash Bashed Message Authentication Codes
Practical Networking
30.0K views

8:10
#36 HMAC (Hash Based) & CMAC (Cipher Based) |CNS|
Trouble- Free
232.6K views
22:00
CNS HMAC
Kallam Gopala Reddy
312 views

9:00
HMAC and CMAC in Cryptography Hash Function || Network Security in Telugu
Lab Mug
10.9K views

9:24
Securing Stream Ciphers (HMAC) - Computerphile
Computerphile
326.5K views
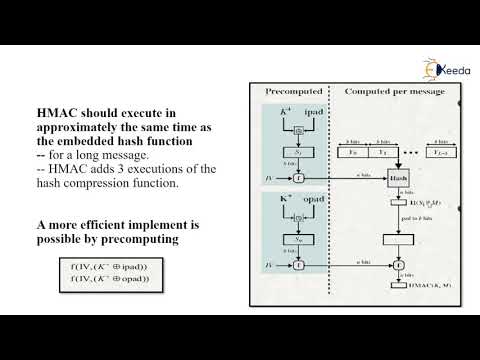
20:35
HMAC | Cryptography and Network Security
Ekeeda
677 views
1:09:59
Go UUID HMAC
Learn To Code
945 views

10:26
Razorpay integration in asp.net web app | HMac SHA256 signature create and matching
New Arts
1.4K views

0:46
HMAC Promo take 2
Players 2Pros
29 views

12:48
Função de Hash - MD5 e SHA - Código HMAC - Aula completa
Prof. Sergio Villarreal
3.7K views
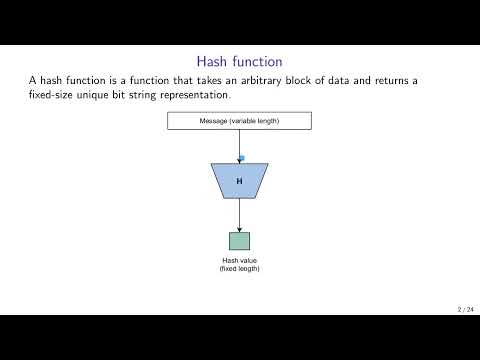
57:46
Applied Cryptography: 3. Hash functions and HMAC
Applied Cryptography by University of Tartu
635 views
20:58
16-HMAC Algorithm Explained 🔐 | Hash-Based Message Authentication Code in Network Security
Sundeep Saradhi Kanthety
168.4K views
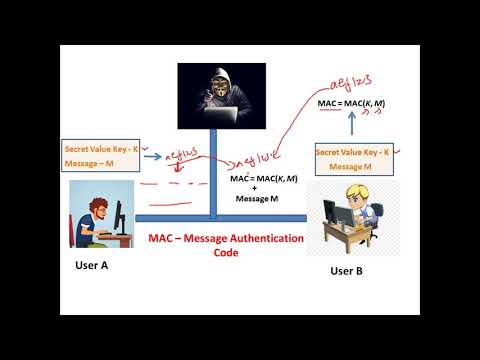
29:42
Message Authentication Code (MAC) and HMAC - Cryptography - Cyber Security CSE4003
Satish C J
37.3K views
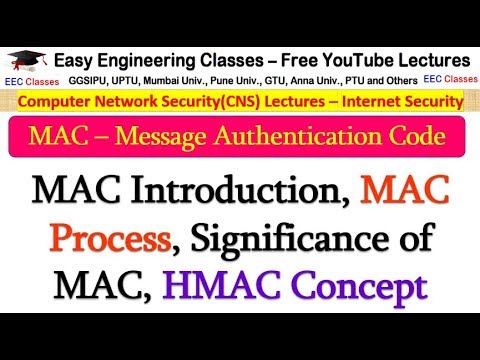
8:08
MAC in Hindi - Message Authentication Code Process, Significance, HMAC Concept
Easy Engineering Classes
111.9K views

13:49
V4b: CBC-MAC and HMAC (Applied Cryptography 101)
Cryptography 101
1.1K views
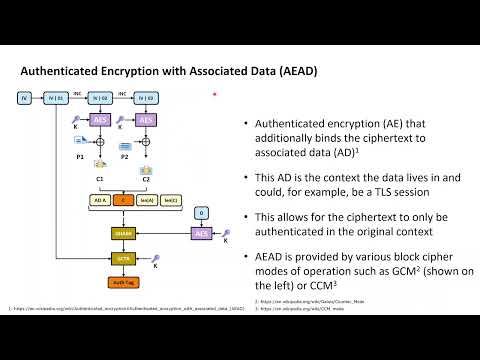
12:51
Cryptography with Python 30: HMAC, Encrypt-then-MAC and GCM
Cyrill Gössi
1.1K views

11:19
MAC function ,HMAC,CMAC in Cryptography and cyber security tamil||CCS||Anna university reg-2021.
Murugan Tech World
7.8K views

6:09
HMAC & Message Authentication Codes (MACs) - Why Hashing alone is NOT ENOUGH for data integrity
JayPMedia
6.7K views

9:40
Message Authentication Codes: CMAC and HMAC
Cihangir Tezcan
4.8K views
6:33
HMAC explained | keyed hash message authentication code
Jan Goebel
85.3K views

7:40
MAC Based on Hash Function | HMAC in network security
Chirag Bhalodia
67.7K views

1:34
How to find a boyfriend Drama Method Review Scam Alert - Drama Method review
Teddylonger79
47 views

1:26
The Drama Method The Drama Method Review
Dorethea4sf
1 views

1:26
The Drama Method The Drama Method Review
Jenifferovy
1 views

2:30
The Drama Method Reviews - Drama Method
Shawnnarsa
1 views

2:27
The Drama Method | The Drama Method-The Emotional Hook Formulas
Marvel0iq
1 views

1:26
The Drama Method | The Drama Method Review
Felicitasa3u
0 views
![drama method relationships | Drama Method [Discount link here]](/image/s1.dmcdn.net/v/DSNUJ1e9M4zhlmAR4/xx720.pagespeed.ic.PFwUrpWpL0.jpg)
2:04
drama method relationships | Drama Method [Discount link here]
Delphineu1c
0 views
2:49
Drama Method - The Real ""Drama Method"" Review
Juneayw
1 views
![drama method reviews | Drama Method [Discount link here]](/image/s2.dmcdn.net/v/DTLAH1e0Z_OiYye5d/xx720.pagespeed.ic.PFwUrpWpL0.jpg)
2:04
drama method reviews | Drama Method [Discount link here]
Marjorieei0
0 views

1:27
Download The Drama Method Aaron Fox Pdf - What Is The Drama Method
Penelopefnz
3 views

1:09
Drama Method PDF - Get Access To Drama Method PDF Now!
Carita53k
3 views

0:19
Read How to Solve It: A New Aspect of Mathematical Method: A New Aspect of Mathematical Method
Nando Patulopol
5 views

4:31
How to Apply RGPV degree in offline method OR Online method|| मात्र 15दिन मैं डिग्री कैसे लाए..?
Humsafar Shubham
17.6K views

0:06
Grouping method #grouping #method #statistics #micro #macro #class11 #rkmclasses #rkmclassesonline
RKM CLASSES
5.2K views

8:25
TUBE METHOD/ABO GROUPING METHOD /PART 3 / ABO GROUP SYSTEM/ PART 7
LAB TECH CLASSROOM by VMG
5.3K views

0:45
Forward and reverse blood grouping method. How to prepare cell suspension for reverse method? Next
Pathofied Mindful tips
2.5K views

9:30
Introduction to Greedy Method || General Method || Control Abstraction || Applications || DAA
Sudhakar Atchala
62.3K views
6:14
google adsense loading method | google adsense loading method 2024 | Google Adscence #baqgamers
Gadget Explorer
355 views

3:44
S.T.A.R vs C.A.R interview method - Best interview method/technique
CareerShakers
8.6K views

9:41
Install Kali linux Nethunter on Android Device ( No Root) | Install kali nethunter offline method
H3NRY TECH
1.3K views

19:15
Hash Functions in hashing, Hashing in data structures, Types of hash functions, division method
CSIT Tutorials by KanyaKumari
4.5K views

0:40
She's A Method Actor - Bryan Cranston To Anna Gunn | Breaking Bad Commentary Funny Ep101 - Pilot
Movies Flicker
588.4K views

9:56
Cesar Cryptography method in daily life
PRAJAPATI SACHINKUMAR VINODBHAI
36 views